Protecting sensitive and confidential information from unauthorized access, sharing, or loss is a critical mission It incorporates a combination of tools, policies, and procedures that function collaboratively to detect, monitor, and prevent the unauthorized transmission or extraction of data from multiple users and cloud app providers.
The Guardz Cyber Intelligence Research (CIR) team is back and invites all MSP security professionals to explore the findings that clearly emphasize why every SME must protect their data.
A Closer Look at Cloud File Exposure
In our modern, digitized world, cloud storage provides universal data access from any device, anywhere, anytime via the internet.
Google Workspace, Microsoft 365, Dropbox and etc. have become favored solutions for SMEs, courtesy of their seamless integration of productivity tools and robust cloud-based storage capabilities. For instance, Google Workspace presents a comprehensive suite of collaborative applications, including Gmail, Google Drive, Google Docs, Sheets, and Slides. These tools facilitate real-time collaboration and document sharing amongst teams.
However, this sharing is not without its pitfalls. A misconfiguration of cloud storage permissions or files inadvertently made accessible to the public can spark major cybersecurity incidents.
One of the most significant threats is unauthorized access. This occurs when sensitive data becomes available to malevolent actors, potentially leading to data breaches, identity theft, and financial fraud.
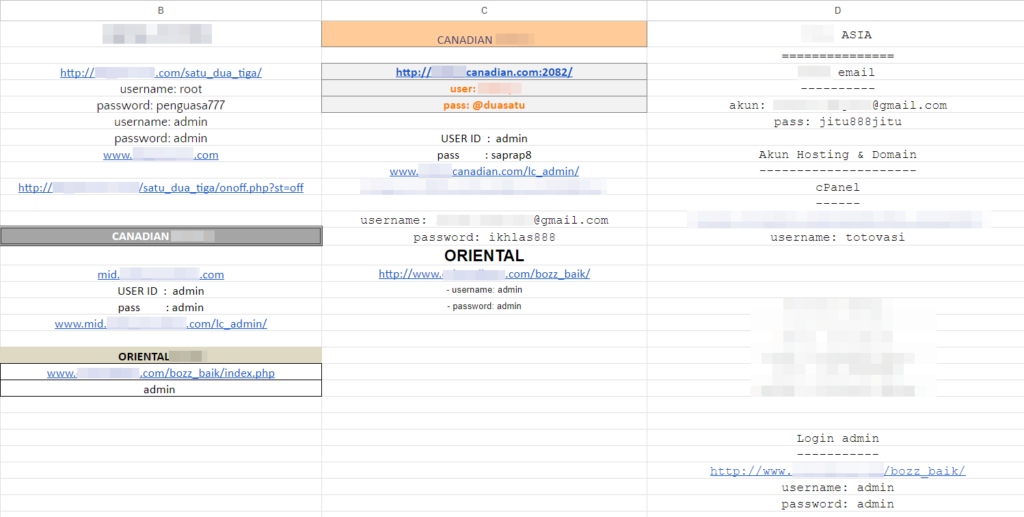
Guardz researchers identified a spreadsheet of an online business that manages its admin credentials in the Google sheet above that is completely exposed to the public. Identifying this valuable information and taking control of all the accounts is possible for any malicious actor.
In a matter of proper cybersecurity education, which Guardz highly advocates, it’s also an example of the bad practice of using the default usernames and passwords like admin: admin to core business accounts.
To summarize, as cloud computing continues to transform data storage, it becomes critically important for MSPs to ensure that organizations prioritize robust security measures and enforce stringent access controls. This will mitigate the risk of exposing files to the public – a potential risk that may lead to catastrophic fallout.
The Silent Danger of Misconfiguration
Misconfigured servers represent a ticking time bomb in the realm of data security. Oftentimes, system administrators may overlook or underestimate the importance of secure configurations, leaving ports, protocols, and services open to the public without proper authentication or access controls.
As a reference, one notorious case serves as proof that not only misconfigured servers can lead to data loss but also a full company closure. In 2019, marketing company Verification.io left a publicly facing server with the database without a password and resulting in 763 million records of personally identifiable information (PII) being exposed.
