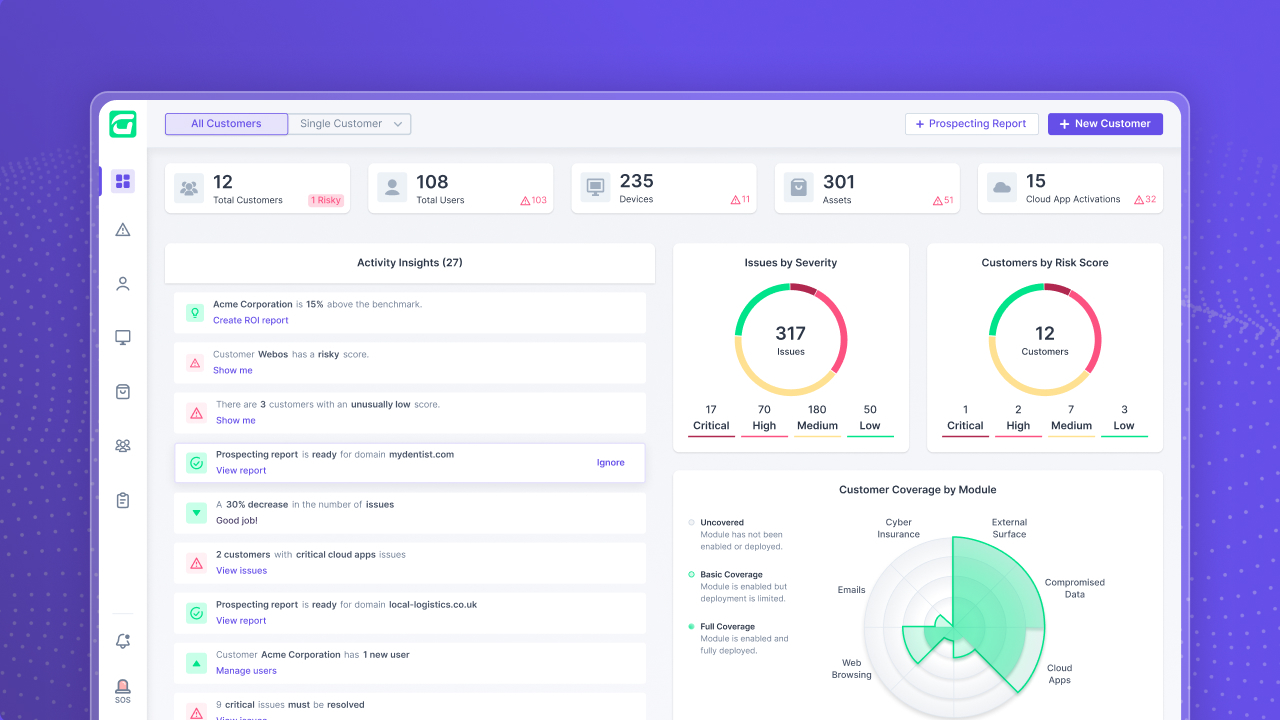
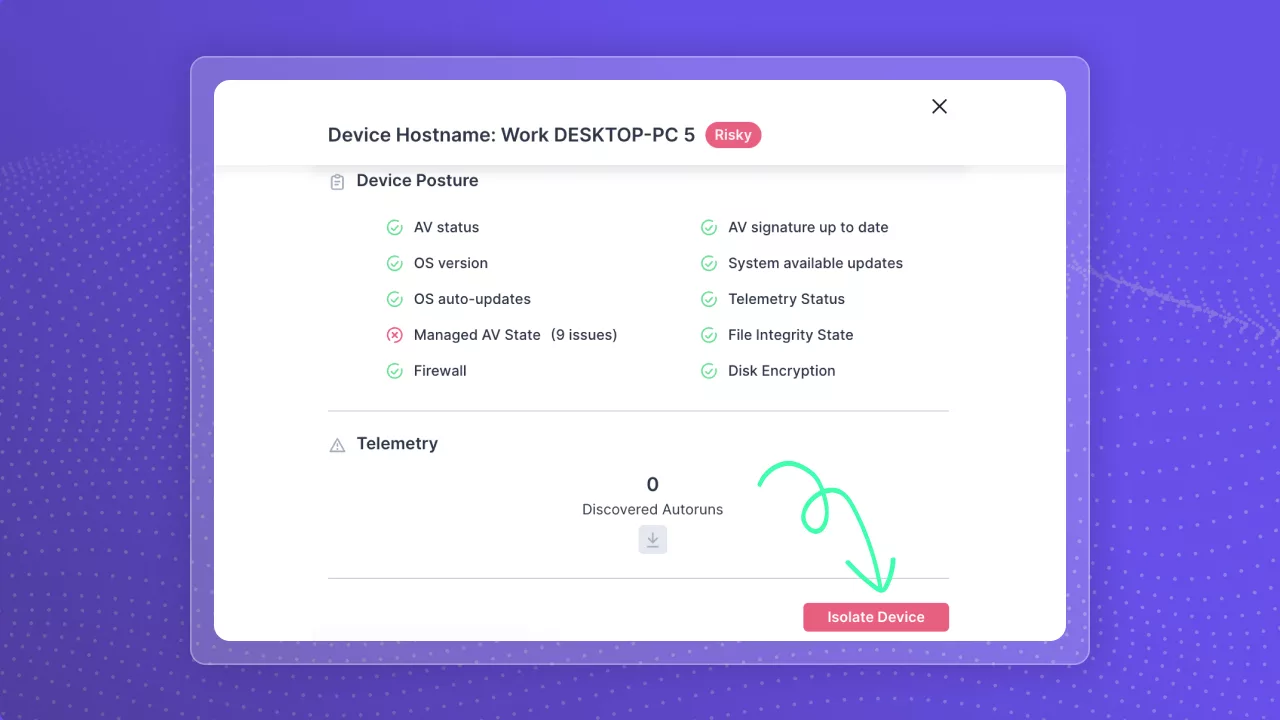
As we strive to ensure that Guardz is solving the most pressing challenges within the ever-evolving security landscape, we listen closely to our partners and are proud to announce the latest product updates implemented over the past few weeks.
Check out what’s in store:
Email Quarantine
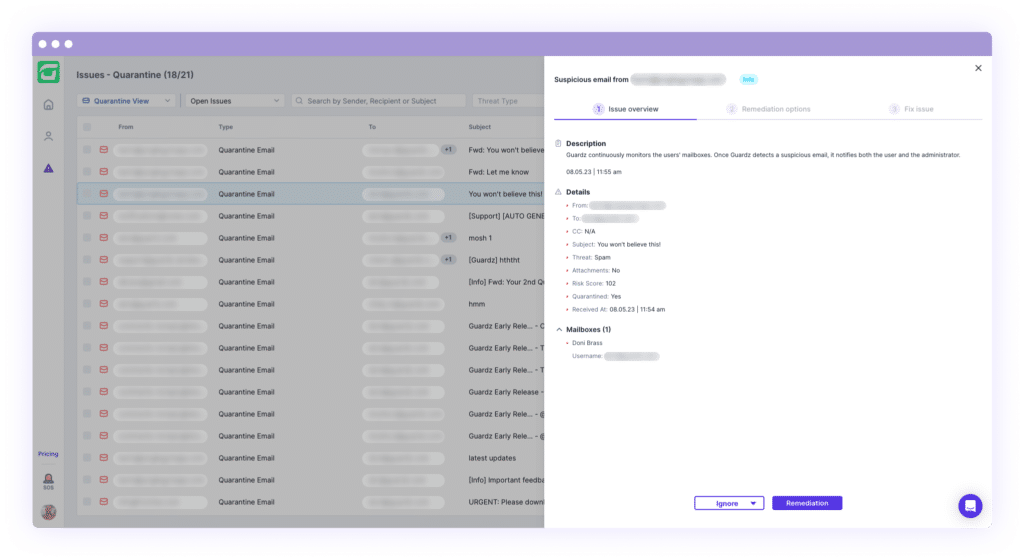
Manually managing every email issue that comes into your organization requires a considerable amount of effort to differentiate between legitimate emails and those that could potentially compromise your systems, and the consequences of a single misstep can be devastating.
