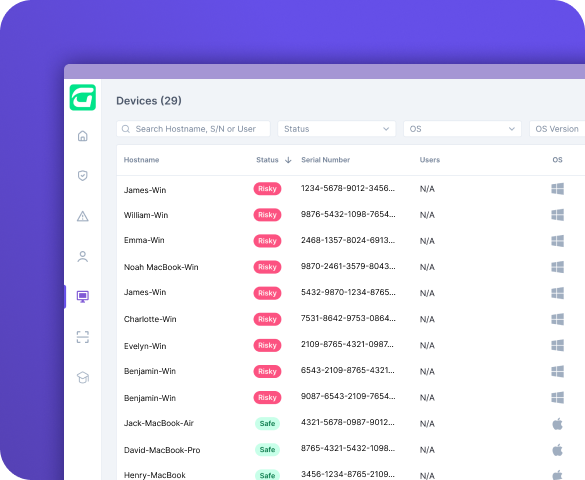
The Guardz device protection automatically identifies and isolates infected Windows and Mac systems


In data loss scenarios, paying a ransom provides no guarantee that the hackers will return the data uncorrupted or at all. There’s always a risk of permanent information loss.
The most immediate impact of a ransomware attack is the financial cost. This includes the ransom demanded by cybercriminals, potential loss of revenue due to disruption in operations, and expenses related to recovery efforts.
Ransomware attacks can grind business operations to a halt. If critical files or systems are locked, it might be impossible for a business to function until the issue is resolved.
If an attack leads to a data breach involving customers’ personal data, businesses could face hefty regulatory fines, especially under laws like GDPR.

Guardz conducts external scans to identify exposed vulnerabilities and outdated operating systems, enabling immediate remediation & strengthening of the perimeter.
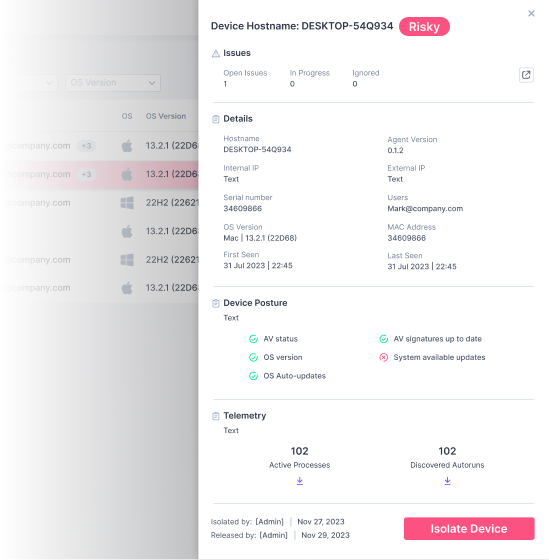
Guardz promptly monitors all of the Defender and Xprotect antivirus engines and detects malicious activity in real-time, ensures a secure device posture and identifies ransomware and empowers MSPs admins to take quick action and remediate the threats in an automated fashion.
Guardz provides advanced security capabilities on two fronts. It preemptively detects ransomware by creating bait files, alerting administrators before attacks escalate. Additionally, it empowers MSPs with snapshots of processes & auto-runs, enabling real-time monitoring of device activity.
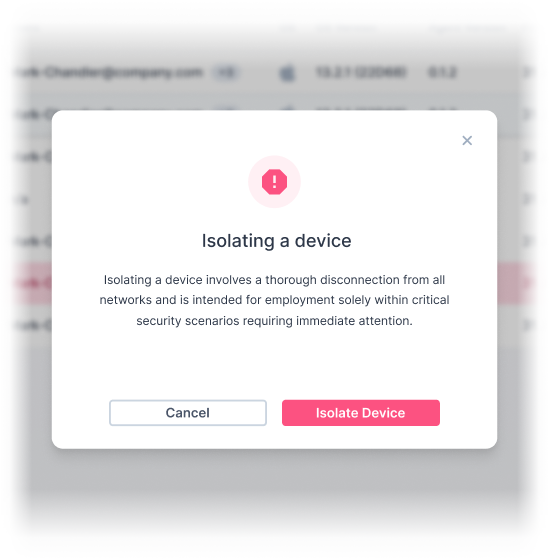
Guardz offers dynamic protection, swiftly responding to ongoing attacks by isolating compromised devices and disconnecting them from networks. Additionally, it proactively blocks or quarantines risky emails with malicious attachments, fortifying your defenses against potential mailbox infiltration.
Employees are the first line of defense so training them to recognize and detect the next attack, fosters a culture of caution and vigilance.
Guardz monitors internet browsing to detect malicious sites that can lead to ransomware download and alerts system admins in real time
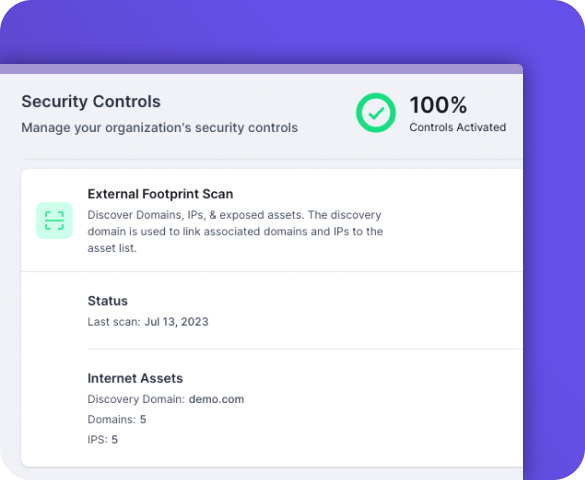
The Guardz external risk monitoring offers an essential component to protect against ransomware attacks by conducting an automatic external surface scan. By assessing a business’s digital footprint, the solution identifies exposed services, and vulnerable software.
Guardz ensures that employees’ and clients’ digital assets remain secure from targeted malware attacks that take advantage of external vulnerabilities while preventing known CVEs are key vectors for cybercriminal exploitation.
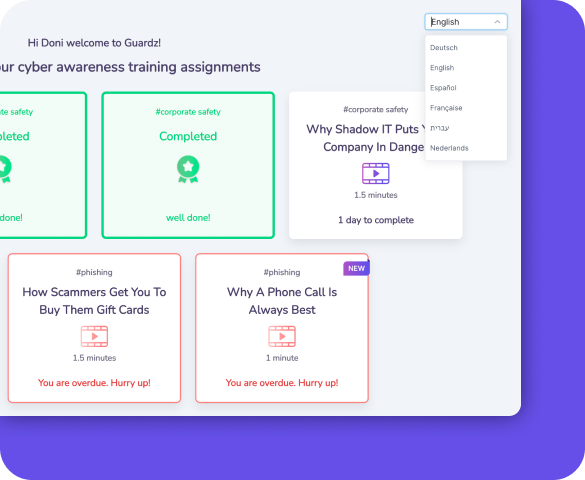
Guardz ensures up-to-date employee training by notifying admins of training status and recommending industry-standard best practices. Customizable campaign planning allows businesses to target specific users and meet company goals.
Phishing simulations help employees learn to avoid threats like ransomware and malware, while mandatory evaluations measure the impact of training.
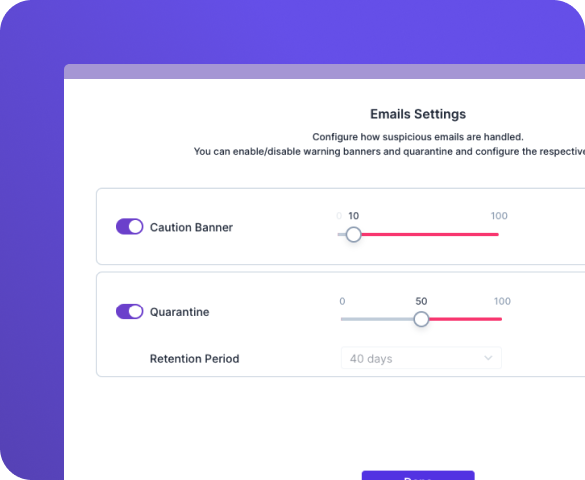
Guardz streamlines email protection with its fully managed, cloud-based solution that eliminates manual setup and seamlessly integrates with Microsoft 365 and Google Workspace accounts. Leveraging advanced predictive analysis, global intelligence tools, and continuous updates, Guardz provides robust defense against multiple attack vectors.
High-risk emails are immediately placed into quarantine to programmatically remove the threat. Employees receive warnings and recommended actions for potentially harmful emails, while IT admins can automatically flag and remove malicious messages.
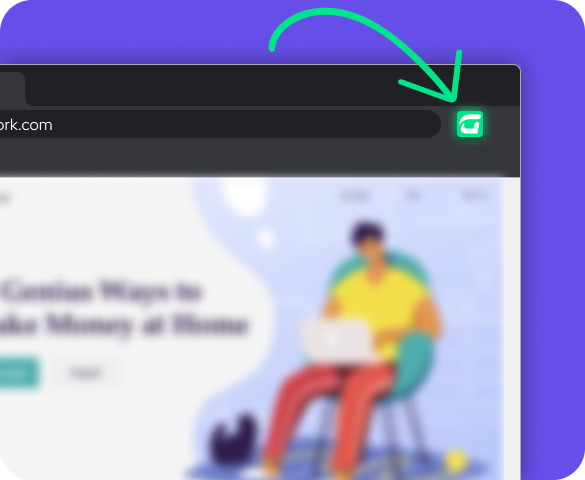
The Guardz browser extension plays a vital role in safeguarding employees’ online security as they engage in their daily internet activities. Working seamlessly with the main platform, the extension actively monitors access to known malicious websites, web redirects to phishing sites, and continuously scans for unsafe browser extensions.
By offering real-time alerts and comprehensive website analysis, the Guardz browser extension empowers employees to make informed decisions and navigate the internet safely.
Guardz provides an instrumental layer of security by pairing with Microsoft Defender Antivirus to proactively manage endpoint security for your organization. Performing ongoing scans in real-time on each device, the solution uncovers potential gaps in security posture, alignment with Defender policy settings and detection of real-world threats.
Strengthening internal security, Guardz assures your organization’s digital assets are protected against targeted digital attacks that exploit internal weaknesses. Guardz not only identifies these threats but provides real-time responses, including automated remediations, generating playbooks to address any issues, as well as offering a valuable snapshot of all processes for thorough investigation and research.





Some common signs are an unexpected screen alert or pop-up message indication that your data has been encrypted, demands for a ransom payment in exchange for a decryption key, inability to access your files, and your system working slower than usual.
If you become a victim of a ransomware attack, it is advised not to pay the ransom. Instead, disconnect the affected device from your network to prevent the ransomware from spreading. Report the attack to the local authorities and get professional help to remove the ransomware. If possible, restore your files from a clean backup.
Paying the ransom doesn’t guarantee you will get your files back. It also pushes the cybercriminals to target more people and makes this kind of illegal activity attractive to others. Rather seek proffessional help before taking next steps.
Ransomware attacks can be prevented by regularly updating and patching systems, using reliable, and holisitic security solutions like Guardz, backing up important data, avoiding suspicious emails and links, and educating employees or users about the dangers of phishing scams.
Antivirus programs can detect and remove many types of malware, including some ransomware strains. However, no solution is 100% effective, so practicing safe browsing habits and regular data backups is also crucial.
The recovery time can vary widely depending on the extent of the attack and the availability of up-to-date backups. It can range from a few hours to several days or even weeks.
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

