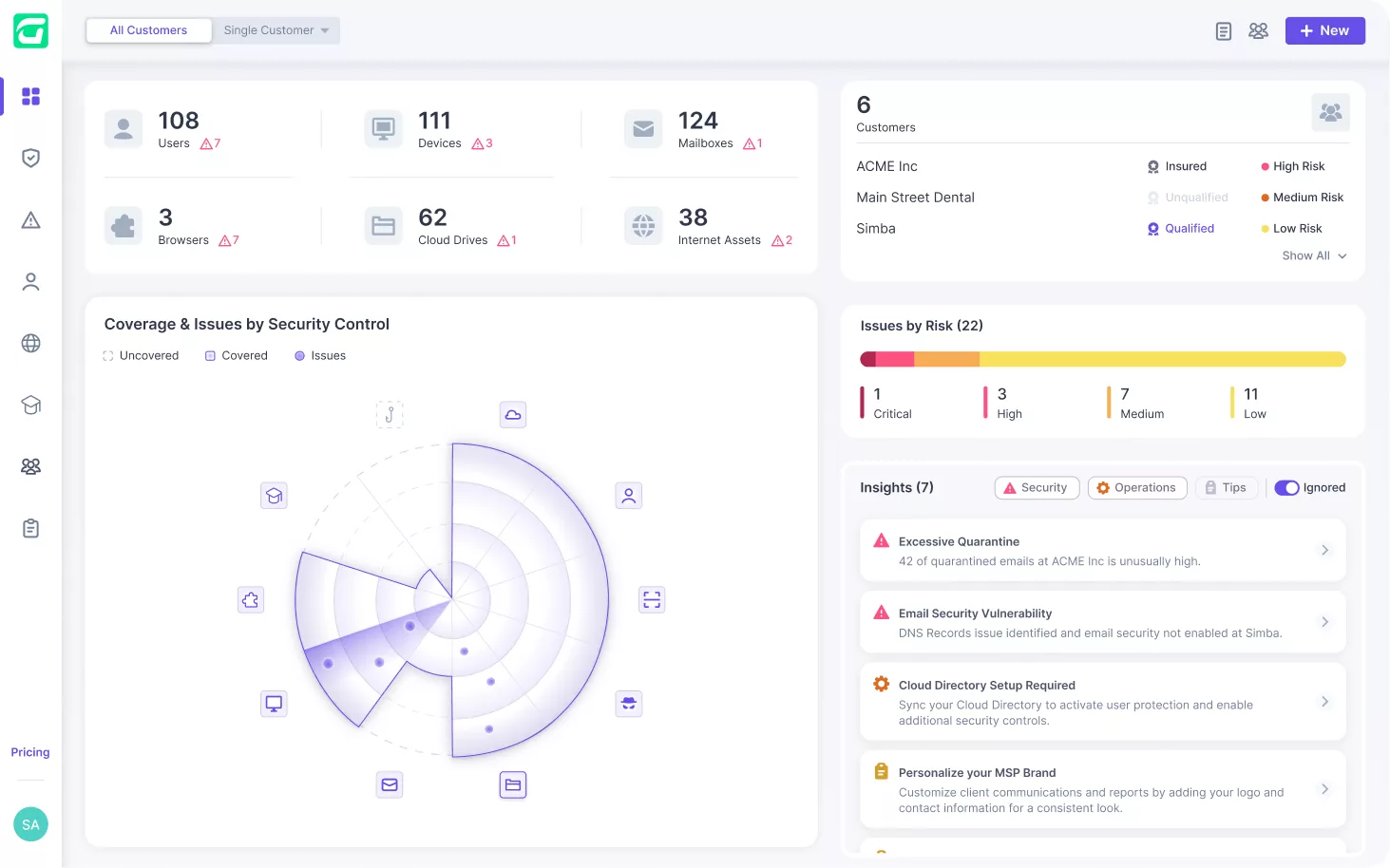

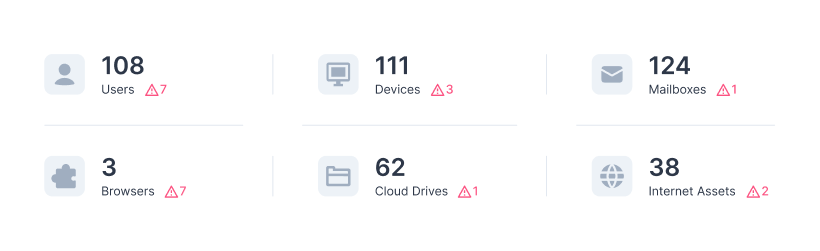
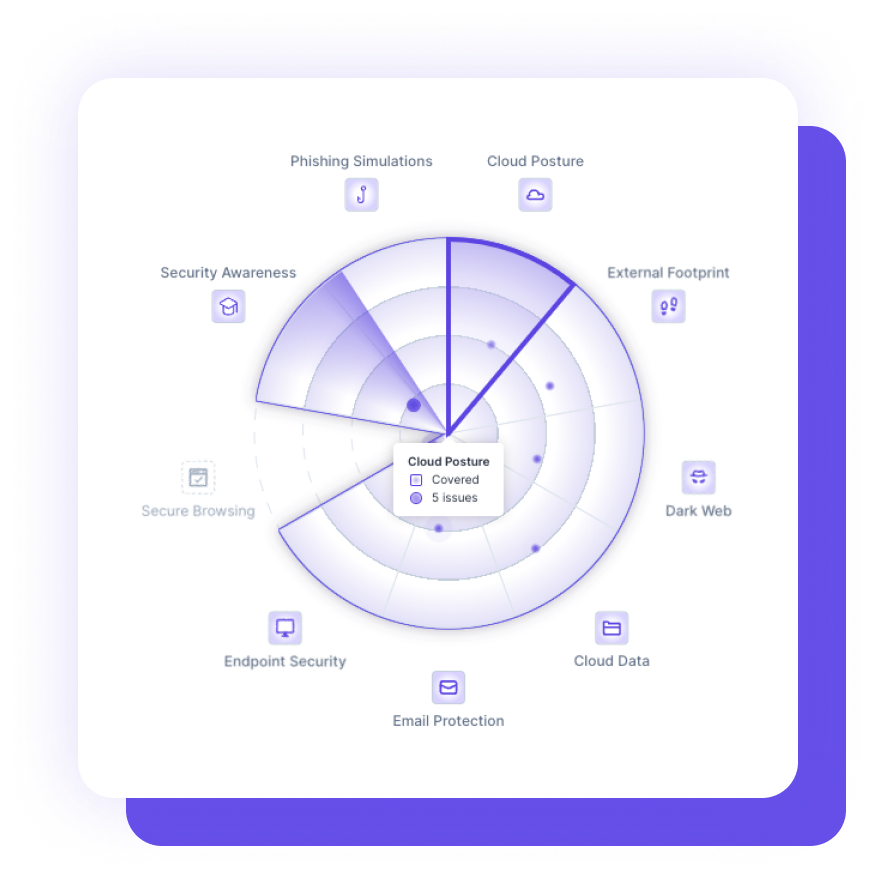
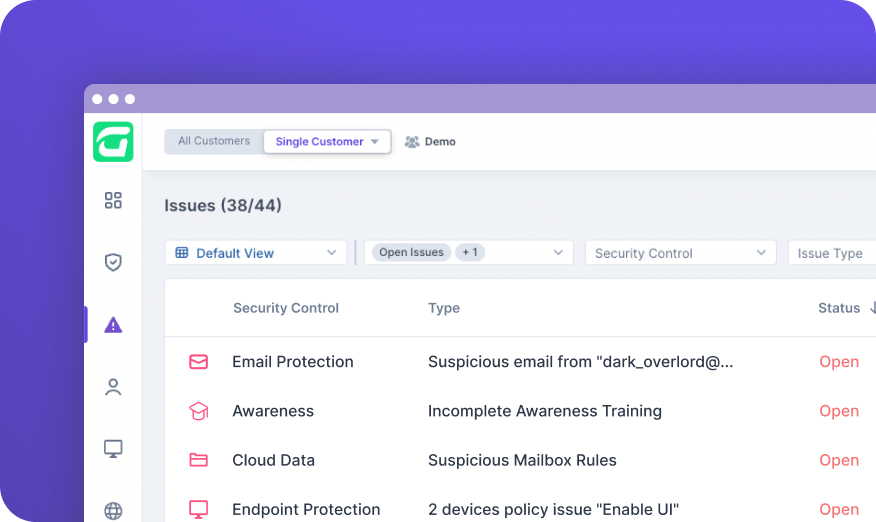