With our new Email Quarantine feature, you no longer have to worry about manually sifting through issues, and you can now manage your email security risk at scale. The automated quarantine capability keeps employee inboxes safe while giving them an opportunity to manually review when required. Since emails are automatically deleted after 30 days, no further action is required by the employee or admin.
Data Protection – Google & Microsoft
Google Drive, along with Microsoft SharePoint and OneDrive, grant users the remarkable capacity and ease to collaborate on documents, presentations, and essential business content, but what potential risks come with these functionalities? If a user intentionally or unintentionally shares a document with external users or via a public link, hackers can exploit these security gaps to exfiltrate valuable data, compromising the organization’s privacy and security.
With the newly launched data protection for cloud applications, we now automatically and regularly scan the permissions of every file and folder across your entire organization. When assets are shared with external/guest users or even exposed via a public link, Guardz alerts the admins and enables visibility over the exposed assets.
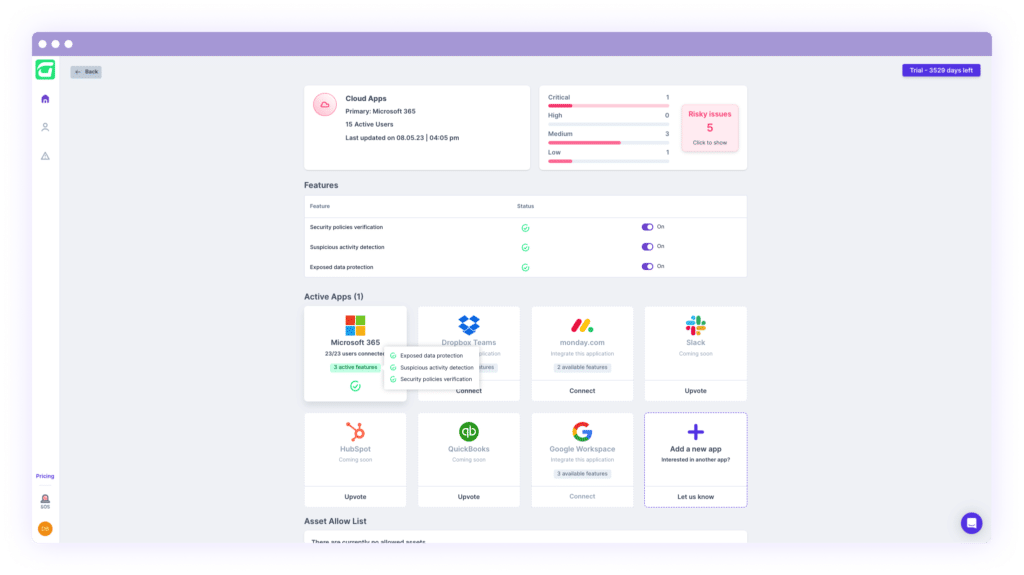
Once an admin identifies data exposure that needs to be resolved, remediation actions are given to do so automatically and manually as required.