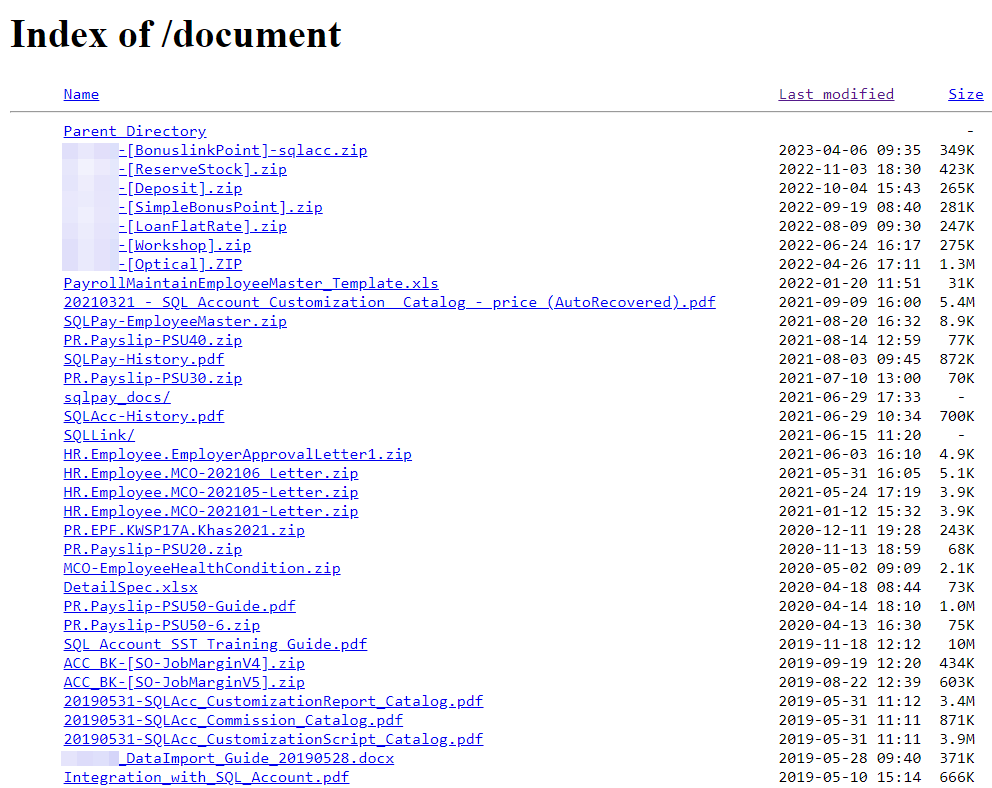
The Guardz research team found an open directory of an accounting software company that has over a hundred internal files completely exposed to the public. Also, in this case, to maintain an affected company’s privacy, we redacted some parts of the file names.
However, even after redaction, it’s possible to understand that the exposed information contains archives with HR and financial information.
Multiple factors contribute to the prevalence of misconfigured servers. Human error remains one of the primary culprits, as even the most experienced system administrators can inadvertently overlook certain settings or fail to keep up with the latest security best practices.
Moreover, pressure to deploy services quickly and efficiently, especially in fast-paced business environments, may lead to shortcuts and hasty configurations, leaving vulnerabilities undetected.
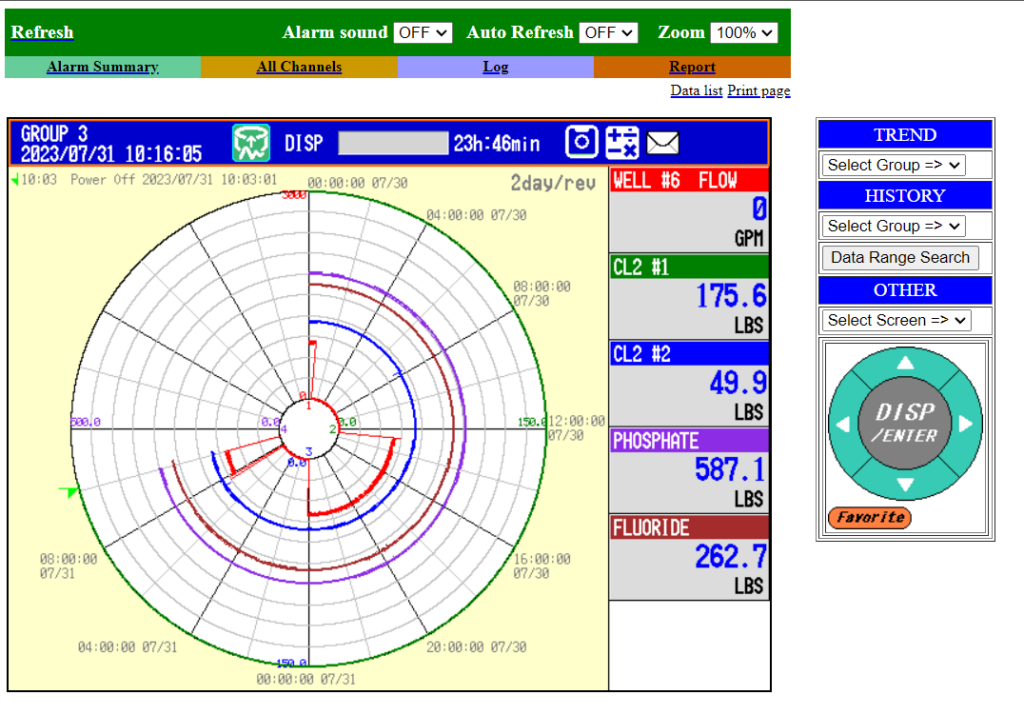
This is also an excellent time to point out that SMEs providing industrial services are also susceptible to the same cybersecurity scenarios.
Our researchers discovered a publicly exposed ICS (Industrial Control System) of a US-based business capable of executing different inputs remotely. Aside from this example, there are a number of other fully exposed ICSs that belong to a variety of business types that can be exploited by cybercriminals or nation-states on a daily basis.
Credentials Leakage
The majority of SMEs use at least a few third-party vendors to enhance their efficiency. Setting up an account with these vendors usually requires an email address and password.
Regrettably, submitting your credentials to a third-party vendor puts you in a vulnerable position if they are not stored securely. In a previous article, the Guardz team reported the discovery of a compromised user database that contained unencrypted passwords and other Personally Identifiable Information (PII).
Consider the following stats: 70 percent of internet users reuse their passwords; 100 million people use ‘123456’ as their master password, and on average, 20 compromised databases are leaked daily on the Dark Web.
Password recycling, or using the same password across multiple online accounts or services, may appear practical, but it introduces significant security risks. Here’s why:
Credential leakage refers to the exposure or theft of login credentials like usernames and passwords, typically resulting from data breaches or suboptimal storage practices. This sensitive information may land in the hands of cybercriminals, who can use it to access unauthorized user accounts on various platforms or systems.
These cybercriminals can utilize the leaked credentials to attempt logging into different online services or platforms. Alarmingly, if employees commonly reuse passwords across multiple accounts, attackers might successfully get into corporate email addresses or seize control of a company’s social media accounts.
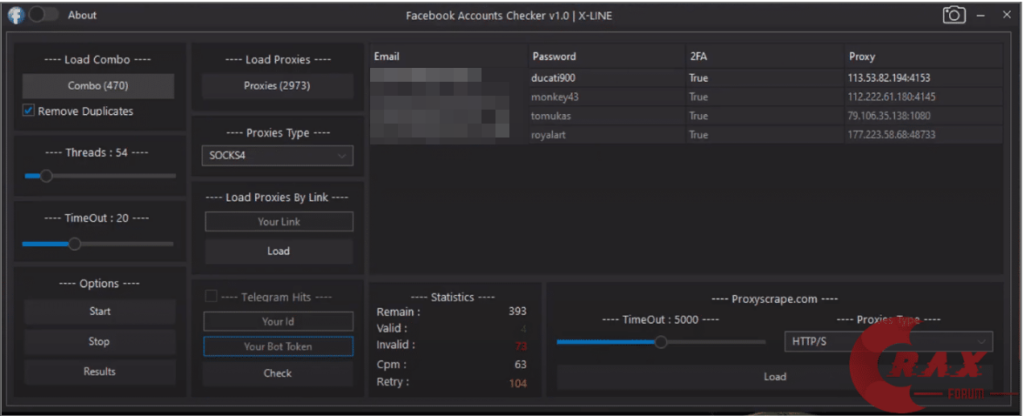
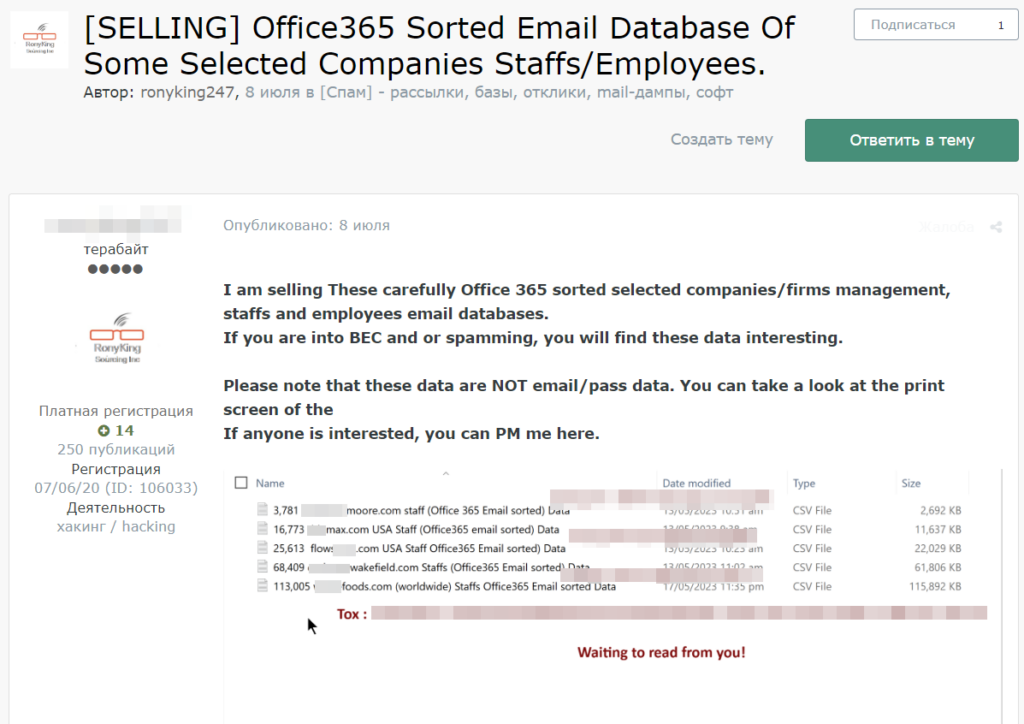
To emphasize why MSPs should monitor this use case as part of DLP practice, Guardz CIR presents an example of a black-hat tool that, in a fully automated mode, will perform a credentials-stuffing attack.
Credential stuffing is an attack technique, in which cybercriminals use automated tools to try leaked credentials across multiple websites, hoping that users have reused their passwords. When a match is found, they gain unauthorized access to the compromised accounts.
Email Forwarding Rules
An email forwarding cyber attack is a devious scheme where attackers gain unauthorized access to a victim’s email account and silently set up forwarding rules to divert correspondence to an external email address controlled by the attackers.
The victims are often unaware of this malicious activity, as the attackers maintain access while subtly siphoning off valuable information and sensitive data from their emails.
Threat actors can use compromised employee accounts for several malicious purposes, including reading emails in a user’s inbox, forwarding emails to external recipients, sending phishing emails, impersonating the CEO or other high-rank position, etc.
Guardz researchers found dozens of threads on the Russian underground forum “Exploit” that target corporate email addresses. We would also like to raise the alarm that all of the samples provided by the threat actor targeted commercial companies that fall into the SME category.
Summary
This blog highlights the significance of DLP both for MSPs and SMEs, outlining the key reasons why they should care about implementing such solutions.
Firstly, it delves into the rising cyber threat landscape, emphasizing how data breaches or information exposure can lead to severe data leakage and irreparable damage to a company’s reputation.
Secondly, the blog underscores the password reuse trend and how it’s connected to future business email compromises that can lead to email forwarding attacks.
Thirdly, it explores the growing trend of “Attack-as-a-Service” tools and other illicit offers widely available on major underground forums.
Guardz holistic protection against data loss starts with our dark web scan and identifying leaked credentials. Security Awareness Training reduces accidental leaks and ensures employees act as the first line of defense by being educated on the various methods of attack. Spear phishing emails are frequently used to target users, and Guardz email protection will identify and quarantine these attacks. Guardz Cloud Data Protection scans all files/folders in a company’s cloud storage or other SaaS apps to identify external exposure and public links. And finally, Guardz endpoint security actively protects against ransomware and other malware designed to exfiltrate sensitive data.
Lastly, by providing screenshots of real-life examples, Guardz highlights how investing in DLP services is a proactive measure that can prevent data breaches, enhance customer trust, and foster long-term business growth and resilience. By caring about data loss prevention, SMEs can embrace the digital era with confidence, knowing that their data is secure and their future is protected.
- Share On:












