AI Multilayered Cybersecurity Platform Built for MSPs to Secure & Insure Small to Medium-Sized Businesses Against Cyber Threats.
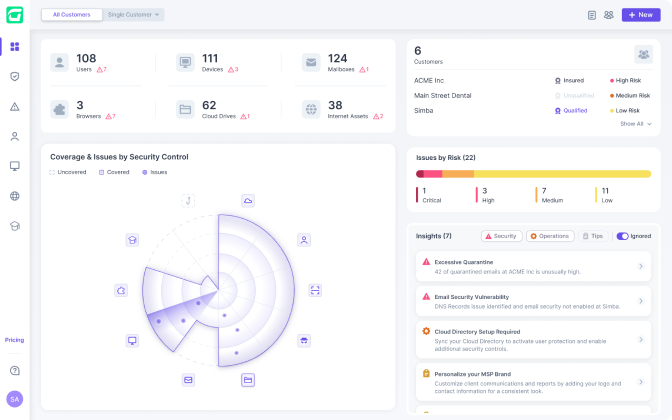

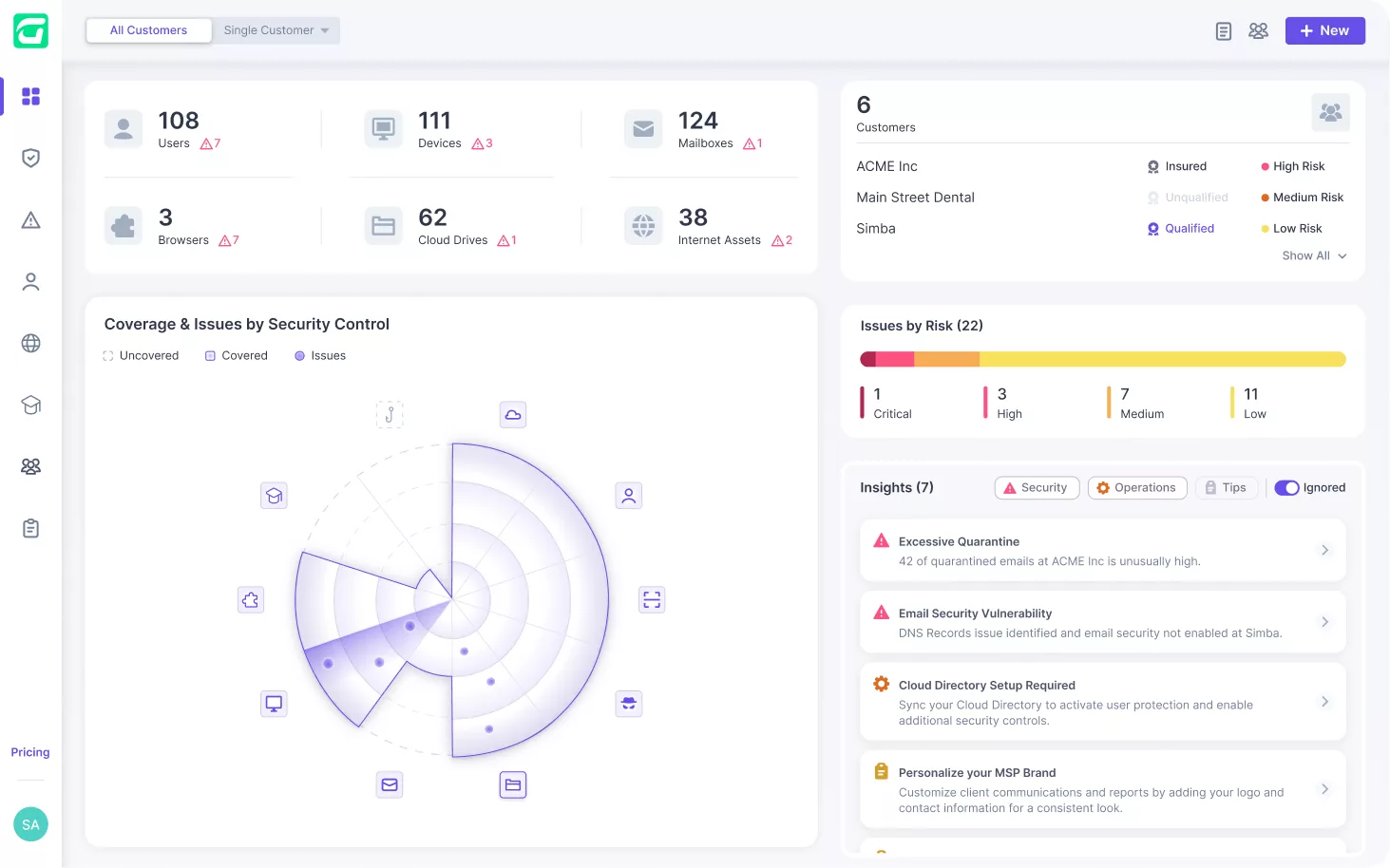
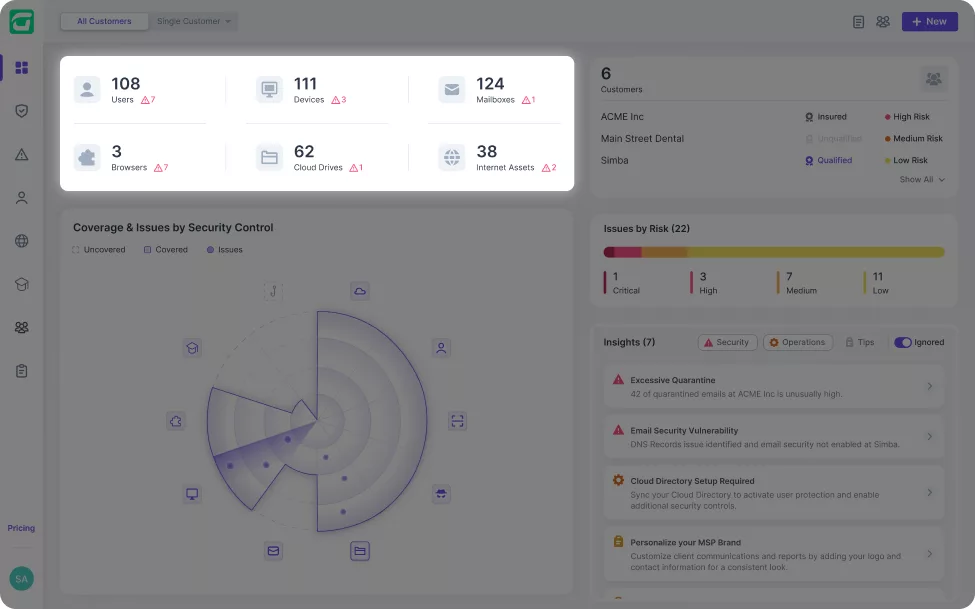


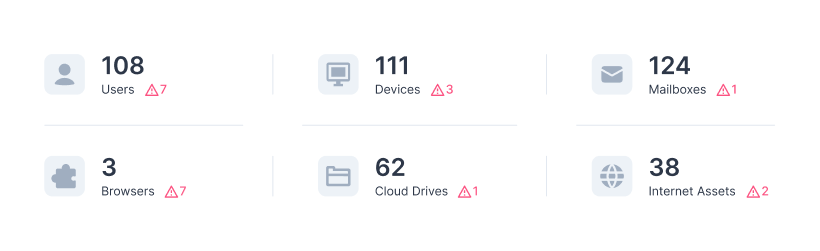
Guardz automatically discovers and monitors all your customers’ digital assets. Drill down to see more details and discover related issues.