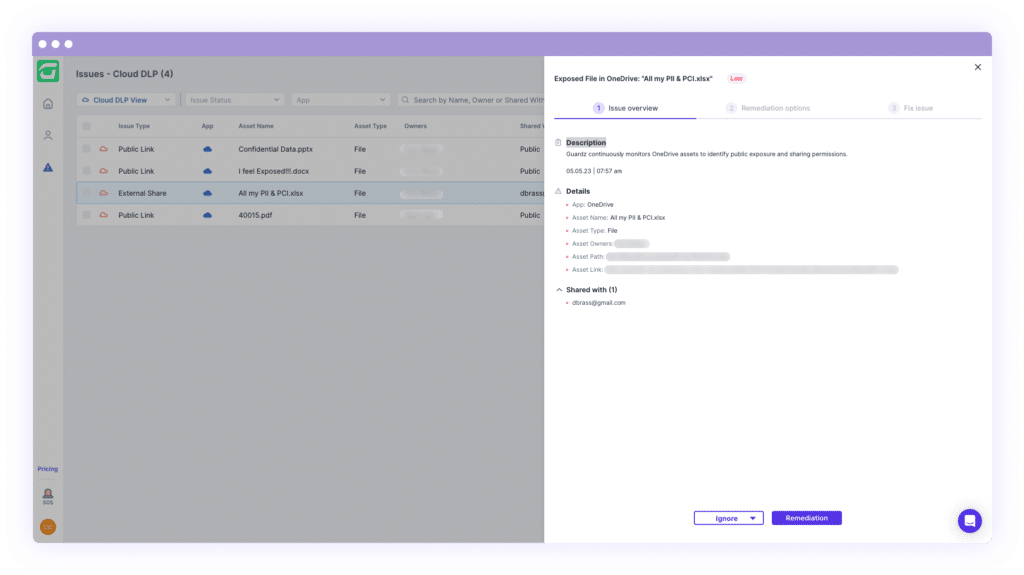
Table Views & Bulk Actions
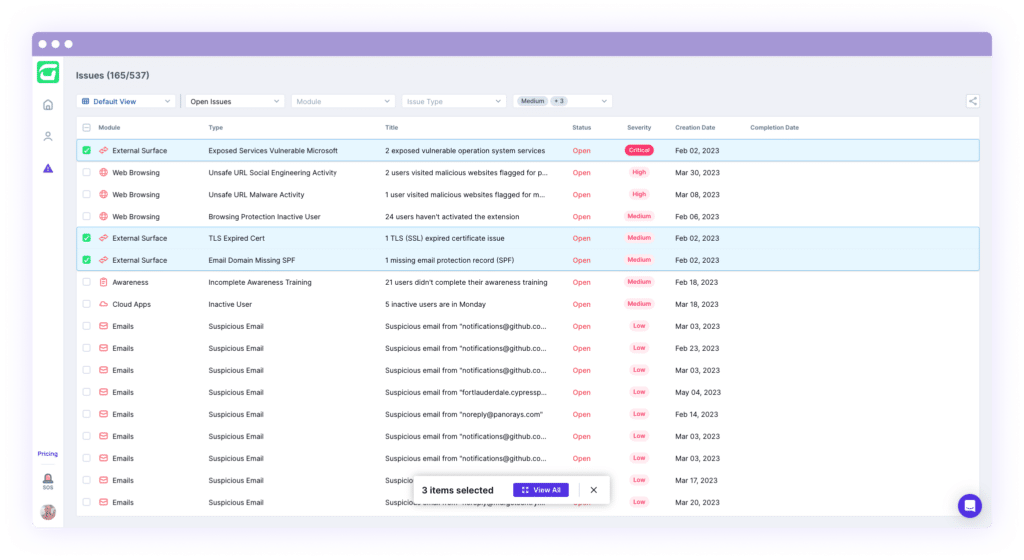
As the number of issues increases, it can be difficult to keep track of common threats and ensure that each issue is resolved in a timely and effective manner. That’s why we developed the Table Views & Bulk Actions – to provide a more efficient and streamlined approach for managing issues at scale.
When a table view is selected, the columns dynamically adjust to display the most relevant information for admins at-a-glance, allowing them to search, sort, and filter the data accordingly. For instance, if you have a use case to review all email issues originating from a specific sender or sent to a particular recipient, simply apply the Email View and filter by the relevant field. Similarly, if you need to see all data exposure associated with a specific owner, apply the DLP View and search for the relevant user.
Moreover, bulk actions allow you to review and remediate multiple issues concurrently. By leveraging the multi-select functionality, an admin can ignore or resolve any issues with just a few clicks.
Email Block/Allow Lists
Previously, Senders and Domains could only be added to the block/allow lists via issue remediation. With this product improvement, an admin can proactively add an email address or domain to these lists via manual entry.
Frequency of External Surface Scan
Previously, external scans were conducted quarterly for premium account holders in order to detect any changes in their external security posture. We improved this functionality so that when remediation occurs, scans are initiated to validate any remediations and guarantee a continuously healthy external posture. This enhanced feature ensures that our premium account holders have the most comprehensive and up-to-date security measures in place to protect their valuable assets.
We can’t wait for you to get your hands on the new updates. Be sure to keep your eyes peeled for more updates to come.
- Share On: