Streamline cloud data protection and permission visibility to reduce the risks of intentional or accidental data exposure.

With an innovative solution and multi-layered approach, Guardz ensures that cloud data are always up-to-date, protected against the latest cyber threats, and insured to mitigate the financial risk in the case of a breach.
Rest assured that employee and clients’ cloud apps are secured with high-end cyber technology accessible to all businesses.






As more businesses are shifting to cloud-based applications, cybercriminals are also adapting their tactics to exploit the vulnerabilities that exist in these environments.
As more and more businesses are shifting to cloud-based applications, cybercriminals are also adapting their tactics to exploit the vulnerabilities that exist in these environments.
Unauthorized access to confidential company data end systems can occur in the cloud due to weak security measures, poor configurations, or lack of MFA.
The ease of cloud collaboration also increases the likelihood of data-at-rest exposure through intentional or unintentional data sharing.
Risky configurations in essential cloud apps can reduce the cloud security posture and lead to avoidable breaches.
Using third-party applications or services can add vulnerabilities to cloud data if these services are not secured or the third-party provider suffers a security breach.
Expired, suspended, and inactive guest users can leave a cloud environment at risk as these users can have any level of permission and go unmanaged.
Granting cloud access permissions often disregard the principles of least privilege, resulting in excessive authority and increased risk.
Once threat actors gain access to a cloud environment, there is little to stop them from exfiltrating data or manipulating their way through other systems.
Guardz manages access to files and folders using best security practices. If confidential data is shared or made public, an alert is sent to the IT admin.
Guardz generates alerts in the platform after scanning org-wide Multi-Factor Authentication (MFA) enforcement as well as checking individual user compliance.
Guardz scans the current authentication, access and data control settings and analyzes the SaaS posture to recommend areas of improvement.
Guardz applies machine learning capabilities to reduce targeted hacks and insider threats typically seen via failed logins, geo-location, and anomalous user behaviors.
Guardz detects third-party apps used by employees or clients and scans Google and Microsoft accounts for excessive permissions granted to these apps, revoking them via API.
Programmatically resolve cloud app issues by forcing secure authentication, suspending users, and modifying sharing permissions, while enhancing productivity.
Via public APIs of popular sanctioned cloud applications we conduct a proactive scan of the current settings, security configurations, user activity logs and token grants.
Output from the API scans get run through our internal engine to conduct a risk analysis and focus attention towards misconfigurations, questionable security settings, high risk users, and unsanctioned cloud apps
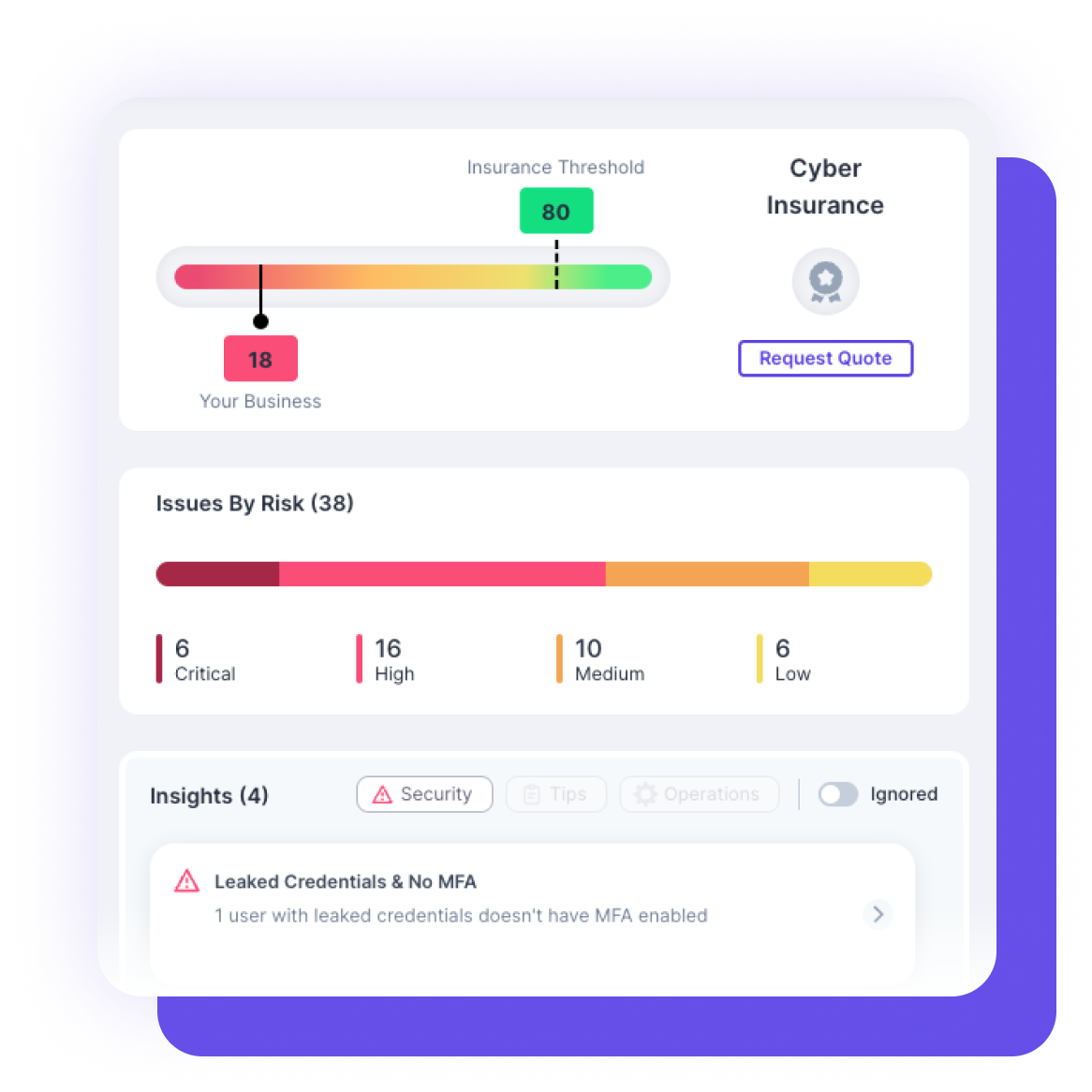
Once an incident has been identified, an alert will be sent along with an issue highlighted in the dashboard.
Our auto-remediation tool enables programmatic fixes for simplified resolution, in addition to manual guidance based on industry best practices.
There is an option to initiate security awareness campaign to users that triggered issues.

We believe in taking a comprehensive approach to cybersecurity. Our holistic protection encompasses all layers of defense, providing a unified shield against threats and vulnerabilities, ensuring your organization’s security is robust and thorough.
When it comes to managing multiple clients, it can be overwhelming to address every potential threat. Guardz enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
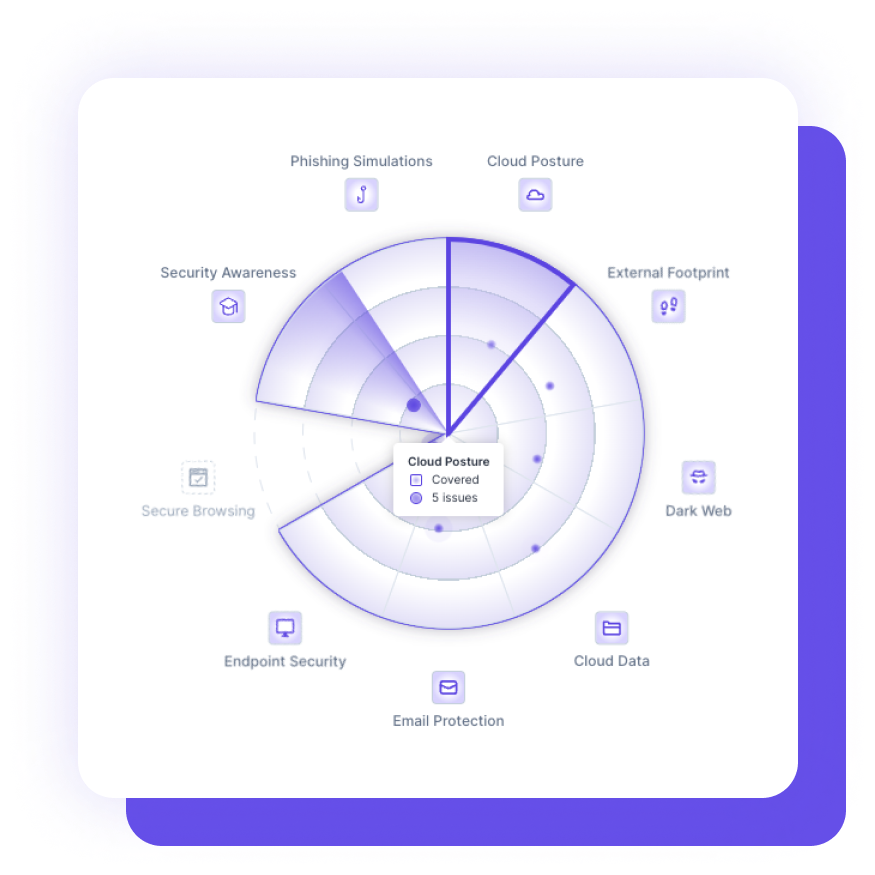


The Guardz managed security platform protects your business or clients from all attack vectors, including email, devices, external exposure, cloud apps, employee awareness, browsers, and more, ensuring that your security is resilient to any threats that may come your way.

Guardz takes advanced enterprise-level technology, democratizes securing your clients with our intuitive interface, and provides easy-to-use and automated playbooks that enable you to quickly detect, prevent, and respond to cyber threats.
Save up to 75% of your cybersecurity costs. Guardz offers tailored security measures that combine essential security tools into a single platform, so that it aligns with your budget and needs, providing an efficient way to mitigate cyber risks without breaking the bank.

Cloud data protection is a set of policies and technologies designed to protect cloud applications and data from unauthorized access, use, or modification.
Cloud Data Protection works by analyzing user activity and behavior within cloud applications to identify and prevent threats. It uses machine learning algorithms to detect anomalies and potential security risks, and can apply policies and controls to protect data and resources.
As more organizations adopt cloud-based solutions, it becomes increasingly important to secure these solutions from cyber threats and attacks. Cloud App Security provides features such as data encryption, access control, and threat detection to ensure that cloud-based data and applications are protected from unauthorized access and cyber threats.
By understanding your cloud security requirements, regularly monitoring and auditing your cloud environment, and using multi-factor authentication, you can significantly improve your cloud security posture.
If developed and implemented properly, cloud applications can be trusted to keep your data safe. Therefore, it is essential to choose a reputable cloud provider and use security applications that are regularly updated and maintained to ensure the highest level of security.
To choose the right cloud data protection for your organization, consider your specific security needs, the type of cloud environment you use, the level of technical expertise required to use the application, and any budget constraints.
Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.


Demonstrate the value you bring to the table as an MSP and gain visibility into your existing or potential clients’ external postures.
This guide provides you with innovative strategies and expert insights to elevate your MSP business, strengthen client trust, and stay ahead of ever-evolving threats.

