Harness the power of AI by generating simulated phishing emails to help bring awareness and identify the weakest links in your organization.
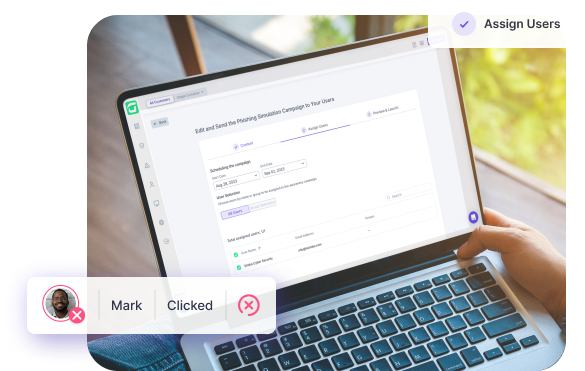
Guardz breaks the mold of traditional static libraries, providing dynamically tailored content for each department. This cutting-edge approach allows you to gather detailed data reports, highlighting the individuals who successfully identified the phishing attempts and those who failed to do so.
By staying up-to-date with the latest phishing trends, we ensure highly accurate simulations, arming your employees against emerging threats.





Phishing attacks pose a serious threat by impersonating trustworthy sources to trick individuals into revealing private data, such as passwords or credit card information. These deceptive practices can lead to unauthorized access and severe breaches of personal and financial information.
Phishing attacks pose a serious threat by impersonating trustworthy sources to trick individuals into revealing private data, such as passwords or credit card information. These deceptive practices can lead to unauthorized access and severe breaches of personal and financial information.
Hackers use this targeted form of phishing to gather information about businesses to draft personalized and convincing messages that are more likely to succeed.
Phishing emails, imitating trusted sources, aim to trick recipients into giving away sensitive information by clicking on harmful links or downloading infected attachments.
Hackers use this tactic to manipulate individuals into divulging confidential information or performing actions that may not be in their best interest.
These attacks, aimed at senior executives within businesses, seek to trick them into revealing sensitive information or conducting major money transfers.
Security is a team sport , it's not just the responsibility of security and IT pros but requires all employees to understand the risks and how to avoid pitfalls.
Malicious downloads from risky websites, deceptive emails, or pop-up ads, can harm a business's system once unknowingly downloaded and opened by users.
Phishing attacks can cause financial fraud, leading to legal issues, reputation damage, and loss of customer trust.
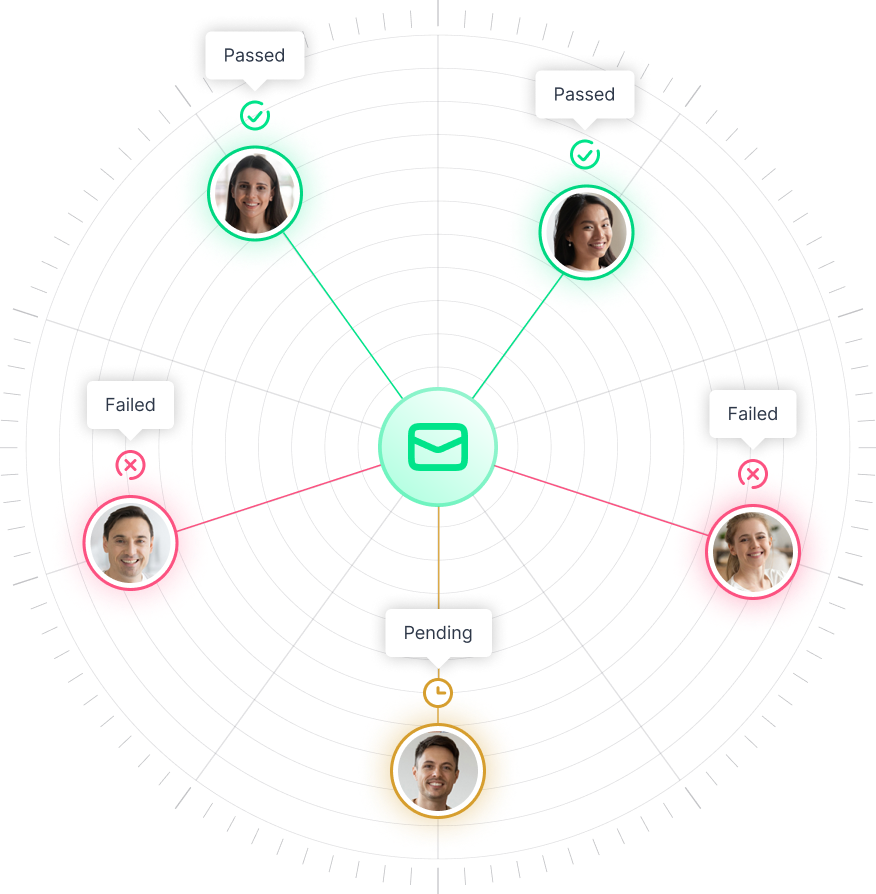
See in real-time the interactivity between employees and the simulation and gain insight into who passed and who failed
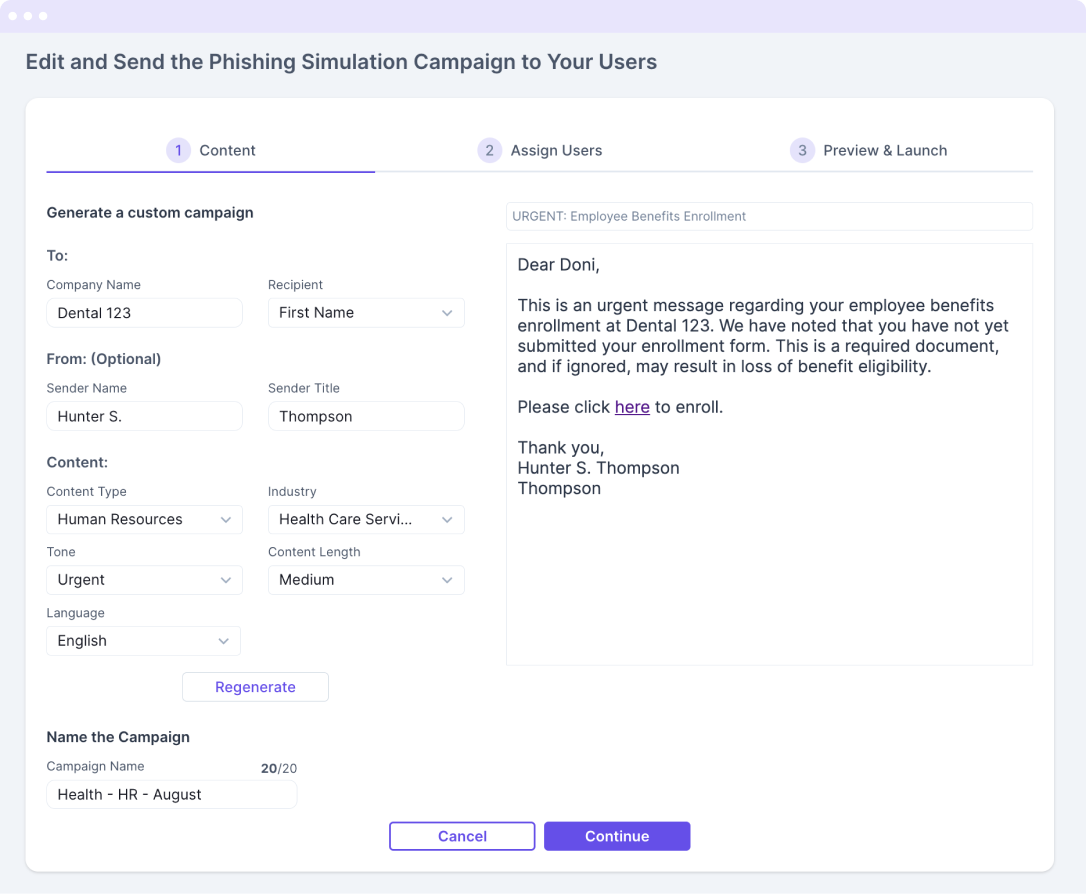
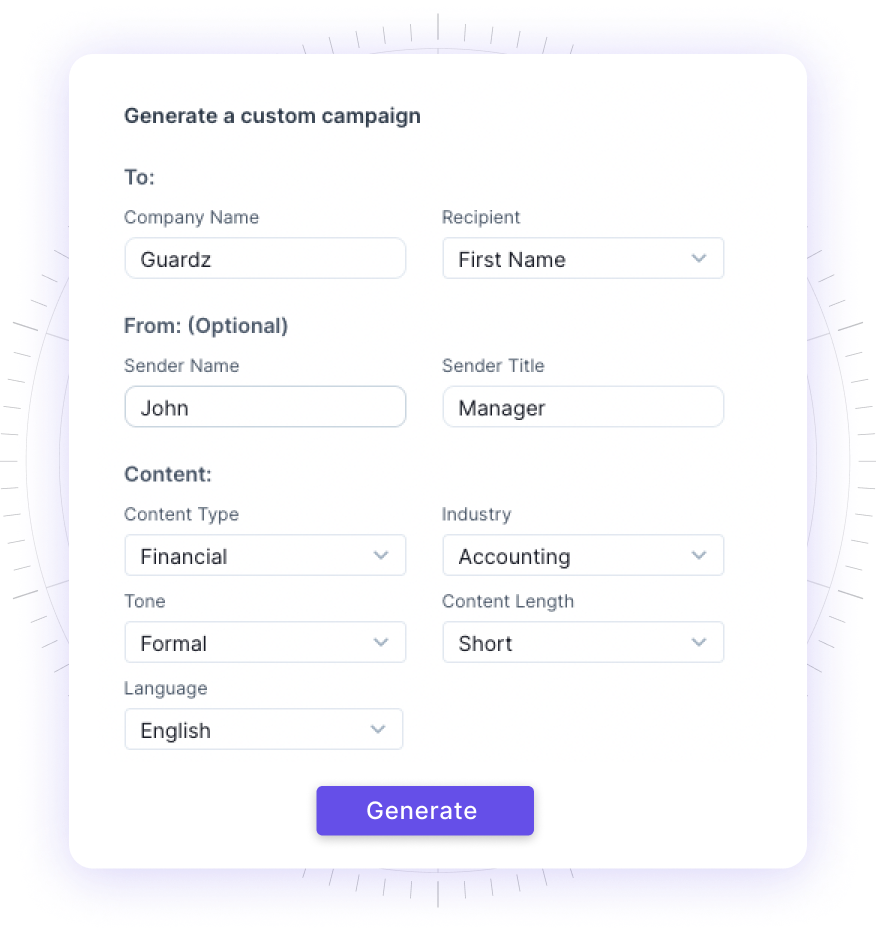
Instead of dealing with a library of outdated predefined emails, utilize the latest large language model to generate an email based on your custom inputs
Input your preferences based on industry, tone, style, length, and language to generate on-the-fly content to fit a specific audience, and if you are unhappy, regenerate
Utilizing automation, you can schedule the start and end dates for the Phishing Simulation. Upon completion of the simulation, an issue summarizing the results achieved will be generated
Users who click the link receive a polite yet firm alert, notifying them that they have not passed the simulation. This warning is followed by an awareness training session
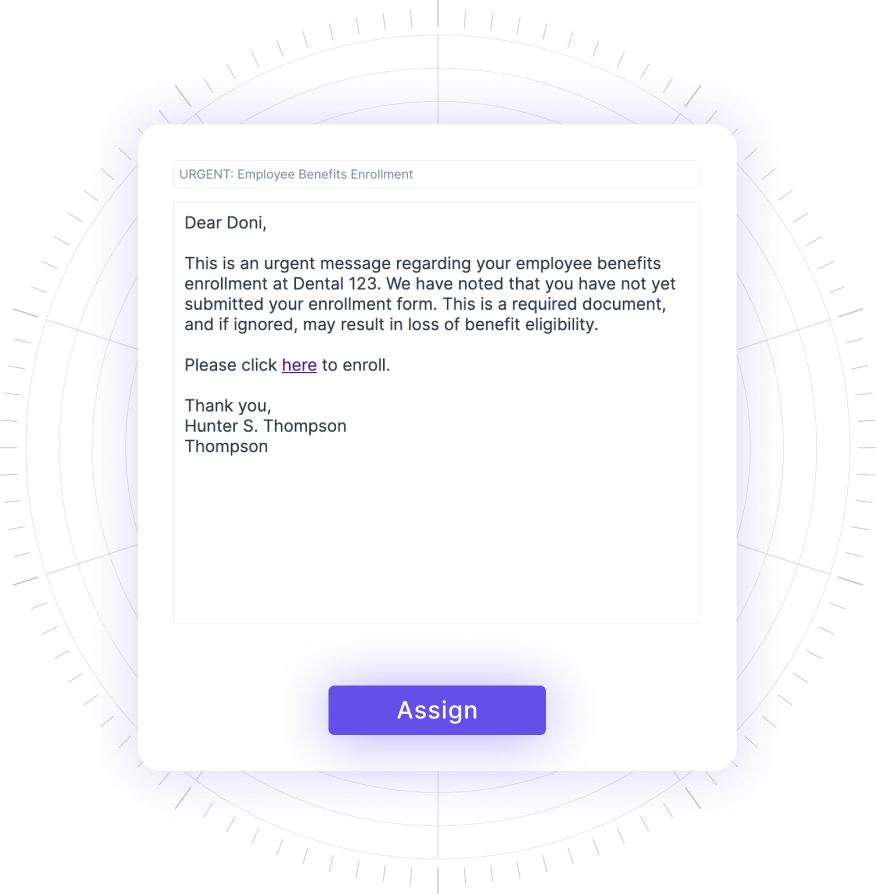
AI generates within a few seconds a personalized email template to be sent as part of the simulation using the values you’ve added. You can re-generate the content until you find the version you like.
Once you are happy with the content and have narrowed down the users and groups you want to target in the campaign, click ” Assign,” and the simulation will be sent.
After you activate the Phishing simulation, the results can be tracked in the simulation results. You can see the send rate, open rate, and click rate and which user clicked on the phishing link.
AI generates within a few seconds a personalized email template to be sent as part of the simulation using the values you’ve added. You can re-generate the content until you find the version you like.

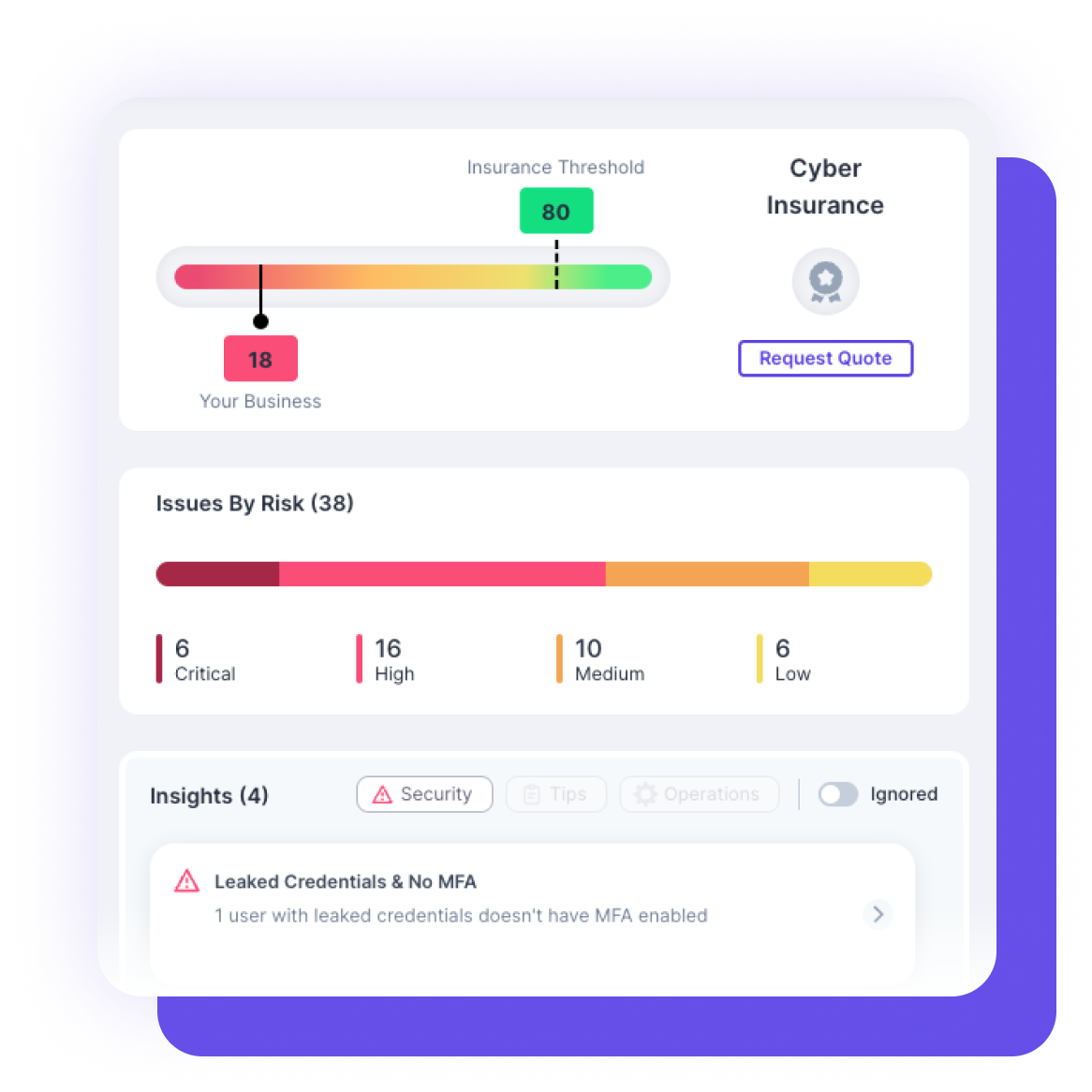
We believe in taking a comprehensive approach to cybersecurity. Our holistic protection encompasses all layers of defense, providing a unified shield against threats and vulnerabilities, ensuring your organization’s security is robust and thorough.
When it comes to managing multiple clients, it can be overwhelming to address every potential threat. Guardz enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
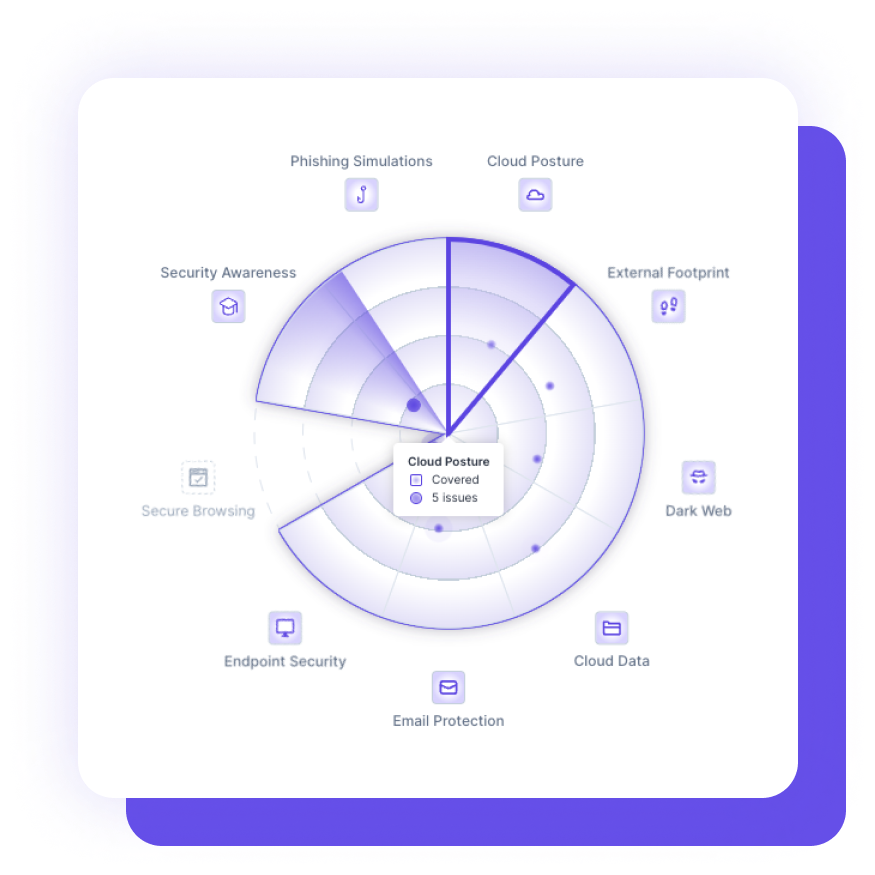


The Guardz managed security platform protects your business or clients from all attack vectors, including email, devices, external exposure, cloud apps, employee awareness, browsers, and more, ensuring that your security is resilient to any threats that may come your way.

Guardz takes advanced enterprise-level technology, democratizes securing your clients with our intuitive interface, and provides easy-to-use and automated playbooks that enable you to quickly detect, prevent, and respond to cyber threats.
Save up to 75% of your cybersecurity costs. Guardz offers tailored security measures that combine essential security tools into a single platform, so that it aligns with your budget and needs, providing an efficient way to mitigate cyber risks without breaking the bank.

Phishing simulations are controlled tests conducted by organizations to assess how susceptible their employees are to social engineering tactics, particularly phishing attacks.
Artificial Intelligence can be incorporated in phishing simulations to replicate the dynamic and evolving nature of cybersecurity threats. This helps by creating more realistic scenarios that mimic actual phishing attempts.
Yes, the learning algorithms in AI can help generate simulations that mimic real-world phishing threats more accurately, making the training more effective.
Through phishing simulations, organizations can determine how effectively their employees can identify and respond to phishing attempts, thus identifying areas where further training is needed.
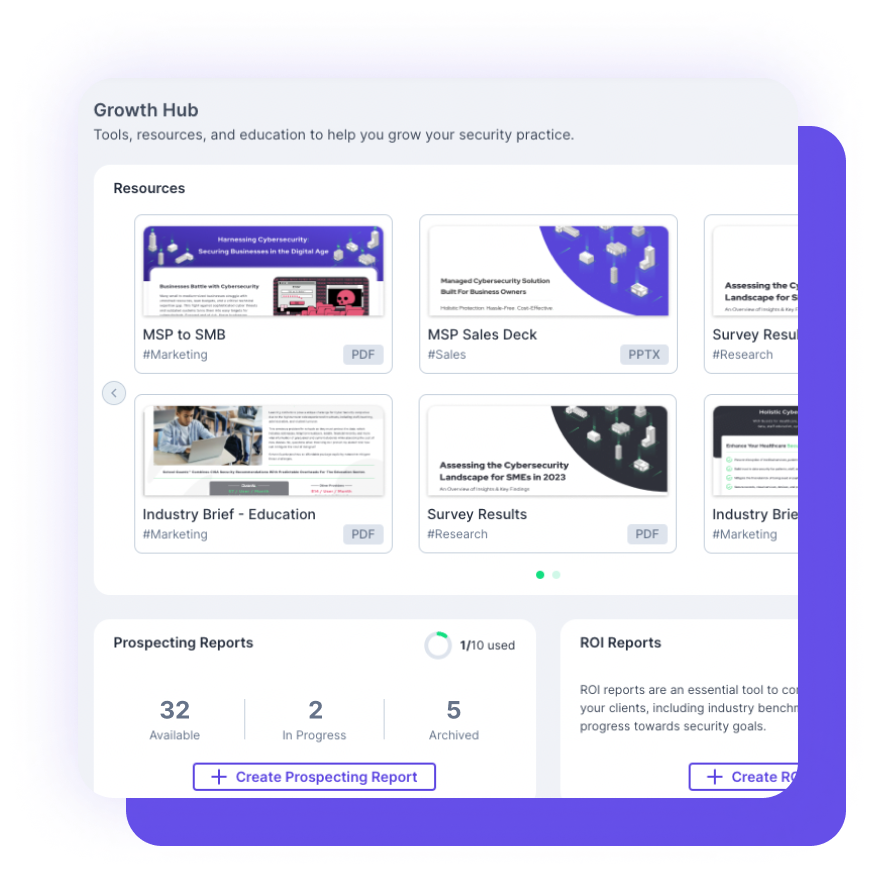
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

