Strengthen your digital perimeters and eliminate external exposures by implementing effective security from the outside in.





Businesses face high levels of footprint from external threats posed by the dark web and other forms of external exposure. Cybercriminals can exploit vulnerabilities at any moment to cause data breaches, financial losses, and reputational damage.
xxxxxx
Open ports, misconfigured firewalls, and vulnerable applications can be exploited by cybercriminals to gain unauthorized access to your network.
Incorrect DNS records, missing SPF or DKIM records, and other configuration errors can lead to phishing attacks, spoofing, and other targeted email-based cybercrime.
Improperly configured or expired SSL/TLS certificates can expose sensitive information and enable cybercriminals to launch man-in-the-middle attacks.
Leaked credentials are typically found in data dumps and other lists on the dark web and pose a critical risk to employees and businesses if they go unchecked.
It's difficult for small businesses to keep up with their external posture and the ever-changing methods of attack on an on-going basis.
The dark web is frequently used to buy and sell data targeting businesses and their employees for malicious purposes such as ransomware, competitive advantage, and financial gain.
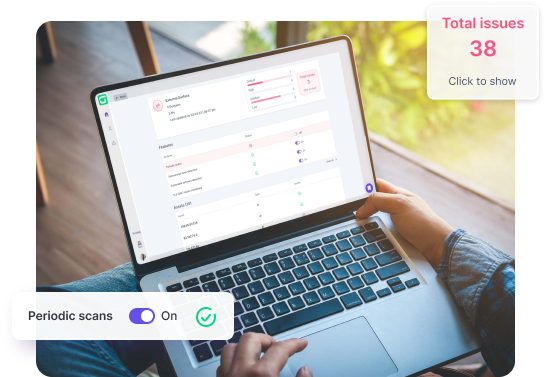
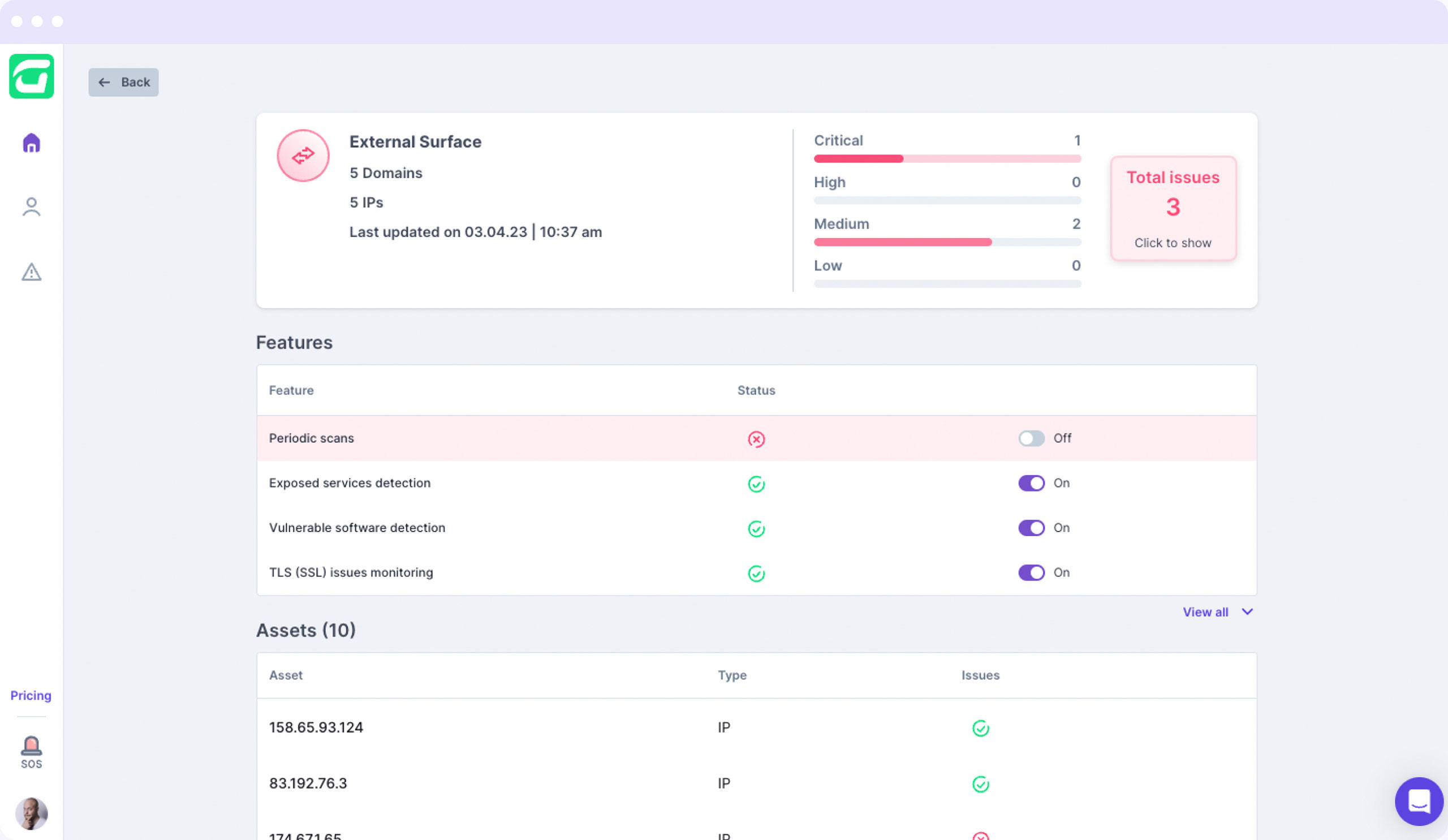
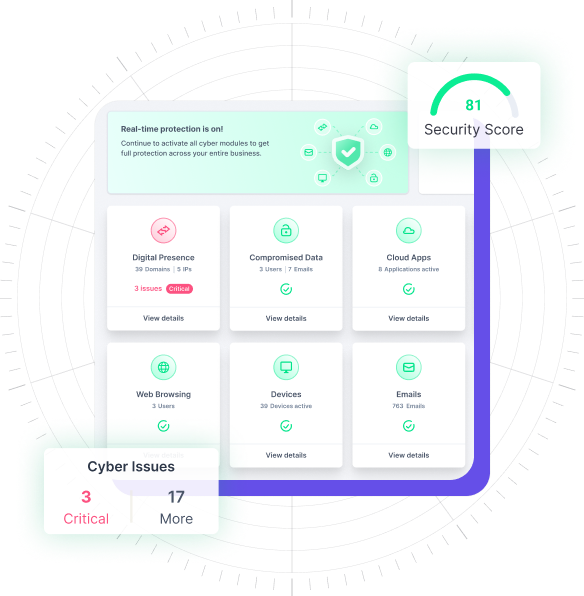
Guardz scans for open ports and public exposures to prevent malicious actors from accessing vulnerable and outdated services.
Monitor DNS email records to see if there is a missing or misconfiguration of SPF, DKIM, and DMARC to prevent spoofing, hijacking, or disrupting the email service.
Discovering the current use of protocols in public domains and servers enables Guardz protocol monitoring for missing TLS/ SSL certificates.
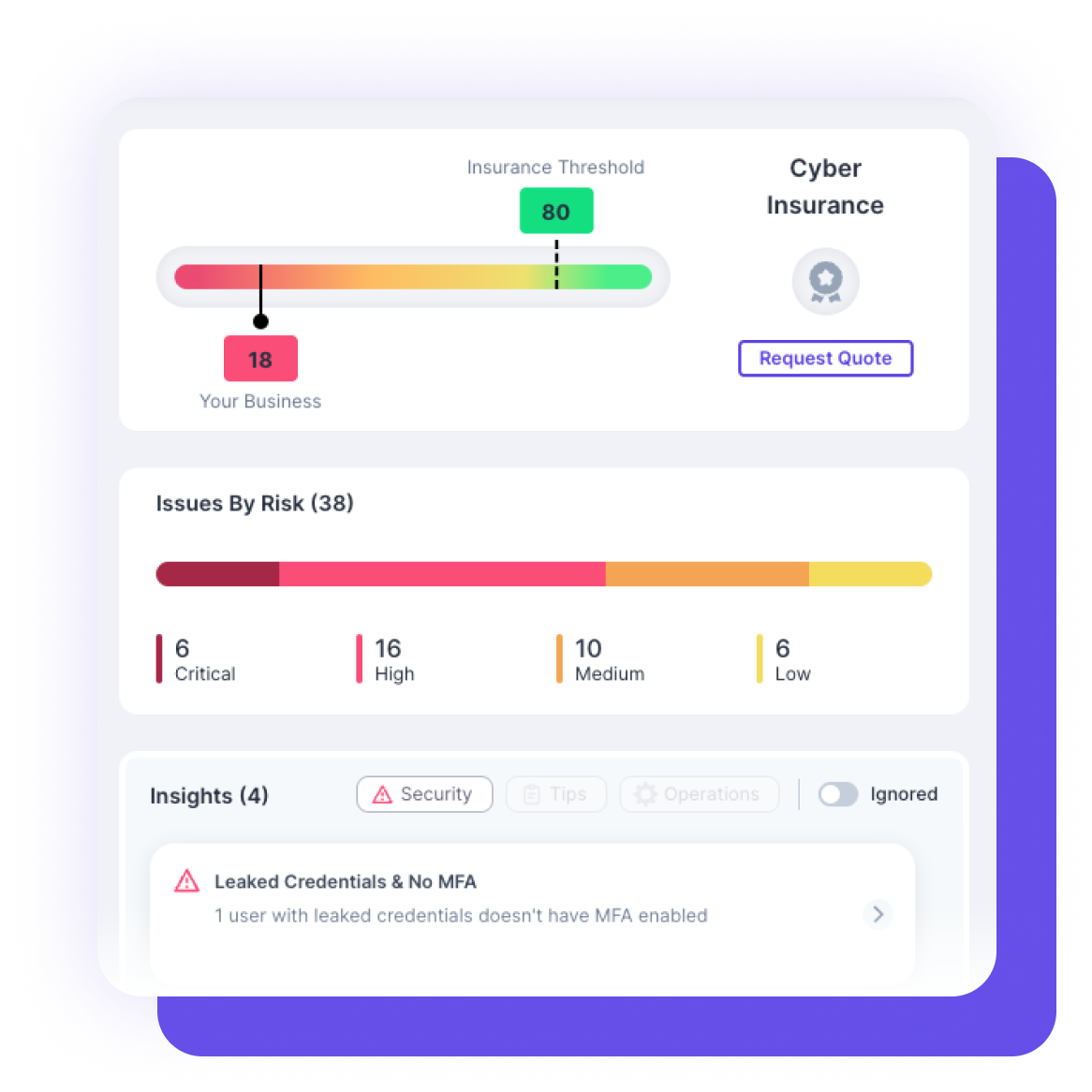
Generate a report summarizing risk across a business’s digital footprint based on exposed assets and external attack surface.
Guardz continuously monitors the internet for leaked credentials and exfiltrated data, triggering alarm bells when the keys to the castle are in nefarious hands.
Using machine learning tools, Guardz scrapes and analyzes dozens of sources that monitor the dark web for malicious activity targeting businesses and users.
After signing up with a business domain, Guardz initiates an initial risk assessment.
Results of a dark web scan are delivered within minutes, and issues are triggered to alert admins to the compromised data.
Results of the public exposure scan are delivered within 3 hours to 3 days and trigger alerts to admins to external surface results.
Guardz remediation playbooks enable precise steps for simplified resolution, leveraging industry best practices.
Each business receives a security score based on an overall risk assessment which will be continuously updated according to the issue status from external scans and reflect any new vulnerabilities.


We believe in taking a comprehensive approach to cybersecurity. Our holistic protection encompasses all layers of defense, providing a unified shield against threats and vulnerabilities, ensuring your organization’s security is robust and thorough.
When it comes to managing multiple clients, it can be overwhelming to address every potential threat. Guardz enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
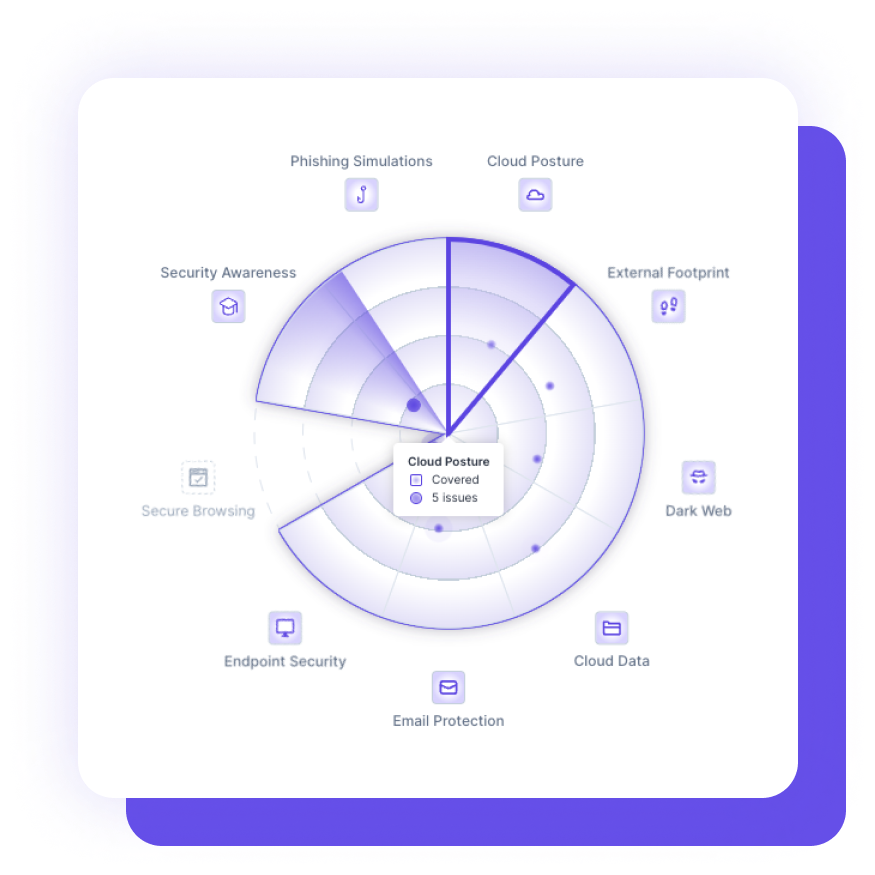


The Guardz managed security platform protects your business or clients from all attack vectors, including email, devices, external exposure, cloud apps, employee awareness, browsers, and more, ensuring that your security is resilient to any threats that may come your way.

Guardz takes advanced enterprise-level technology, democratizes securing your clients with our intuitive interface, and provides easy-to-use and automated playbooks that enable you to quickly detect, prevent, and respond to cyber threats.
Save up to 75% of your cybersecurity costs. Guardz offers tailored security measures that combine essential security tools into a single platform, so that it aligns with your budget and needs, providing an efficient way to mitigate cyber risks without breaking the bank.

External footprints are potential security threats outside a business’s network or systems. These can include various malicious actors, such as hackers, cybercriminals, and state-sponsored attackers, who may attempt to gain unauthorized access to sensitive data, disrupt business operations, or cause other damage.
If your business experiences a data breach, it’s important to take immediate action to contain the breach and minimize the damage. This may involve shutting down affected systems, notifying affected customers, and conducting a forensic investigation to identify the source of the breach.
External footprints originate from outside a business, such as hackers or other malicious actors, while internal footprints, such as employee errors or malicious insiders, come from within the business. External threats can be more challenging to prevent or detect, as they are often outside the business’s control.
Prioritizing and managing external footprints requires a holistic approach to cybersecurity, including regular security assessments and audits, implementing strong access controls and monitoring systems for signs of compromise, and investing in advanced security like Guardz technologies.
Third-party vendors may introduce new footprints to your business, as they may have access to your systems and networks or be responsible for handling sensitive data. It is important to carefully vet and monitor third-party vendors and contractors to ensure they meet your security standards and do not introduce new vulnerabilities.
Security assessments and audits are critical tools for identifying external footprints, as they help businesses identify vulnerabilities and assess the effectiveness of their security controls. Regular assessments and audits can help businesses stay ahead of emerging threats and minimize the impact of potential cyber attacks.
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