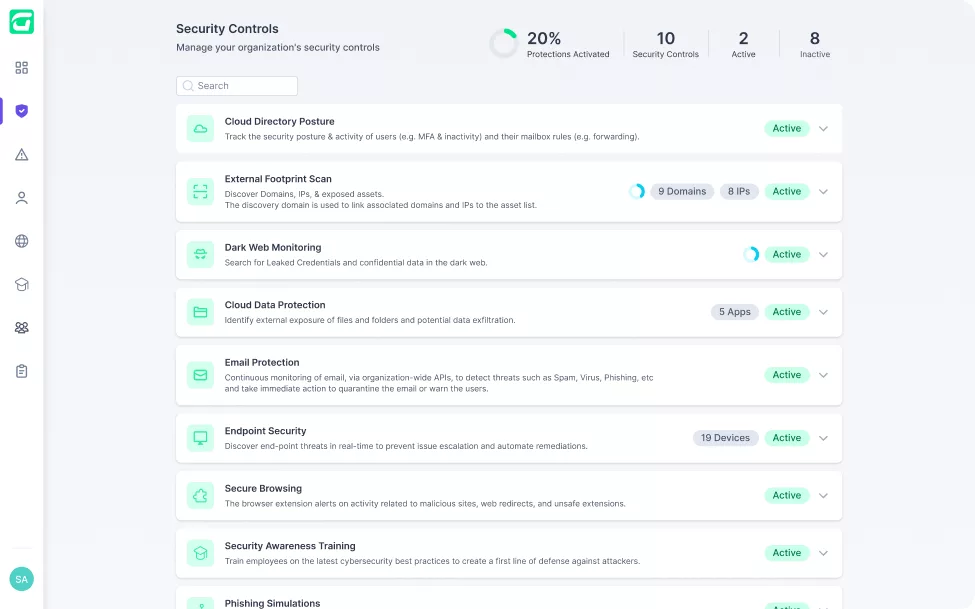
Guardz provides the security controls
and coverage across your customers and detects issues in real-time.
Real-time protection of all business employees across all applications, devices, and communication channels.
Connect the dots across detections and swiftly remediate, regardless of the attack vector.
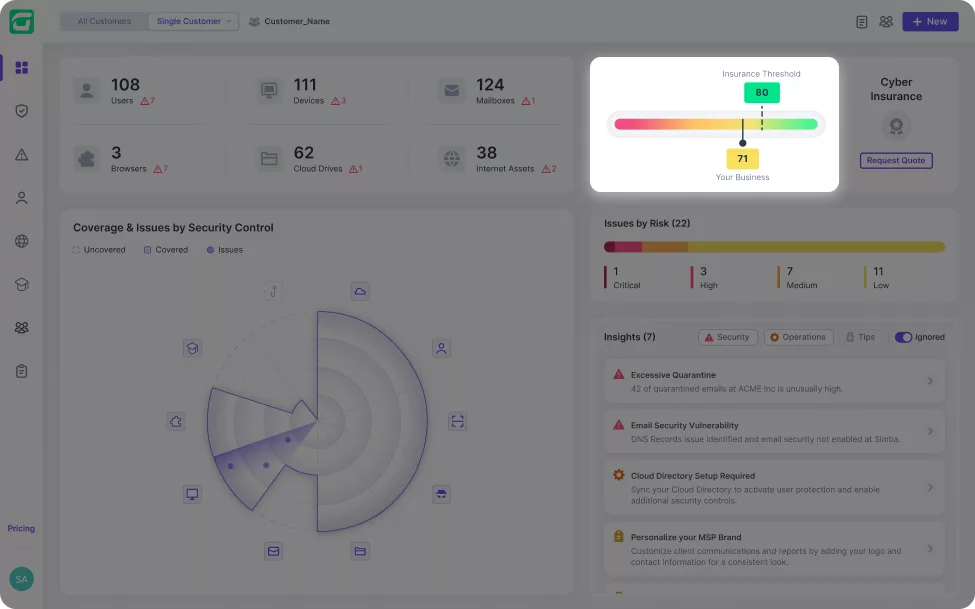
Get the coverage that you need at the right price based on your clients’ posture.




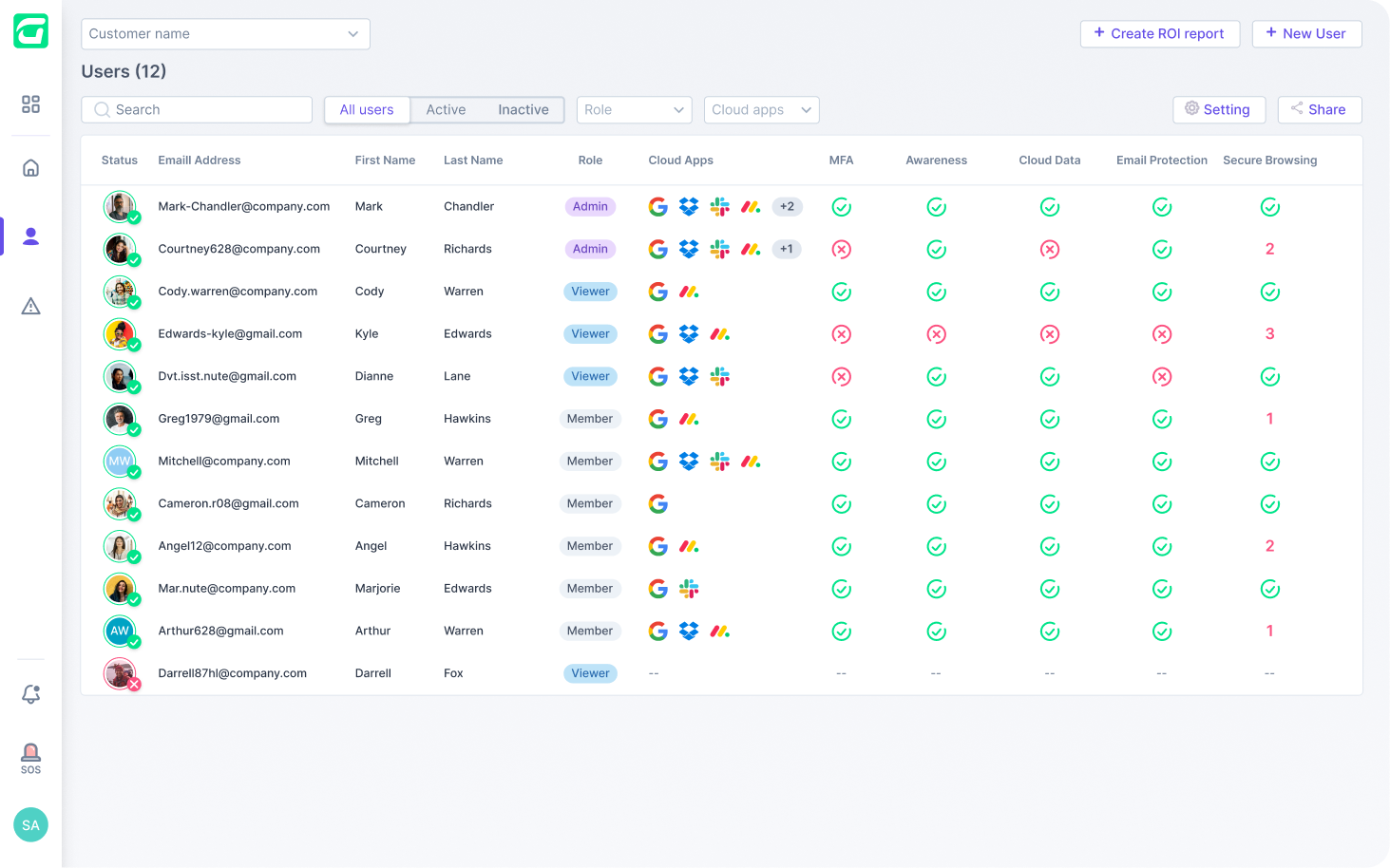




Guardz automatically discovers and monitors all your customers’ digital assets. Drill down to see more details and discover related issues.
Guardz provides the security controls
and coverage across your customers and detects issues in real-time.
Get all the security controls needed to fortify your client cyber posture.
Real-time protection of all business employees across all applications, devices, and communication channels.
Connect the dots across detections and swiftly remediate, regardless of the attack vector.
Real-time cybersecurity posture score
that reflects the cyber risk and
remediation plan.
Get the coverage that you need at the right price based on your clients’ posture.
By assessing both internal and external vulnerabilities, from exposed assets to risky users, we proactively protect against the top attack vectors from the inside out.
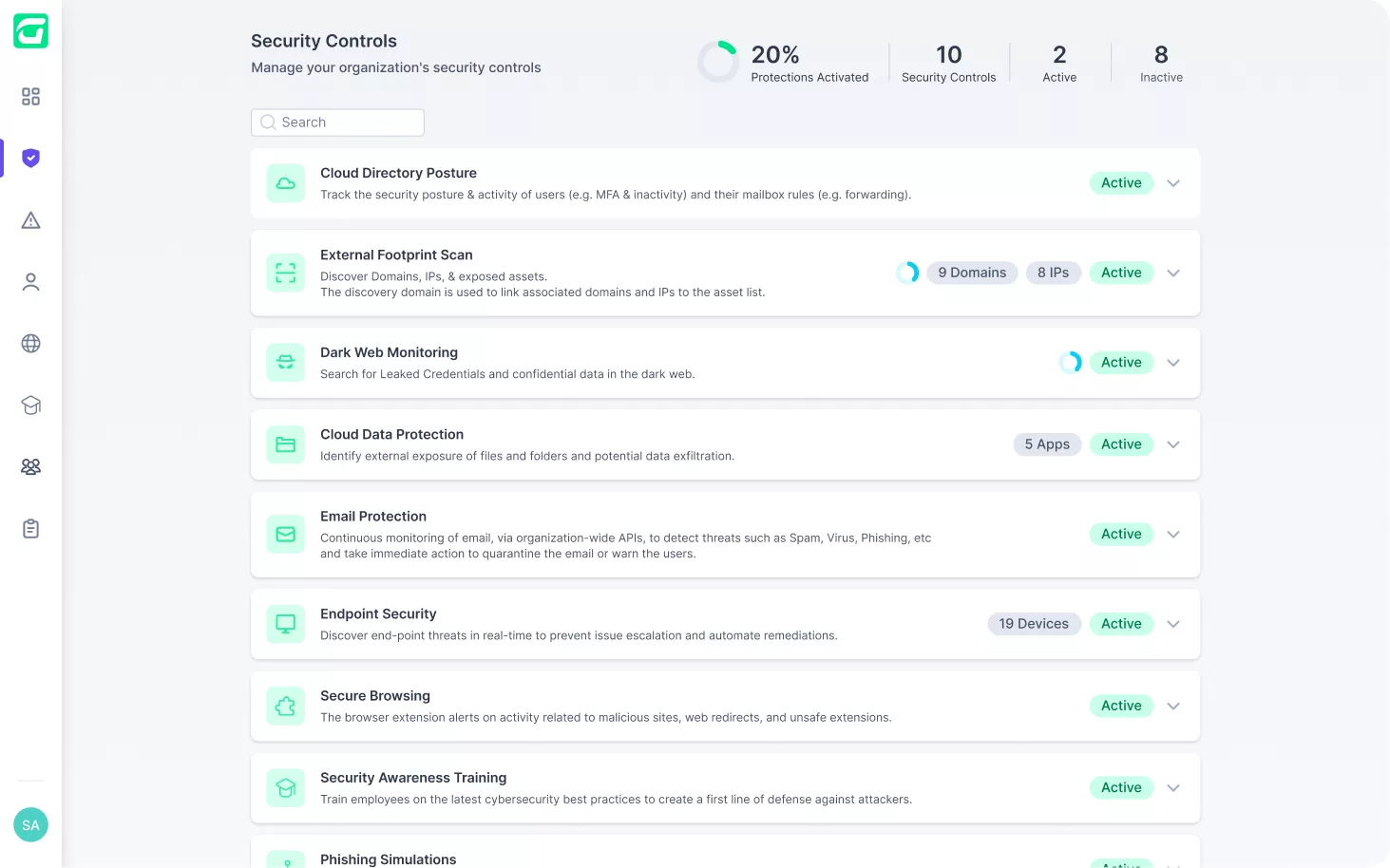
The Guardz Security Controls are a reflection of the holistic approach to cybersecurity, putting the core safeguards in one place while simplifying the setup and management of these critical controls.
This centralized view of Guardz Security Controls enables hassle-free configuration for each control, ultimately simplifying security implementation and issue resolution
in a breeze.
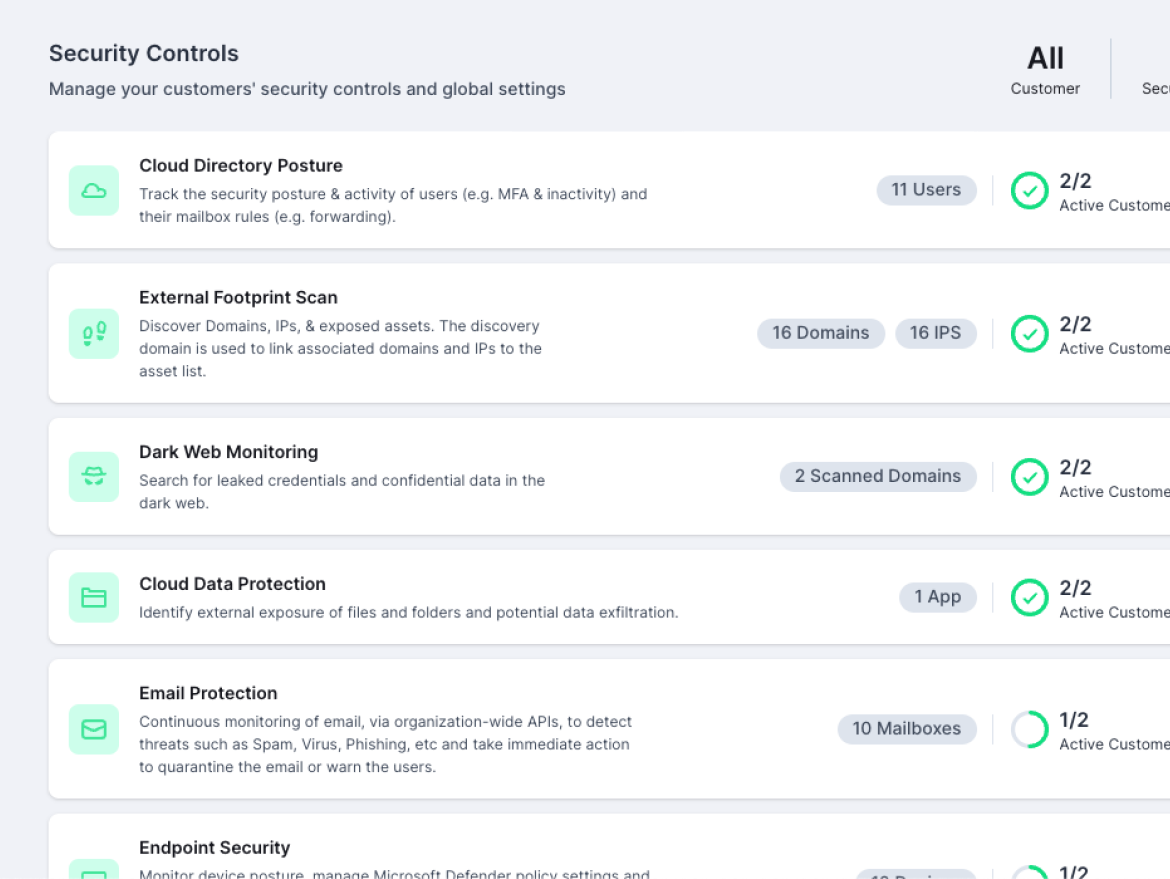
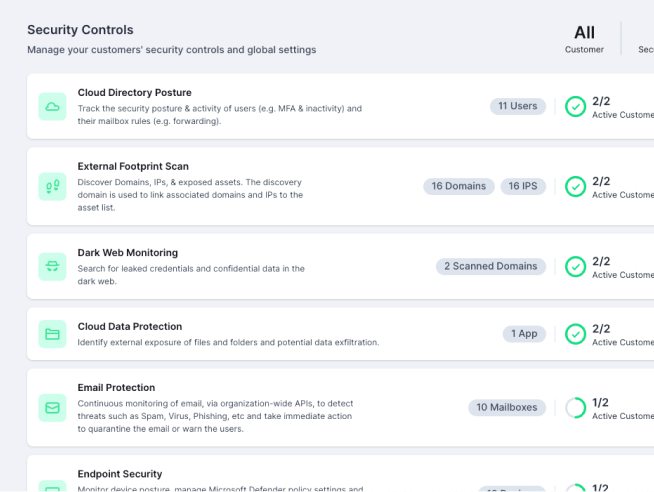
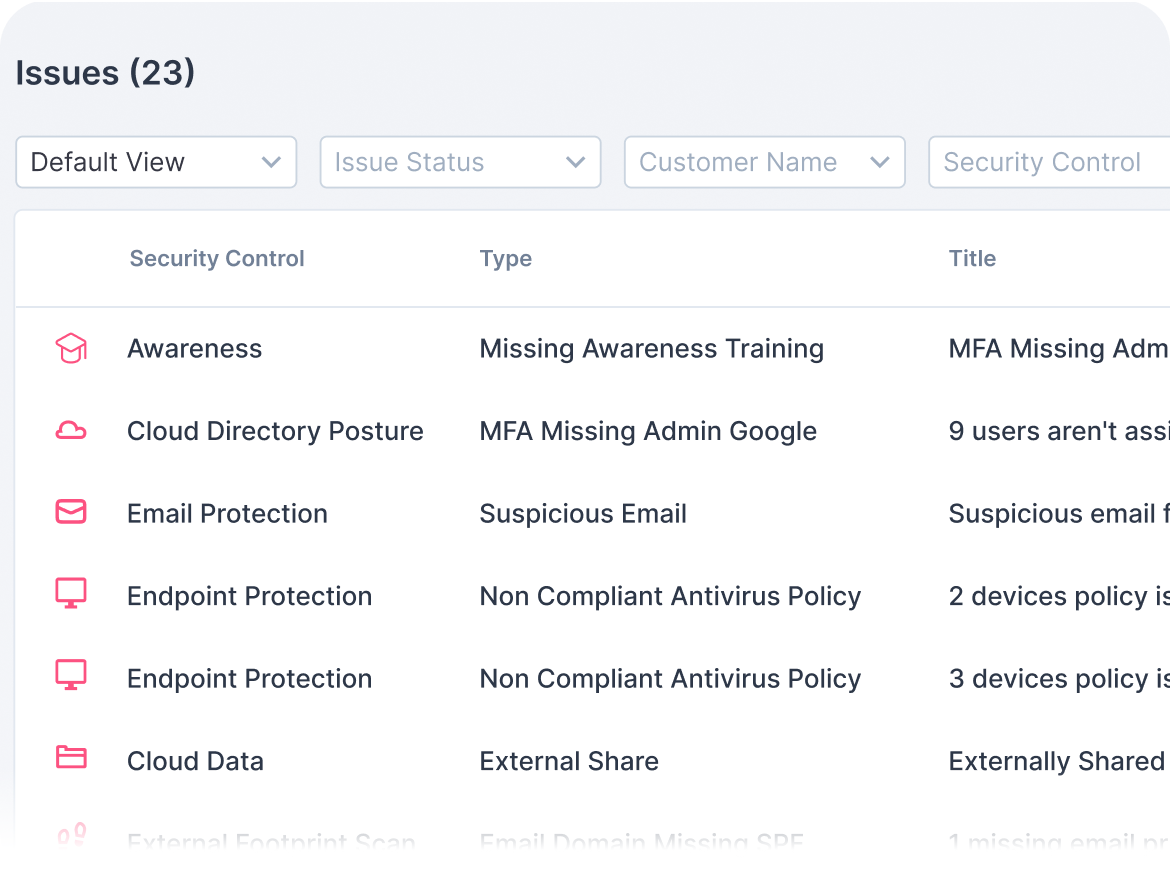
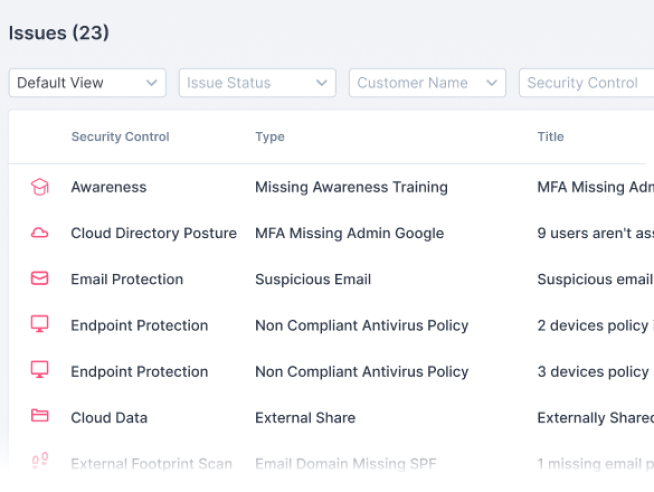
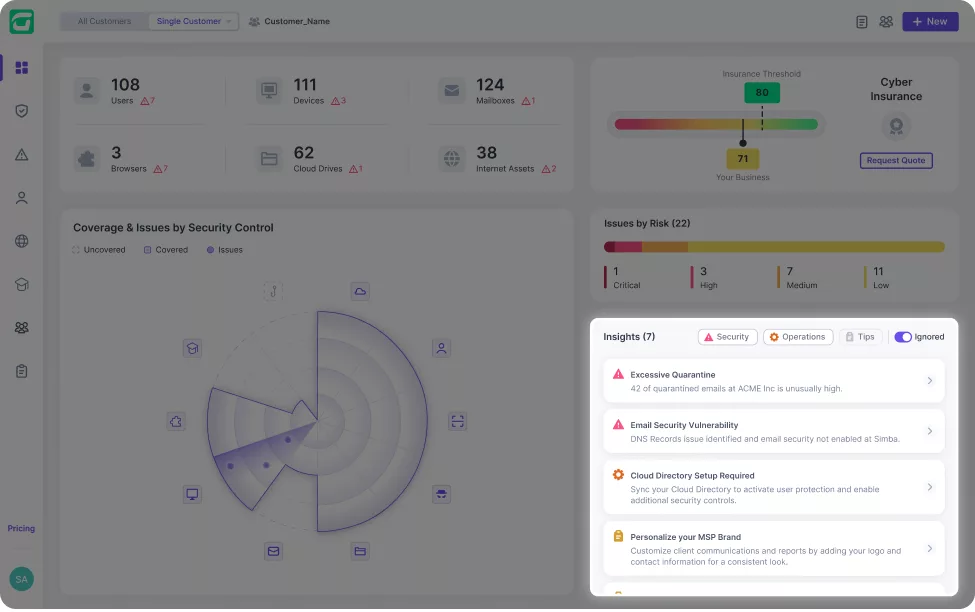
Guardz continuously scans for threats across multiple attack vectors and generates issues when a threat is detected. Issues are prioritized by severity of risk and include all the relevant details to trigger automated and manual remediations.
See more specific information about the issue, choose the most suitable remediation, and complete the action to resolve the issue.
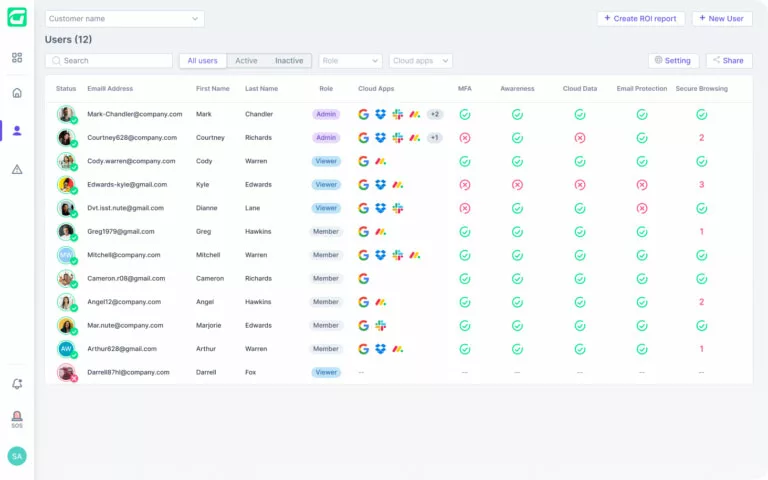
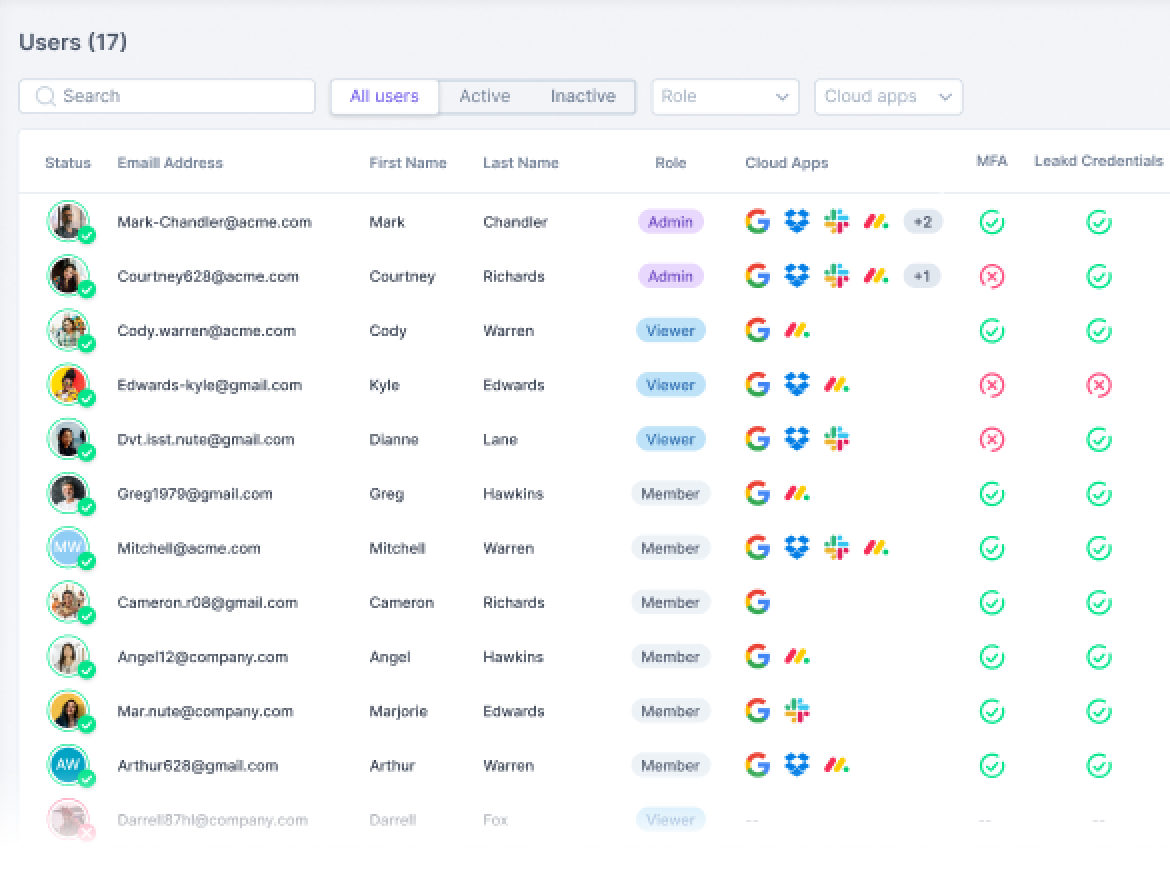
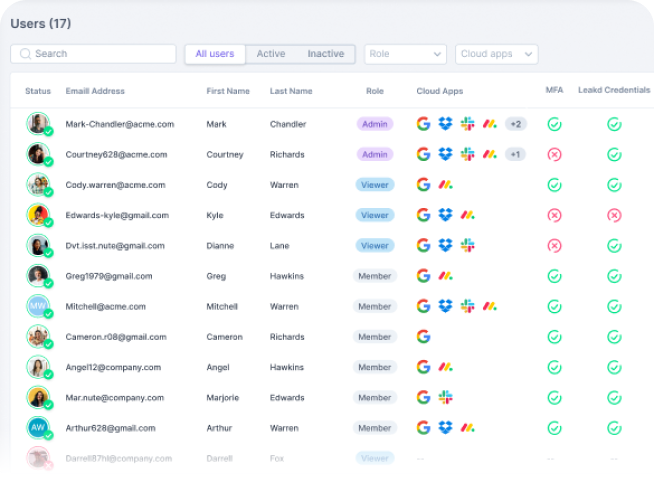
Users are at the center of defining an organization’s risk, so Guardz aggregates user-level data to paint a picture of employee risk and its impact on the company.
A company’s cloud directory (Google or Microsoft) is the source of the user list and is enriched with data about licensing, role, cloud apps, issue status, related devices, and more.
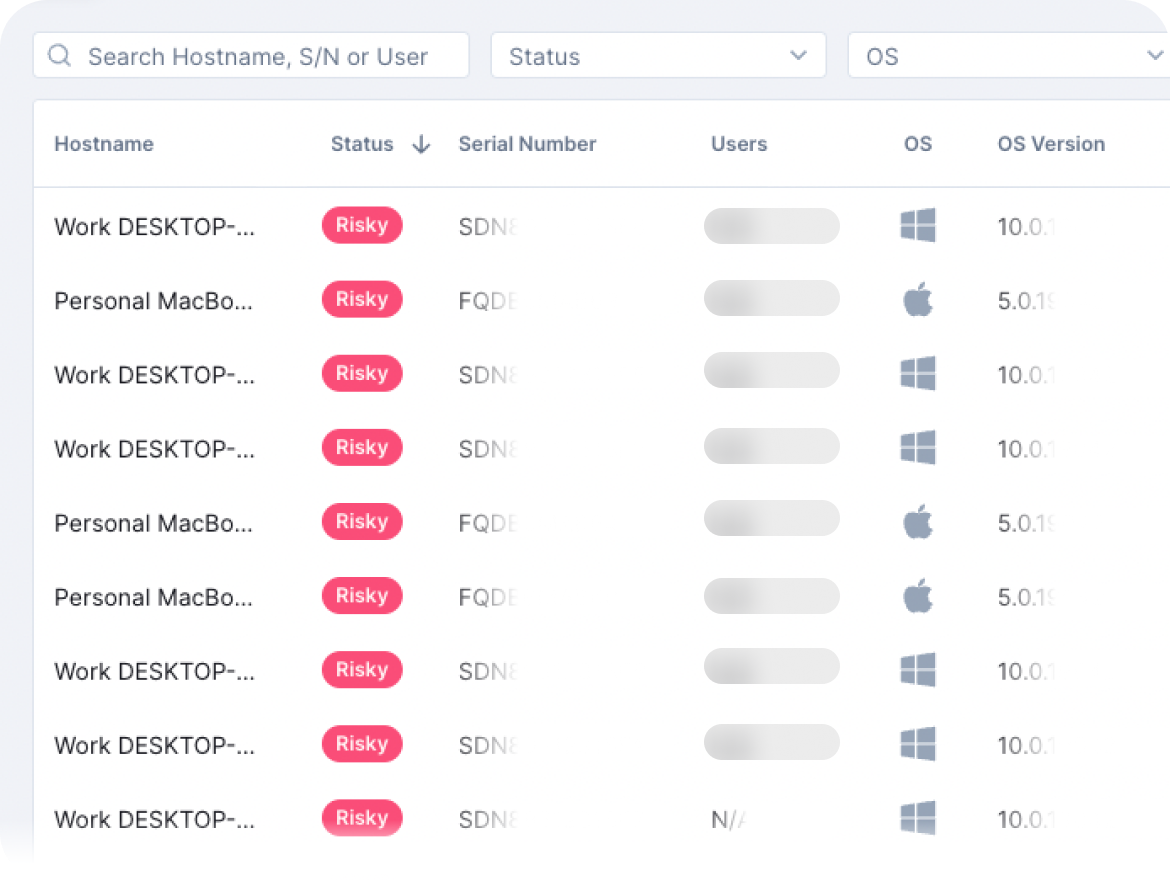
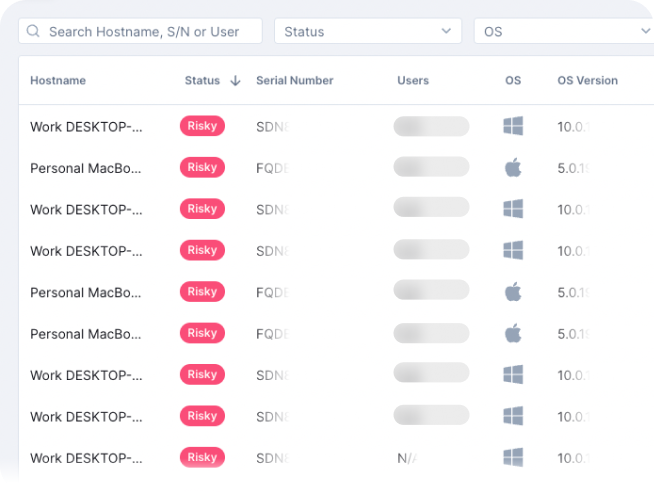
The simplified device management feature offers visibility into devices across an organization, providing vital information on their health status, relevant metrics, threat/risk levels, and existing issues.
This enhances the management of a company’s antivirus capabilities and streamlines the process of addressing device-related concerns.
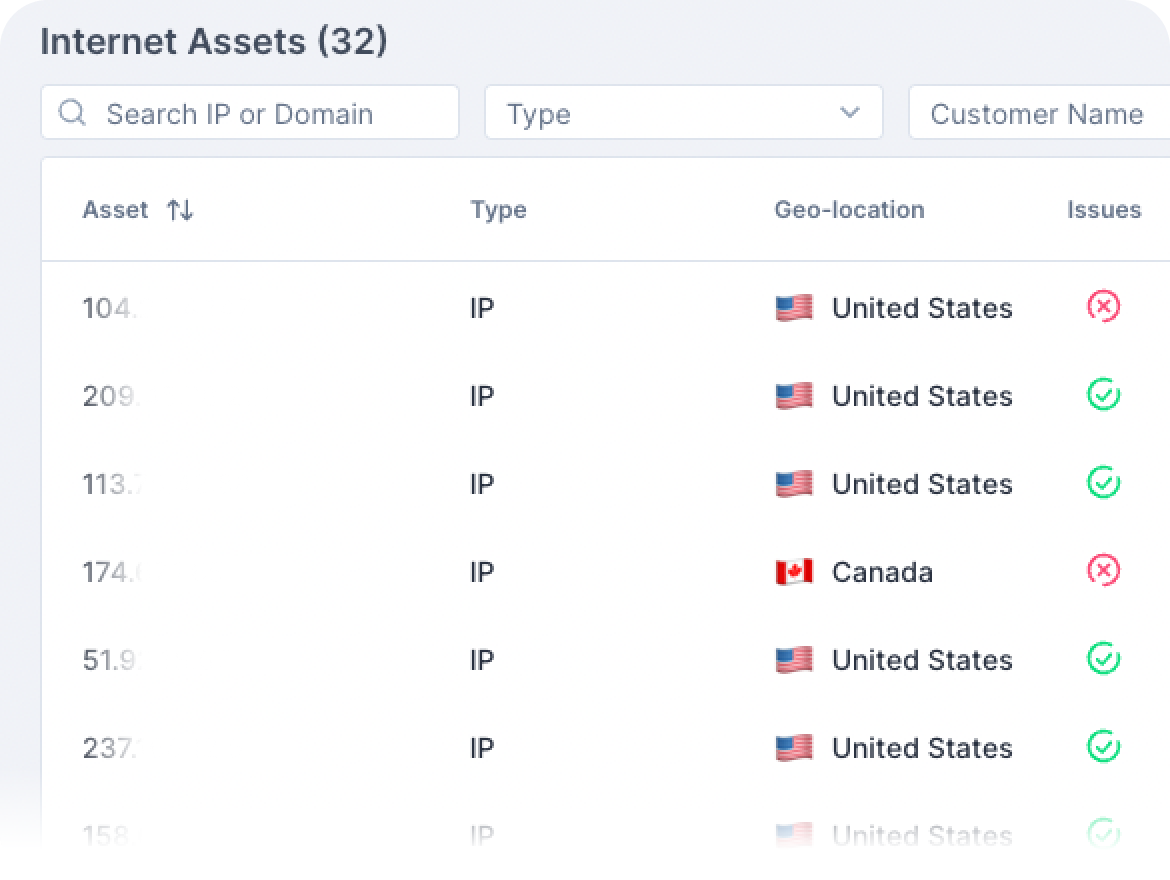
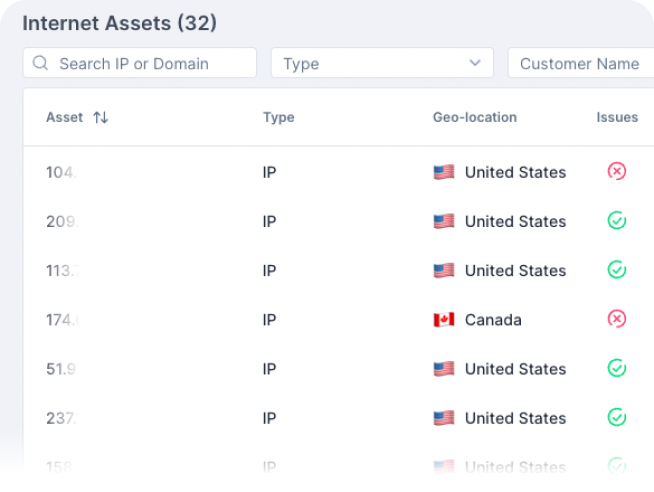
Attackers exploit weak points in the organization’s network, often left unprotected. The Guardz External Footprint Scan helps you to discover, manage, and monitor your organization’s assets in one place.
Upon initial sign-up, Guardz will run a scan automatically on all assets related to your primary domain (domains, sub-domains, and IPs) and discover all the connected assets.
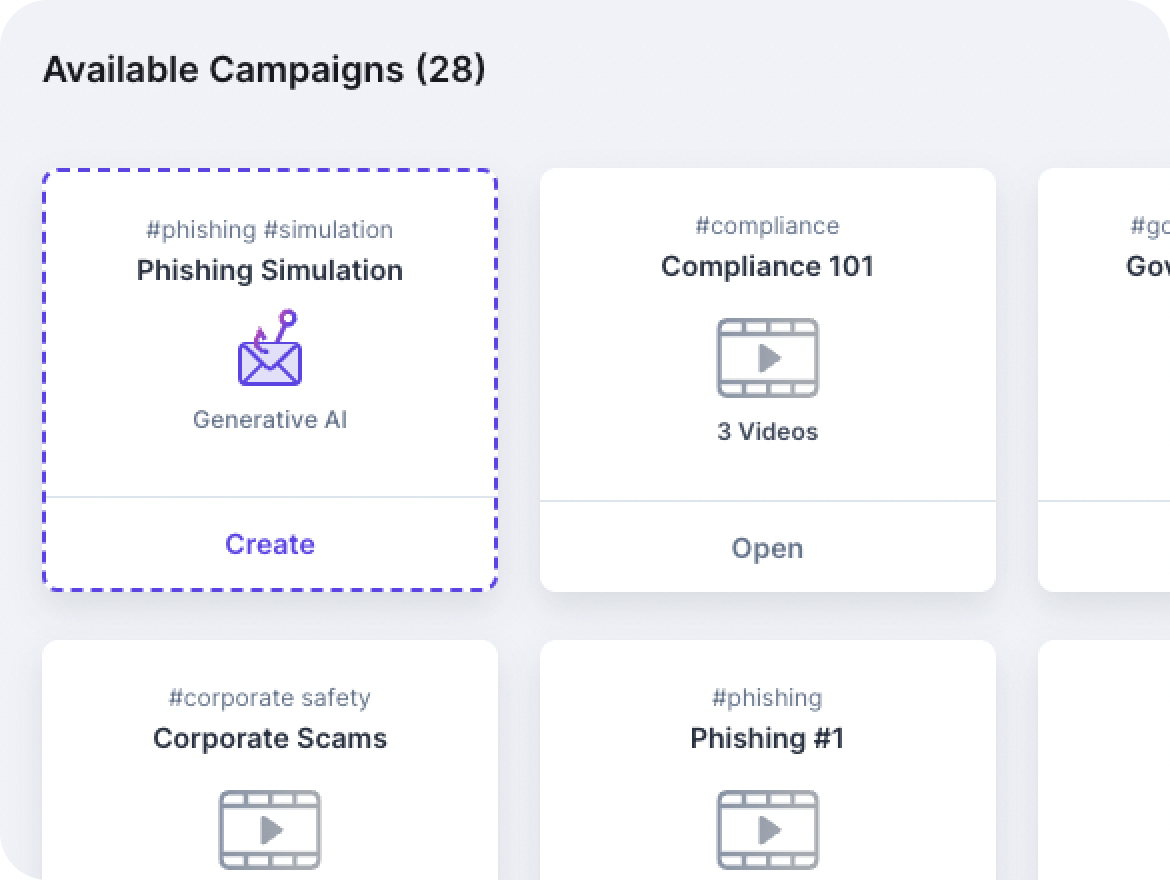
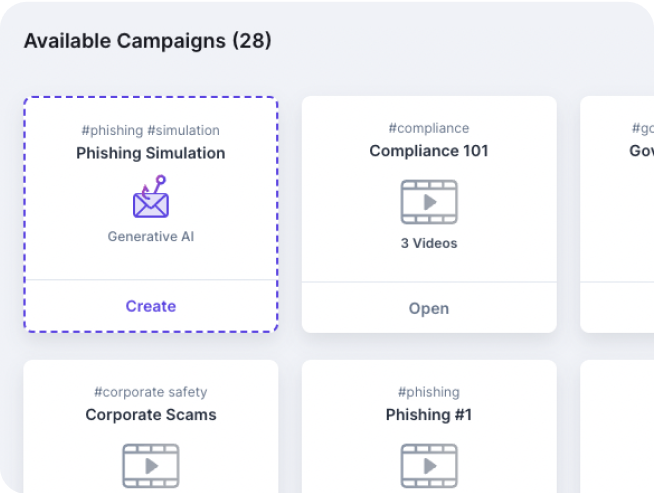
Guardz ensures up-to-date employee training by notifying admins of training status and recommending industry-standard best practices. Customizable campaign planning allows businesses to target specific users and meet company goals.
Phishing simulations help employees learn to avoid threats like ransomware and malware, while mandatory evaluations measure the impact of training.
The Guardz Growth Hub includes crucial tools designed to boost revenue, attract new clients, and demonstrate immediate value. This is achieved by leveraging Prospecting and ROI reports, facilitating easy access to marketing collateral, and providing a visual representation of your subscription, clients & channel managers.
Utilize the Growth Hub to foster vital business conversations and contribute to your company’s growth.


Stay ahead of potential email threats by leveraging a user-friendly API-based email security solution.
Enable cloud data protection to achieve a safe and secure data collaboration with external users
Equip employees to be the first line of defense against the evolving landscape of cyber threats
Gain actionable insights on external threats by scanning digital footprint and exposed vulnerabilities
Protect laptops, and desktops from cyber threats such as malware, and ransomware
Keep your browser secure with the Guardz extension for protection against viruses and malicious sites
Continually simulating cyber attacks like phishing emails to highlight weak spots
Transfer the cyber risk associated with evolving cyber threats with tailored coverage at the right price





















Yes, Guardz automates and streamlines cybersecurity threat remediation. We accomplish this on a few levels; by offering a managed service option to save time on labor intensive tasks, and, with our runbook focused UI/UX.
To get started with Guardz, please check out this article from the Guardz Help Center:
MSP Getting Started with Guardz
Small to medium sized businesses are frequent targets of cybercriminals due to their weaker cybersecurity defenses. Common attacks include phishing, ransomware, malware, and insider threats, which can result in financial losses and reputational damage.
Guardz seamlessly provides continuous monitoring of both internal and external vulnerabilities. In the event of a potential threat, you will be immediately alerted and provided with a comprehensive remediation plan.
Guardz is designed with a multi-organization perspective that provides an aggregated view and a single-tenant drill-down aspect for individual customers and their employees.
Guardz equips MSPs with a prospecting report, highlighting potential clients’ risks across their digital footprints. This data serves as a powerful tool to attract new clients with pertinent points of interest.
Furthermore, Guardz offers MSPs an ROI report, illustrating the potential financial impact of a cyber attack and employee exposure and compares your clients’ cyber score with the industry benchmark.
Guardz is built specifically for MSPs to holistically secure and insure small and medium sized businesses against evolving threats by leveraging AI and a multilayered approach.
By combining robust cybersecurity technology and deep insurance expertise, Guardz ensures that security measures are consistently monitored, managed, and optimized on a unified platform to prevent the next attack and mitigate the risk.


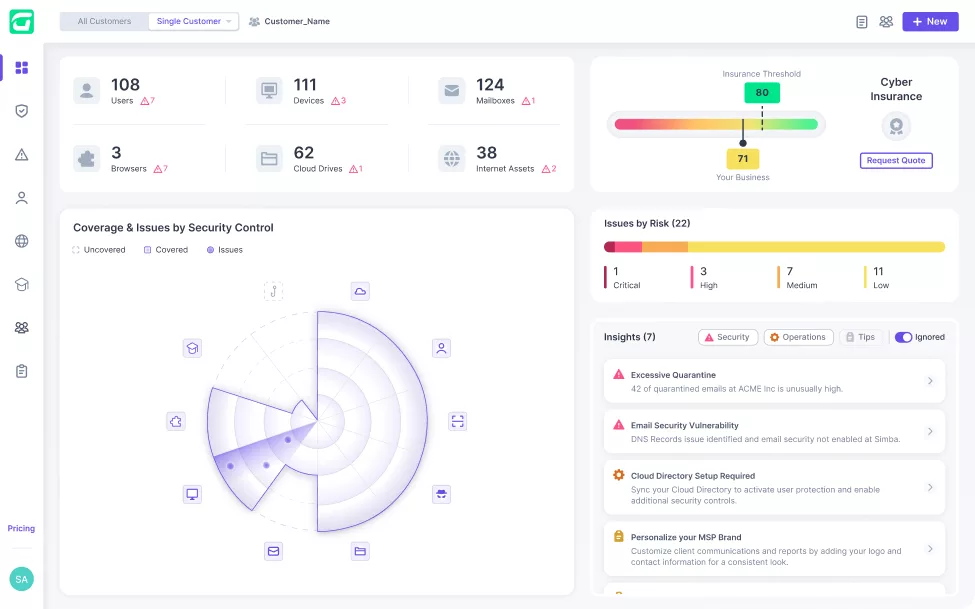

Guardz automatically discovers and monitors all your customers’ digital assets. Drill down to see more details and discover related issues.
Guardz provides the security controls and coverage across your customers and detects issues in real-time.

Get all the security controls needed to fortify your client’s cyber posture.
Real-time protection of all business employees across all applications, devices, and communication channels.
Connect the dots across detections and swiftly remediate, regardless of the attack vector.
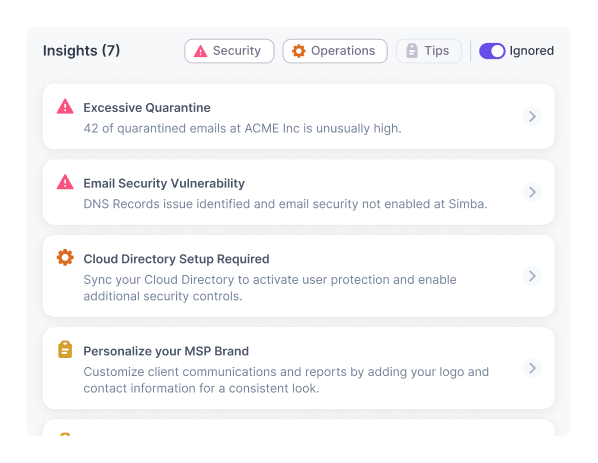
Real-time cybersecurity posture score that reflects the cyber risk and remediation progress.
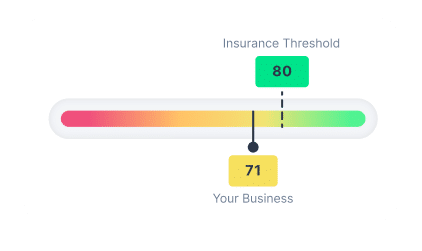
Get the coverage you need at the right price based on your client’s posture.
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

