Discover end-point threats in real-time to prevent issue escalation and automate remediations when it matters.

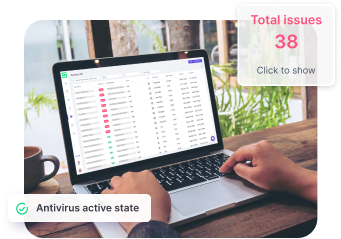
With an innovative solution and multi-layered approach, Guardz ensures that company-managed devices are fully protected and monitored from malicious threats.
Rest assured that employees and clients’ can focus on their day-to-day business while their devices are actively secured by industry-leading end-point security.





A device threat can compromise the security of an electronic device and lead to negative consequences such as data breaches, financial losses, or identity theft.
A device threat can compromise the security of an electronic device and lead to negative consequences such as data breaches, financial losses, or identity theft.
A virus can typically replicate itself and spread its malicious processes to other computers in order to corrupt, steal or delete files.
Malware downloaded from email attachments or websites, also embedded in legitimate software, damages computers and servers.
Ransomware extorts money by encrypting files on a device or in the cloud and demanding a ransom for the decryption key to avoid data loss.
Spyware & keyloggers are designed to spy on your computer activities and/or record exactly what is typed (ex. passwords) on a keyboard.
APTs are complex techniques that infiltrate systems without detection to disrupt operations or steal classified data without leaving any trace of their actions.
A Trojan horse is disguised as legitimate code or software patches that deliver malware to steal data, disrupt services, or create backdoors.
PUPs and adware are bundled with other software to forcefully install themselves on a device, and can be disruptive in less malicious ways.
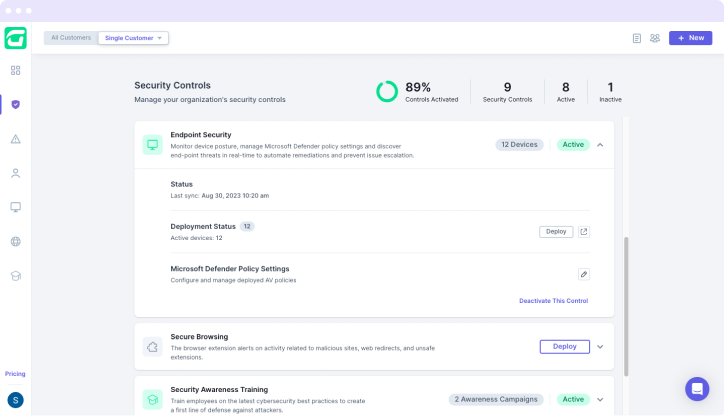
Leverage management capabilities on-top of existing endpoint tools to connect the dots and enforce policies on organizations’ devices and the relevant processes.
Map device resources and configurations to build a device security snapshot across an organization based on industry best practices for end-point protection.
Guardz detects outdated operating systems and vulnerable software so you can take appropriate actions with the guidance of the Guardz playbooks.
Leverage Guardz on top of the native anti-virus and anti-malware capabilities to manage and protect endpoints with automated remediations.
Working hand-in-hand with the Guardz browser extension, ensure employees are not exposed to malicious sites, web redirects, unsafe extensions, and more during their day-to-day internet activity.
By monitoring device processes and executables across an organization, Guardz can assist with investigation and response as threats are identified and for post-incident attack-chain analysis.
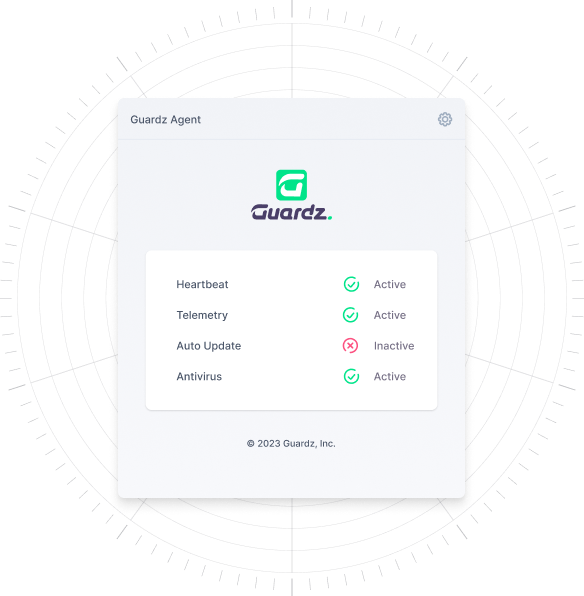
The Guardz device agent continuously monitors activity on designated end points, integrating with existing AV tools and communicating status to the management system.
Designed to identify anomalies in executables, processes, autoruns, and command-level activity, the Guardz agent surfaces the information that matters with an urgency that reflects the relevant risk.
Using the combined intelligence of the Guardz threat operations team and machine learning tools, malicious activity is isolated from the noise and brought to the forefront.
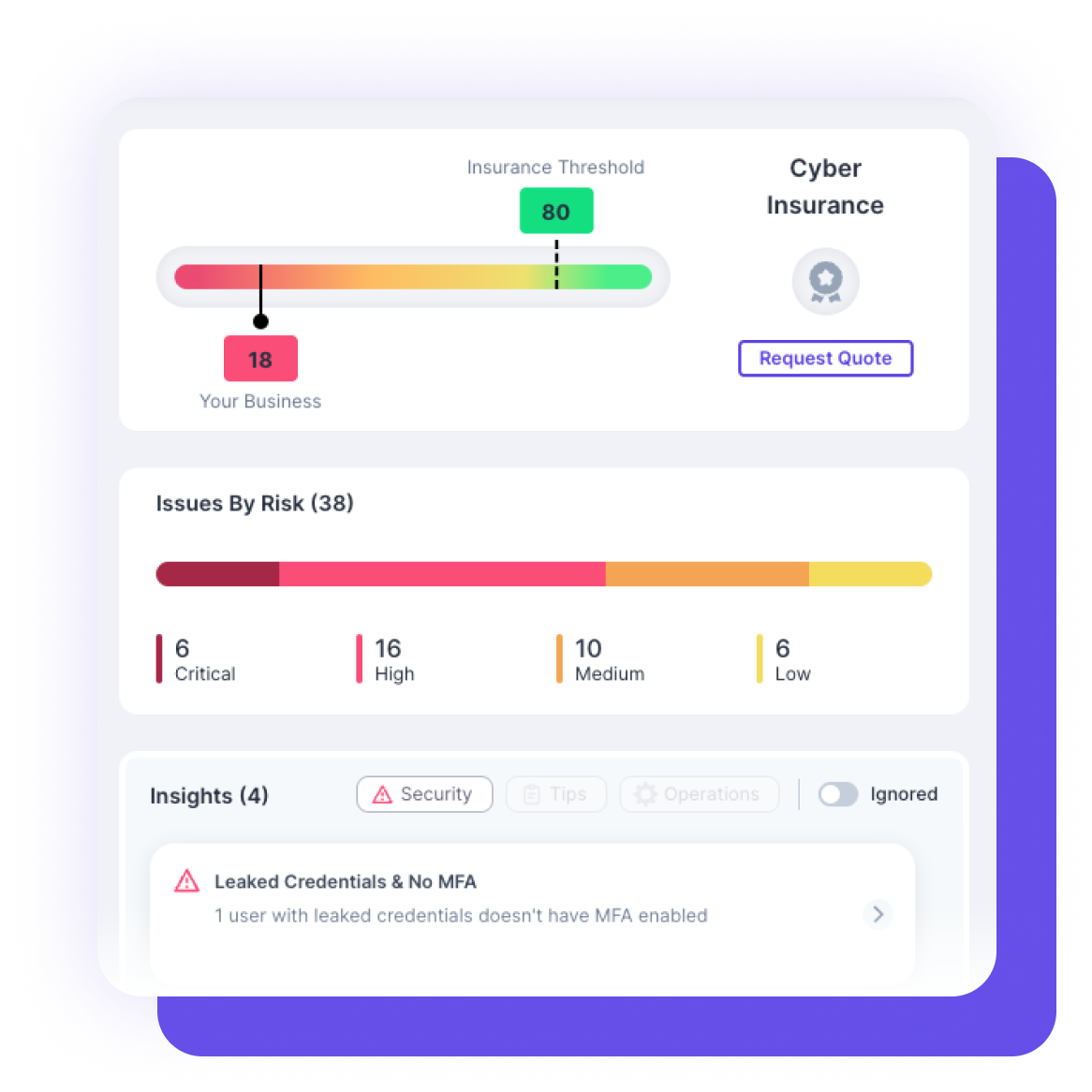
Guardz delivers the relevant alerts and insights to system admins through issues and alerts to enable timely responses and communication with the relevant parties.
The Guardz remediation options vary according to the findings but empower admins to implement automated resolutions or follow detailed playbooks to solve the issues manually.


We believe in taking a comprehensive approach to cybersecurity. Our holistic protection encompasses all layers of defense, providing a unified shield against threats and vulnerabilities, ensuring your organization’s security is robust and thorough.
When it comes to managing multiple clients, it can be overwhelming to address every potential threat. Guardz enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
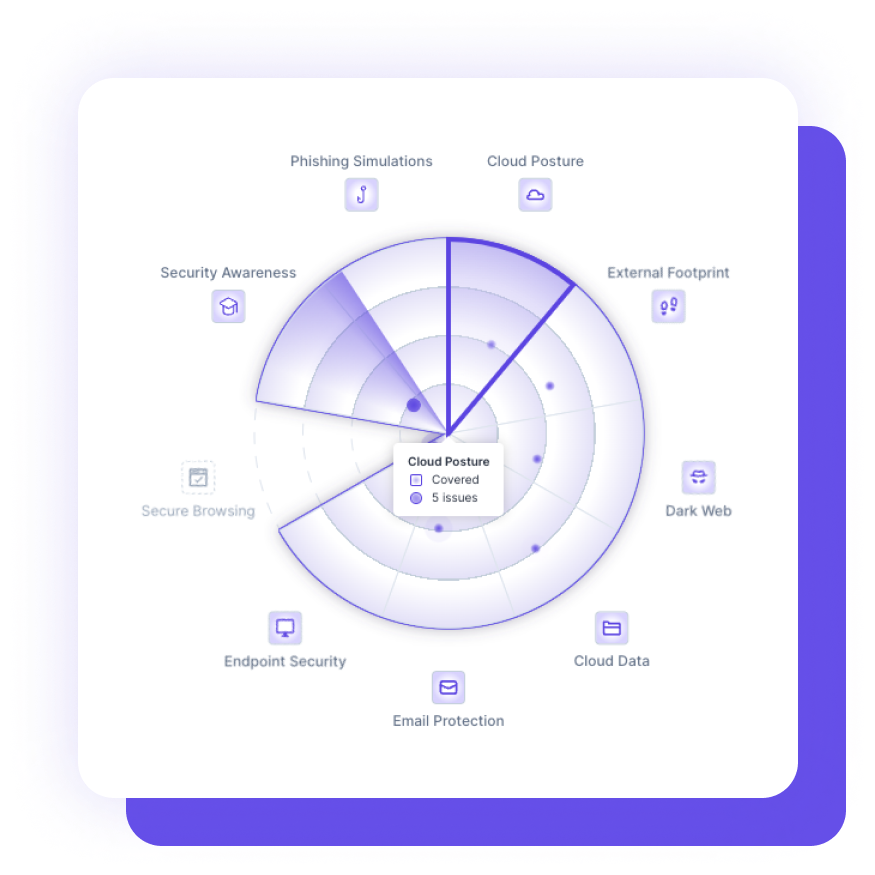


The Guardz managed security platform protects your business or clients from all attack vectors, including email, devices, external exposure, cloud apps, employee awareness, browsers, and more, ensuring that your security is resilient to any threats that may come your way.

Guardz takes advanced enterprise-level technology, democratizes securing your clients with our intuitive interface, and provides easy-to-use and automated playbooks that enable you to quickly detect, prevent, and respond to cyber threats.
Save up to 75% of your cybersecurity costs. Guardz offers tailored security measures that combine essential security tools into a single platform, so that it aligns with your budget and needs, providing an efficient way to mitigate cyber risks without breaking the bank.

Endpoint security refers to the measures taken to protect electronic devices, from potential risks and vulnerabilities that can compromise the confidentiality, integrity, and availability of data stored on them.
By regularly checking for software updates, reading security news and blogs, and by adopting solutions like Guardz that will alert you if any threat arises.
No, there are currently no limits on number of devices or number of organizations supported in the Guardz MSP dashboard.
Guardz admins can distribute the device agent via RMM tools in an automated fashion or send emails for users to manually download and install on their computers
Guardz supports Windows and Mac devices.
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