Guardz automatically discovers and monitors all your customers’ digital assets. Drill down to see more details and discover related issues.
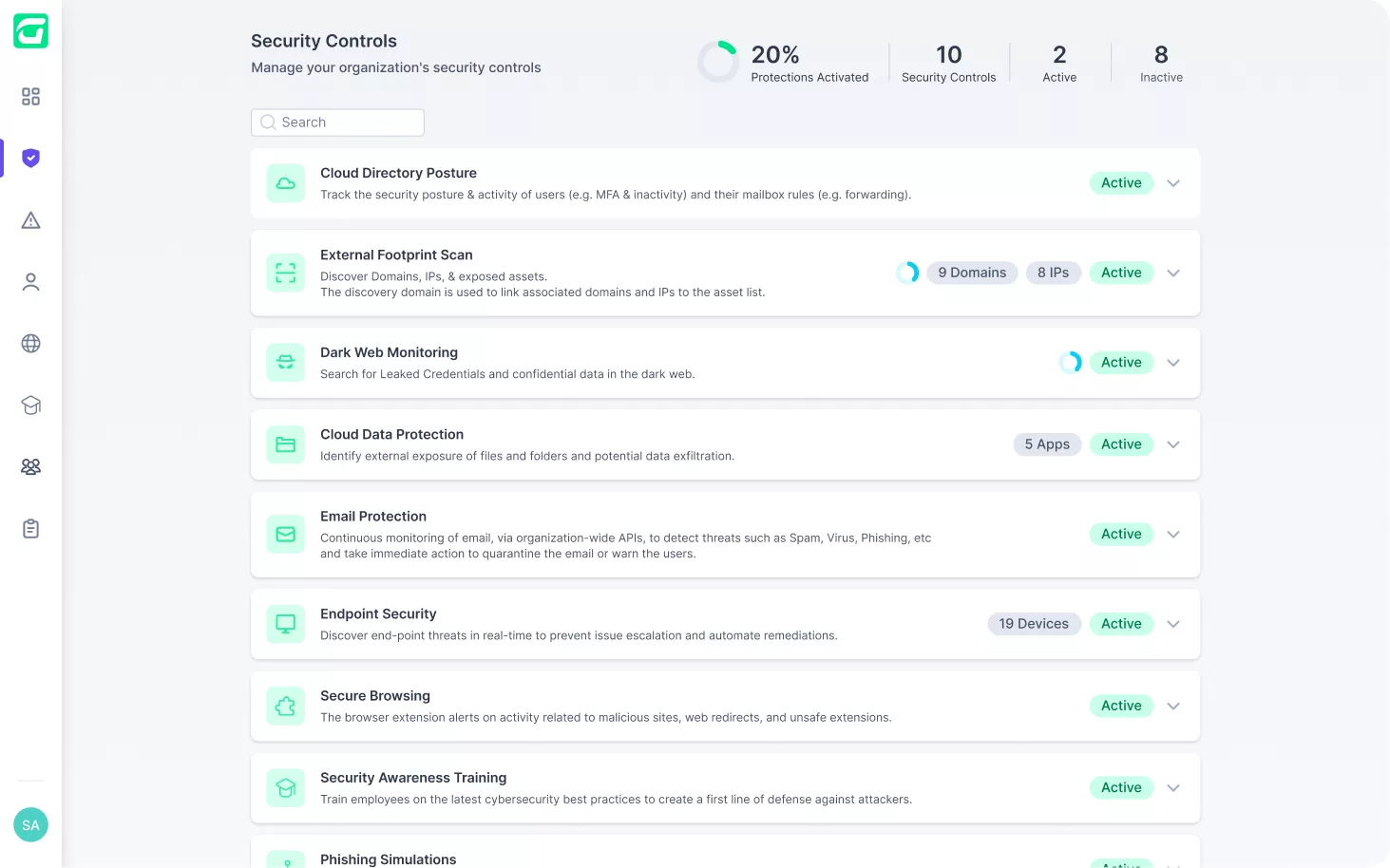
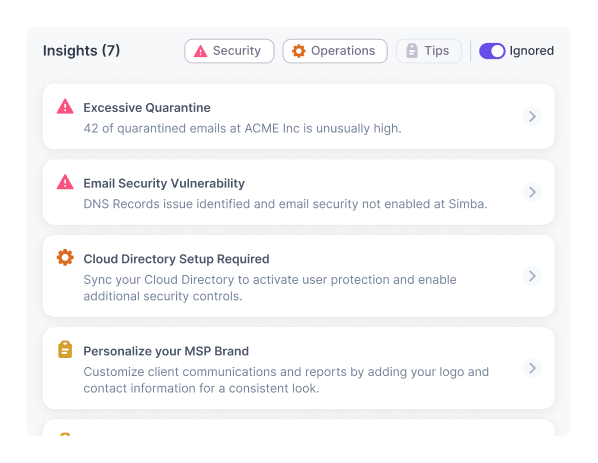
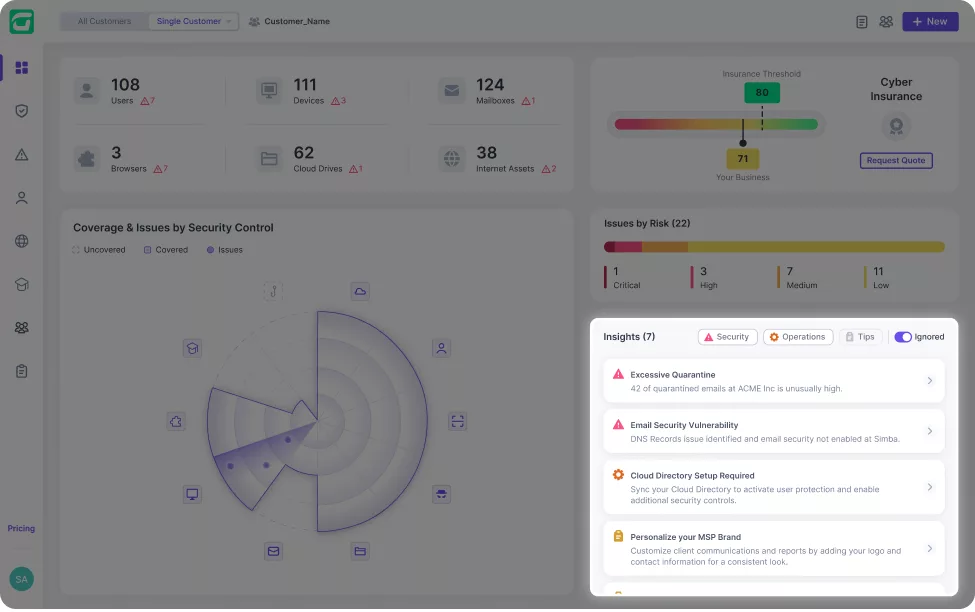
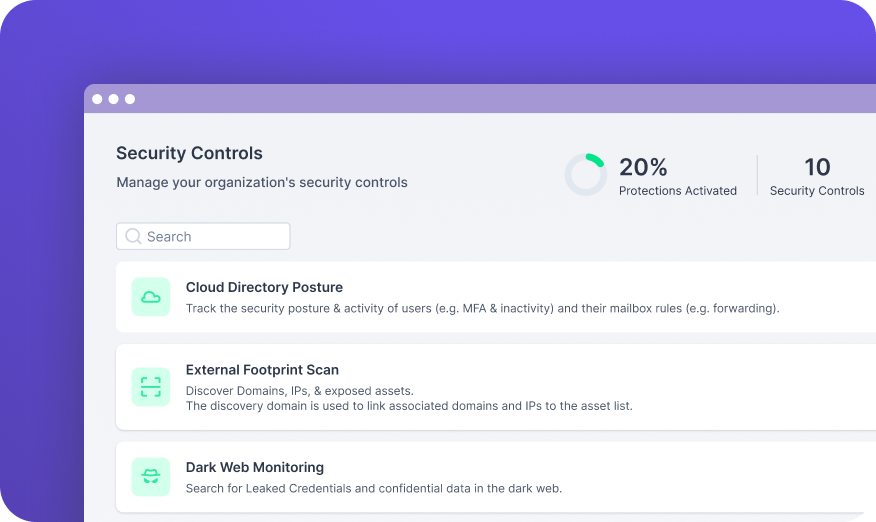
Guardz provides the security controls and coverage across your customers and detects issues in real-time.

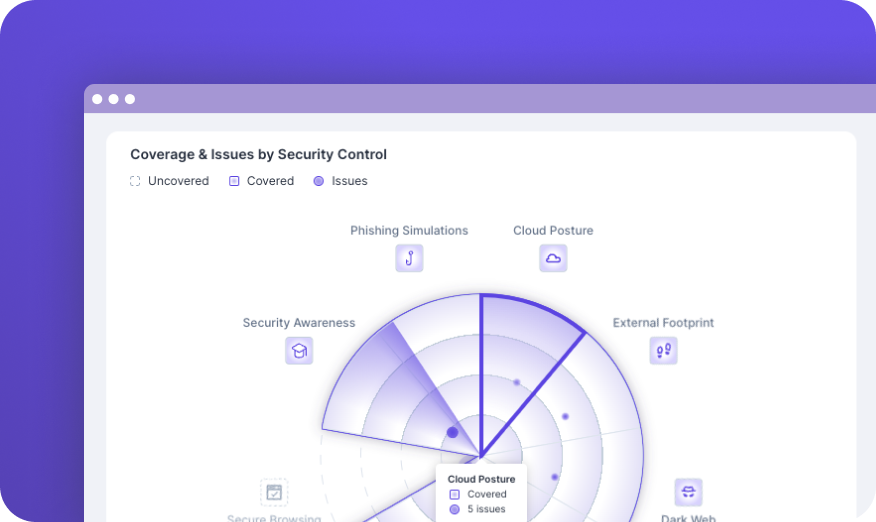
Get all the security controls needed to fortify your client’s cyber posture.
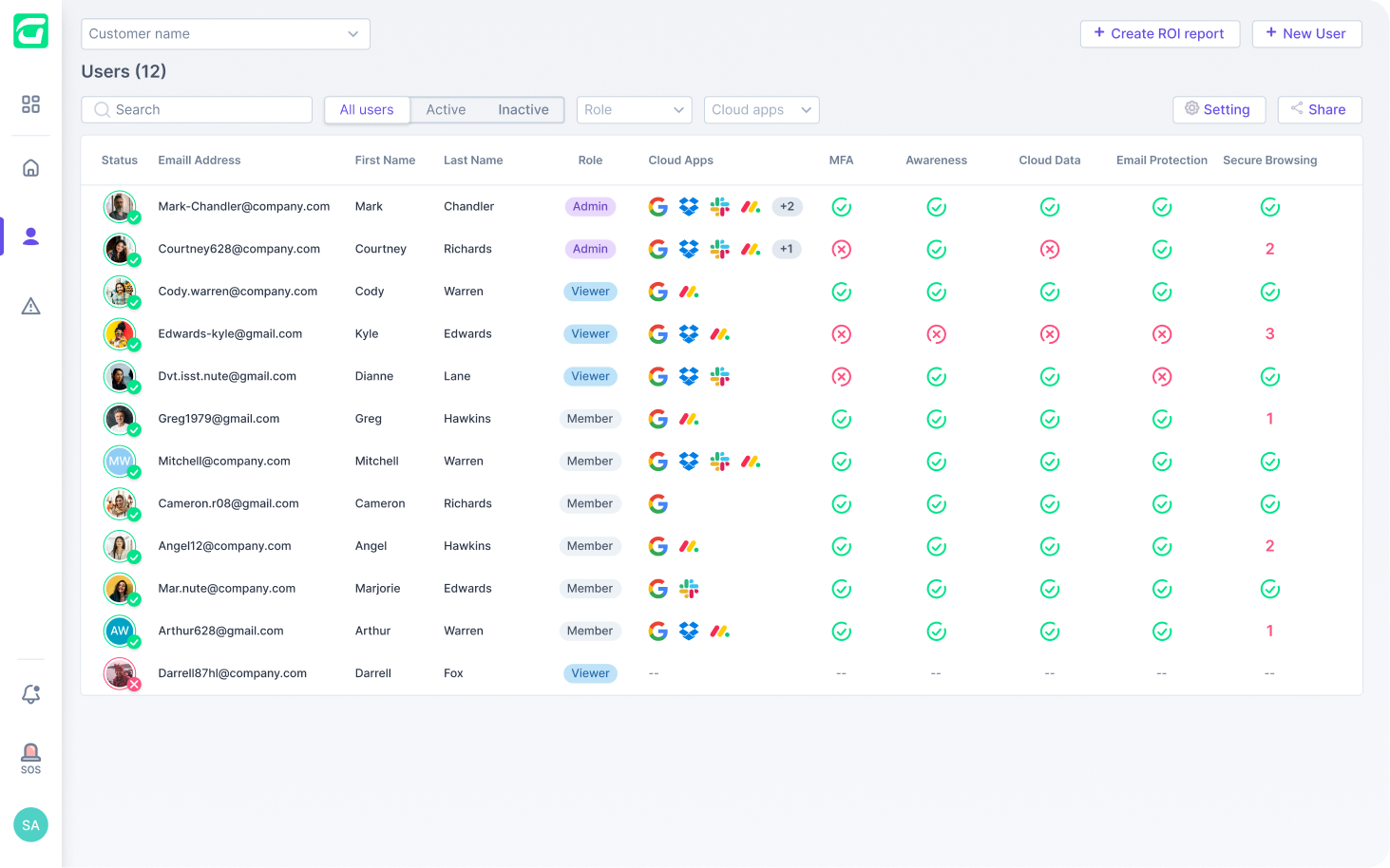
Real-time protection of all business employees across all applications, devices, and communication channels.
Connect the dots across detections and swiftly remediate, regardless of the attack vector.
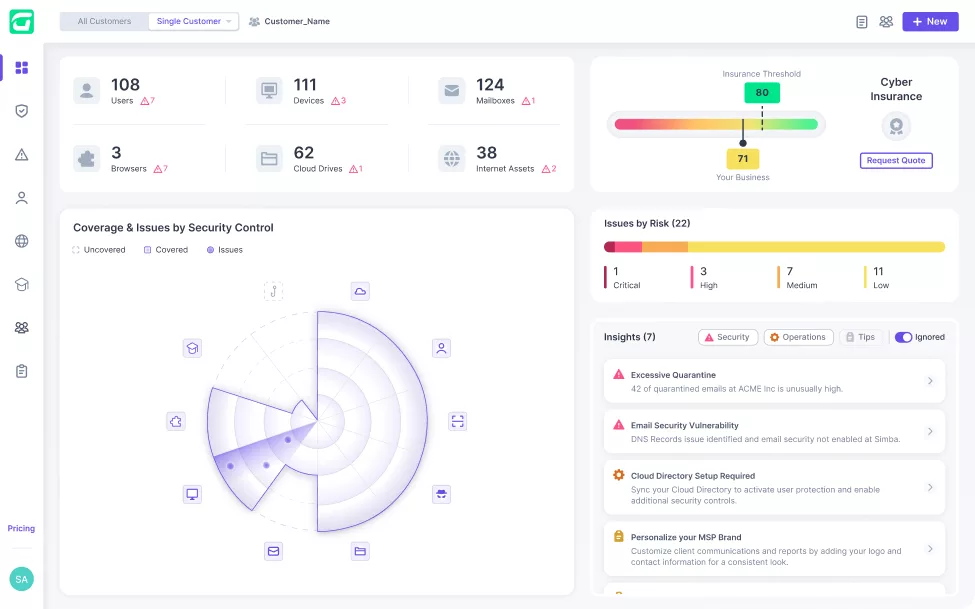
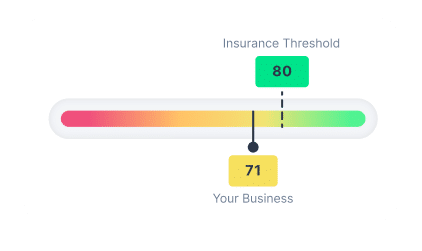
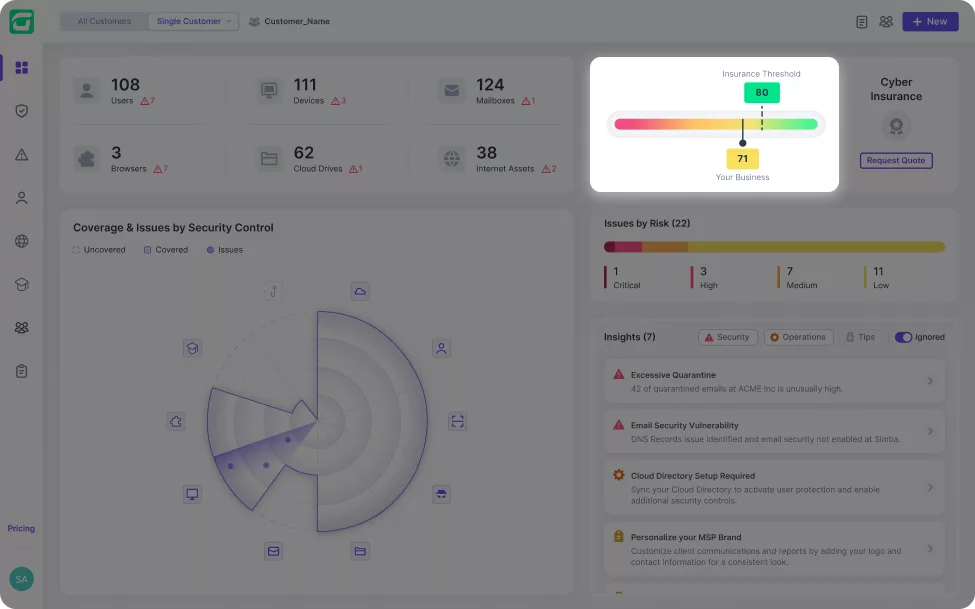
Real-time cybersecurity posture score that reflects the cyber risk and remediation progress.
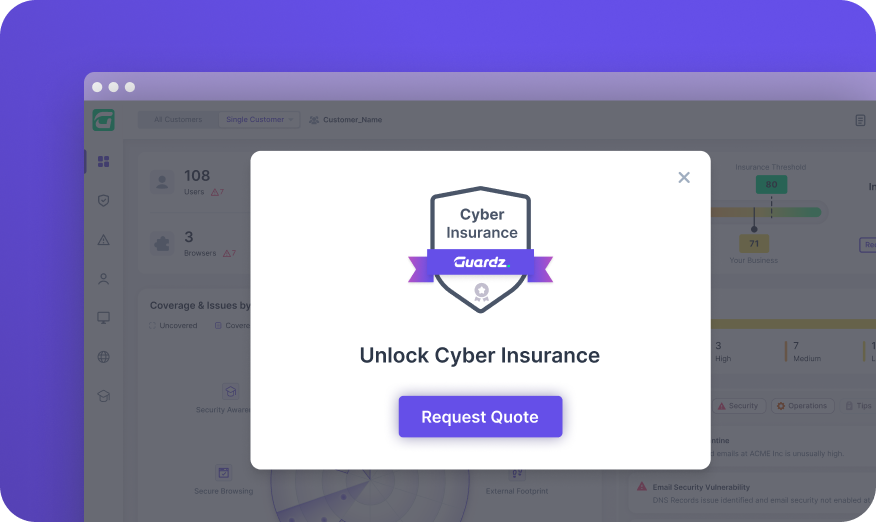
Get the coverage you need at the right price based on your client’s posture.

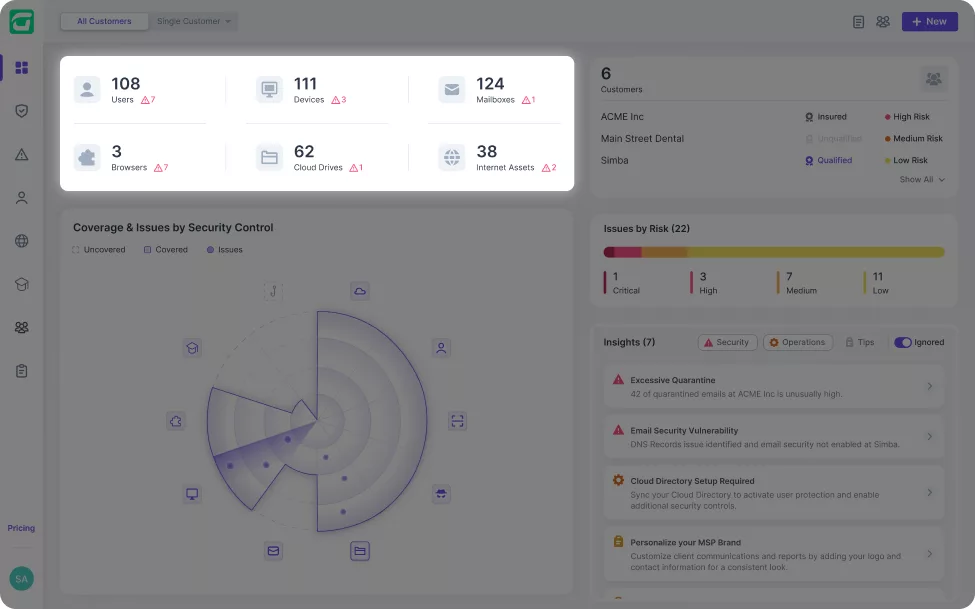

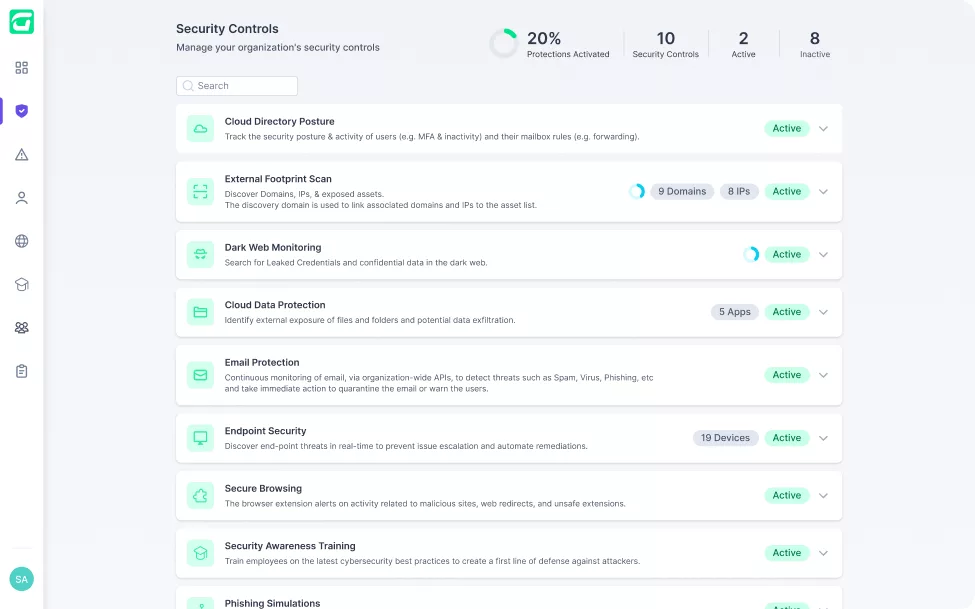
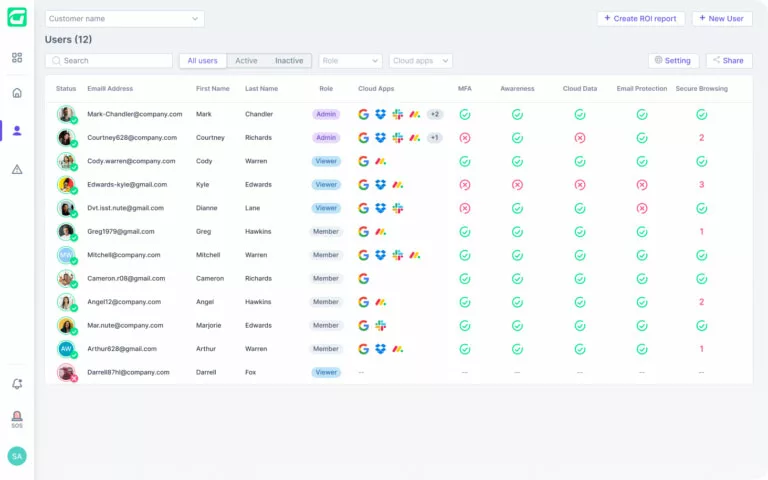
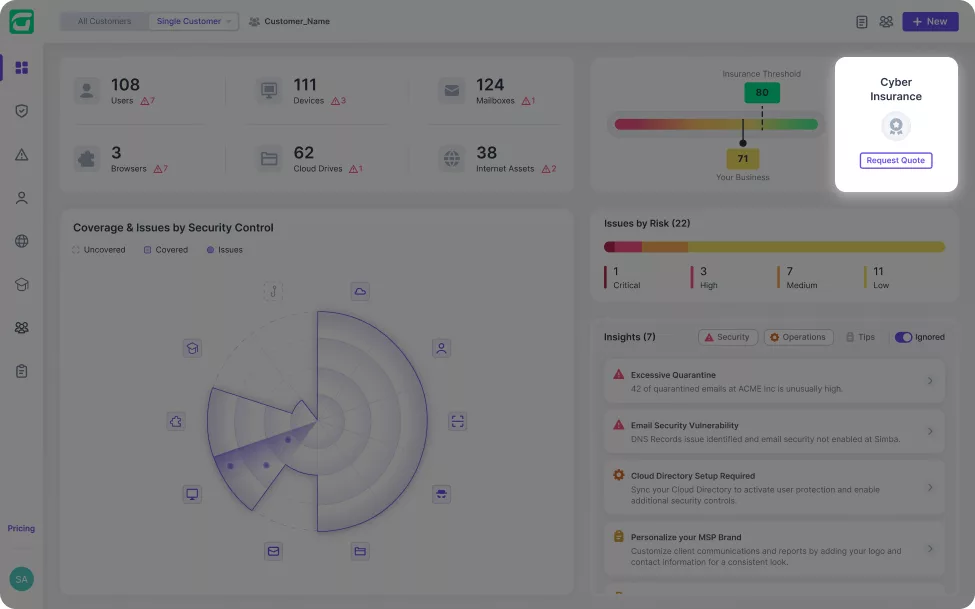

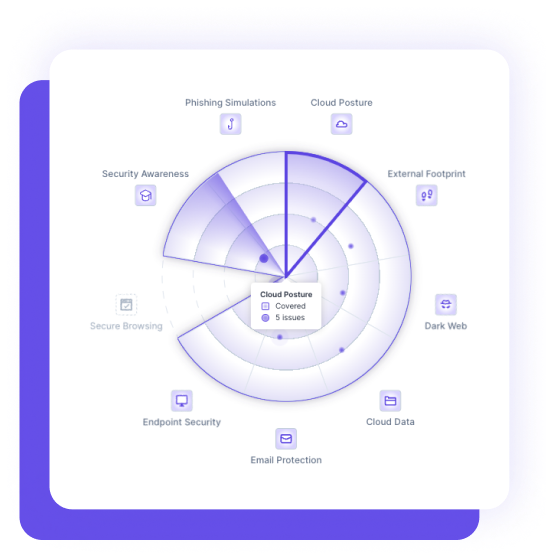
Guardz automatically discovers and monitors all your customers’ digital assets. Drill down to see more details and discover related issues.
Guardz provides the security controls
and coverage across your customers and detects issues in real-time.
Real-time protection of all business employees across all applications, devices, and communication channels.
Connect the dots across detections and swiftly remediate, regardless of the attack vector.
Get the coverage that you need at the right price based on your clients’ posture.













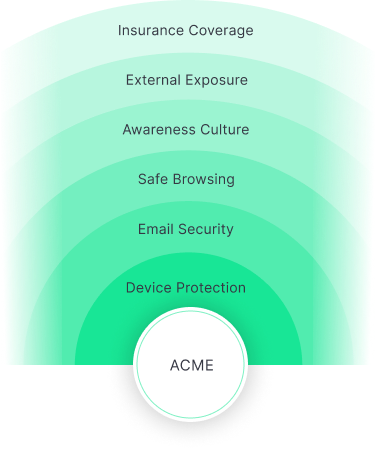
By combining robust cybersecurity technology and deep insurance expertise, Guardz ensures that security measures are consistently monitored, managed, and optimized to prevent the next attack and mitigate the risk. Guardz empowers MSPs to holistically secure and insure SMEs from the inside out.


Quick and easy activation for real-time protection of internal and external digital assets with an accurate risk score and remediation plan.
An insurance premium is calculated that is uniquely tailored to the business needs according to the risk score, ensuring optimal cyber coverage.
Guardz MDR integrates cybersecurity technology with insurance coverage in a unified native solution for end-to-end protection.
With a 4.9/5 rating, experience the confidence of choosing Guardz, a holistic cybersecurity solution built to empower MSPs to secure and insure SMEs. We’ve earned the trust of our customers through unwavering dedication to providing holistic protection.











Navigating the digital landscape brings various challenges for MSPs, from differentiating amongst competition, juggling multiple vendors to demonstrating customer value. On top of tackling these business obstacles, the primary objective has become the defense against advanced cyber threats to keep their clients secure. MSPs are more than just service providers; they’re the gatekeepers of digital assets.




Guardz takes enterprise-grade technology and simplifies securing systems and data with an intuitive and unified interface along with automated tools that detect, prevent, and respond to cyber threats seamlessly.
Guardz combines vital security tools
and partner enablement within a single platform tailored to fit your specific budget and requirements. This offers an effective and cost-efficient approach to managing cyber risks and growing your business without incurring excessive costs.

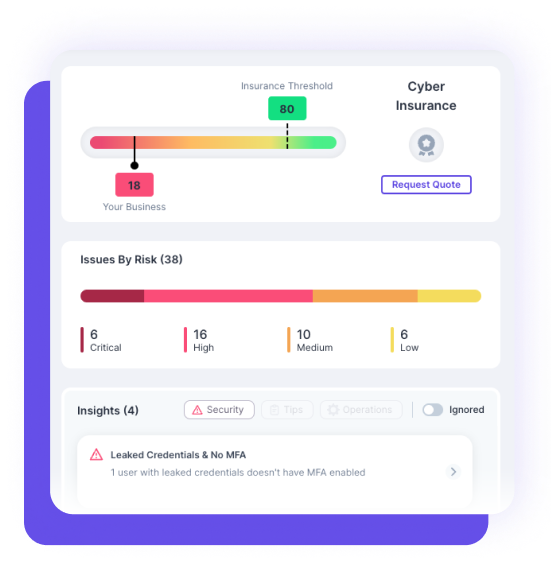
Guardz facilitates the adoption of cyber incident protection insurance to mitigate the financial risk associated with cyberattacks, data breaches, phishing, ransomware attacks and other cyber threats by ensuring insurance readiness and access to sufficient coverage.
Stay ahead of potential email threats by leveraging a user-friendly API-based email security solution.
Enable cloud data protection to achieve a safe and secure data collaboration with external users
Equip employees to be the first line of defense against the evolving landscape of cyber threats
Gain actionable insights on external threats by scanning digital footprint and exposed vulnerabilities
Protect laptops, and desktops from cyber threats such as malware, and ransomware
Keep your browser secure with the Guardz extension for protection against viruses and malicious sites
Continually simulating cyber attacks like phishing emails to highlight weak spots
Transfer the cyber risk associated with evolving cyber threats with tailored coverage at the right price
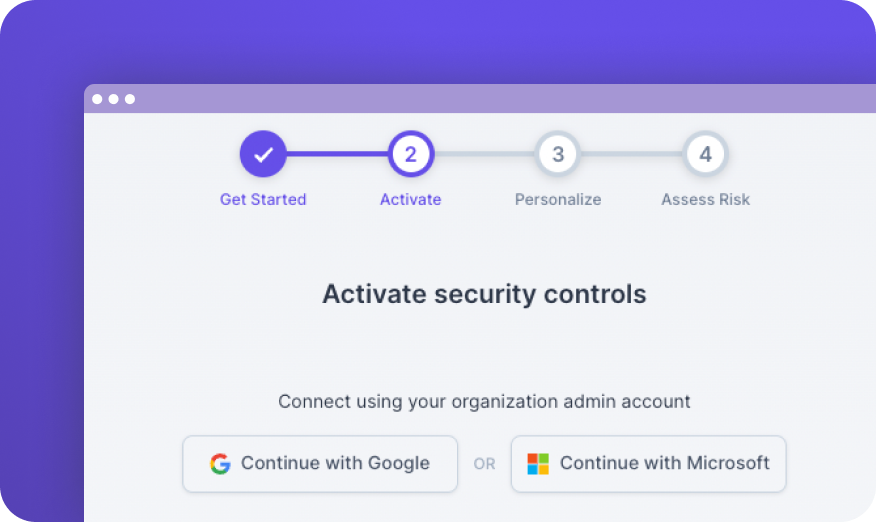
Onboard with your Google Workspace or Microsoft 365 business account to start monitoring your security posture.
Grant permissions to start active threat analysis and remediation plans.
Guardz continuously monitors for external exposure on the dark web as well as scanning your internal assets and cloud apps to identify vectors of risk.
Based on high-risk threats, Guardz promptly alerts administrators of urgent issues and guides resolution through manual and automated remediation.
Guardz ensures that you check all the boxes for insurance readiness and have access to an affordable, tailored coverage plan.





Support Teams Located in
USA & EMEA

Cyber Expert
Available 24/7

Contact Us
+1-972-587-7005
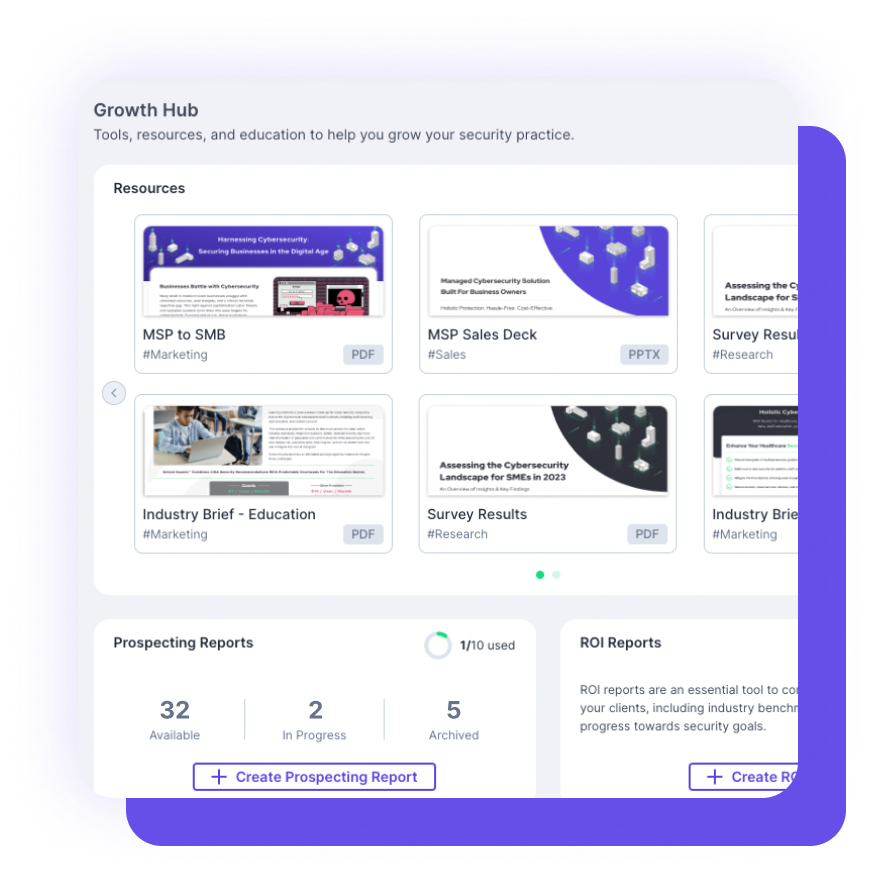
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


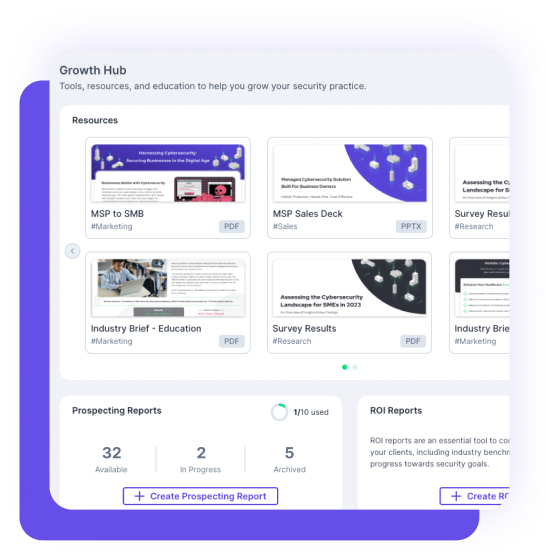
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

