The recent reveal of ShadowVault malware in our blog post decidedly piqued the interest of the cybersecurity news community. Keeping up-to-date with the latest developments in cybersecurity is always exciting, and we are delighted to participate and contribute to these discussions actively.
In this follow-up post, Guardz CIR (Cyber Intelligence Research) team decided to leverage the power of AI, much like we do in our phishing protection service, and we asked ChatGPT about additional mac-OS threats that lurk somewhere on the Dark Web.
Motivated by the response, our researchers delved back into the depths of the cybercrime underground to authenticate this lead.
In this article, we will explore additional findings related to macOS, recent developments discovered by our team, and the advanced hacking tactics cybercriminals employ to target Mac devices owned by employees in SMEs. Furthermore, we will elucidate what a “deposit” means in a cybercrime forum and how it relates to our current discussion.
Our mission is to equip MSP security professionals and SME business owners with readily available cyber intelligence to bolster their cybersecurity defenses.
As cyber threats continue to significantly expand and advance in complexity, the need for timely threat intelligence and security education intensifies. We aim for this latest research from our frontline analysts to enlighten and empower our audience.
Insights into the macOS HVNC Tool
Disclaimer: Under no circumstances do we purchase goods or services from Dark Web marketplaces, nor do we promote or assist others in engaging in cybercriminal activities. Our research method is designed solely to deliver threat intelligence and help organizations improve their cybersecurity posture and raise awareness.
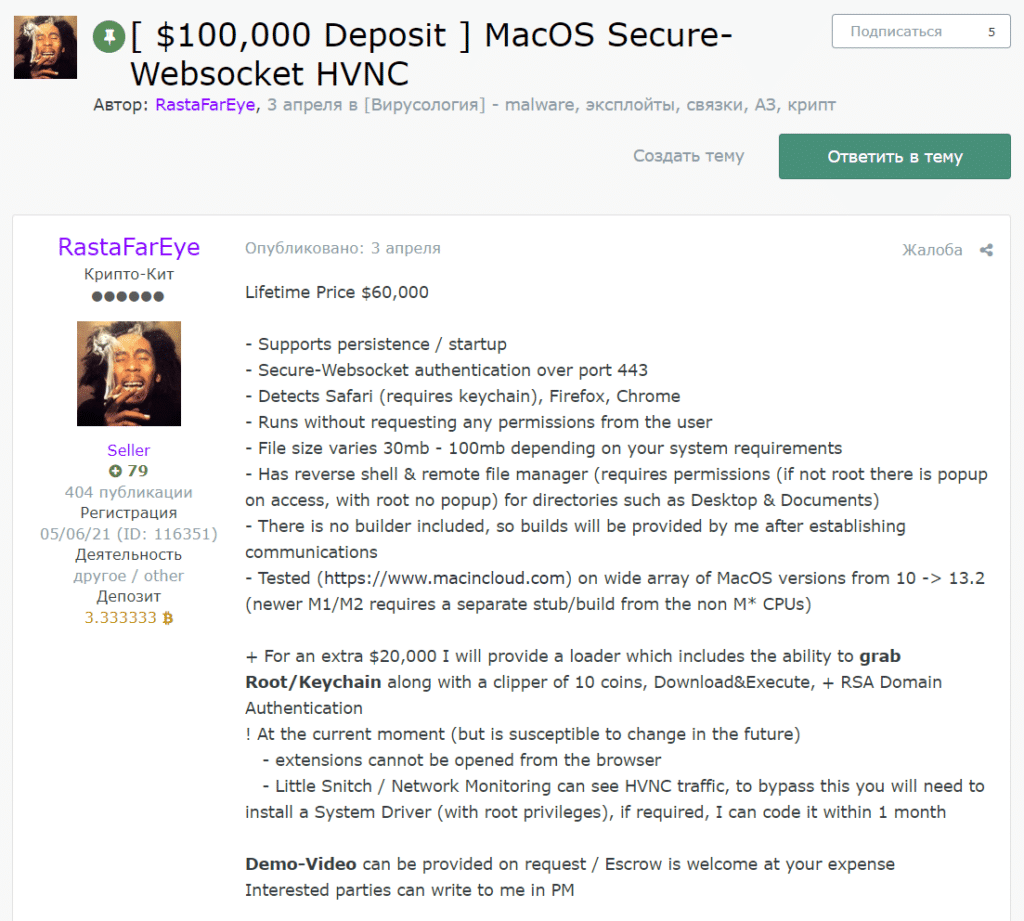
Guardz CIR team delved into the prominent Russian cybercrime forum “Exploit.” Our team discovered another tool available since April 2023, specifically targeting macOS devices owned by SMEs. Notably, the title bears a peculiar “$100,000 Deposit” prefix, a consideration that our team will clarify further in this blog post.

For a lifetime price of $60,000, the threat actor will provide you with a malicious tool that supports persistence, runs without requesting any permission from the user, has a reverse shell plus remote file manager, and was tested on a wide array of macOS versions from 10 up to 13.2.
Besides the $60,000 price tag, the threat actor offers a $20,000 add-on that will deliver more malicious capabilities to the arsenal.
So what is the HVNC, you probably ask yourself? HVNC stands for “Hidden Virtual Network Computing.” It is a type of technique used by cybercriminals to gain unauthorized access to a victim’s computer.
Virtual Network Computing (VNC) is a legitimate technology that allows users to remotely control another computer over a network. It is commonly used for remote technical support or accessing a computer from a different location. In this case, the user is clearly able to see on his/her screen that somebody else controls the workstation and is fully aware of which actions are performed by a third party.
However, HVNC is a malicious variation of this technology used for nefarious purposes. Using Hidden VNC, the attacker can take control of a victim’s computer without their knowledge. It means that the user is completely unaware that there is an intruder that created a new desktop session and just silently joined their computer.
Guardz CIR mapped the key characteristics of HVNC:
- Hidden Operation: HVNC is designed to run in stealth mode, making it difficult for SMEs to detect its presence on their system. This hidden operation allows cybercriminals to maintain access without raising suspicion.
- Persistence: HVNC often includes mechanisms to ensure it remains active even after the system reboots or attempts to remove it.
- Data Theft: The primary purpose of HVNC is to steal sensitive information from an employee’s computer, such as login credentials, personal data, financial information, or other valuable data.
- Remote Control: HVNC allows cybercriminals to control computers remotely, giving them full access to the system.
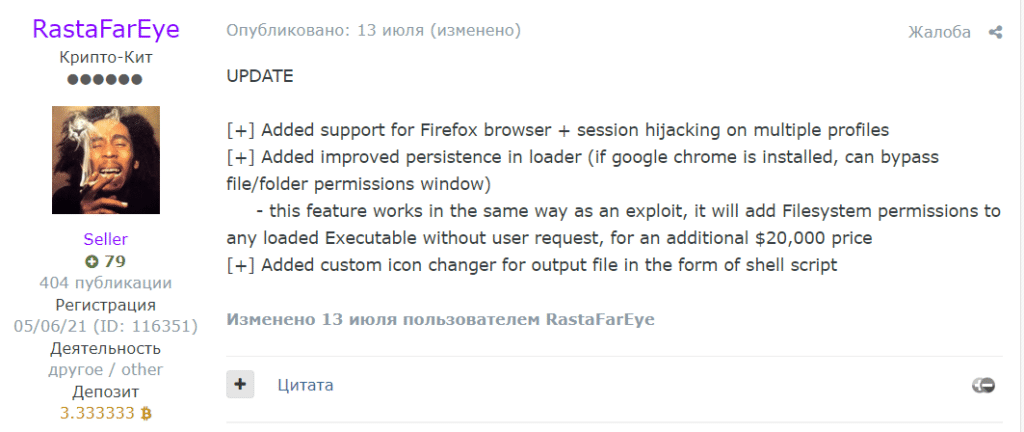
HVNC is typically distributed through various attack vectors, including email attachments, malicious websites, or exploit kits. Once installed on a victim’s system, it establishes a connection to the attacker’s command-and-control server, enabling the cybercriminal to interact with the compromised device. It also appears that this tool has been continuously developed since its initial offering back in April 2023. On July 13, 2023, the threat actor published a follow-up post stating that the tool has undergone some technological updates.
Let’s talk about “RastaFarEye”
RastaFarEye, an active member since May 2021 on the notorious Russian cybercrime forum, already has a track record of significant malicious activity. He has already developed a variant of HVNC for Windows OS, cryptocurrency targeting malicious software, and offers EV (Extended Validation) certificate creation services.

Not only does he have a “Seller” status, a type of achievement that requires approval by the underground forum administration, but RastaFarEye also made a good faith deposit of $100,000.
The $100,000 deposit (that equals 3.33 Bitcoin) helps the other cybercriminals to understand that the person behind this profile is a high-profile actor. This money is kept in the escrow account of the forum administration as a type of underground insurance in case the offered product is not as described in the original post.
A threat actor that deposits such money must be sure that he sells top malware. Otherwise, the administrator has the right to deduct funds from his/her deposit as compensation.
The combination of the “RastaFarEye” background on the forum combined with money that he keeps as a deposit only emphasizes that this threat is real.
Rising Cyber Threats: What It Means for macOS Users?
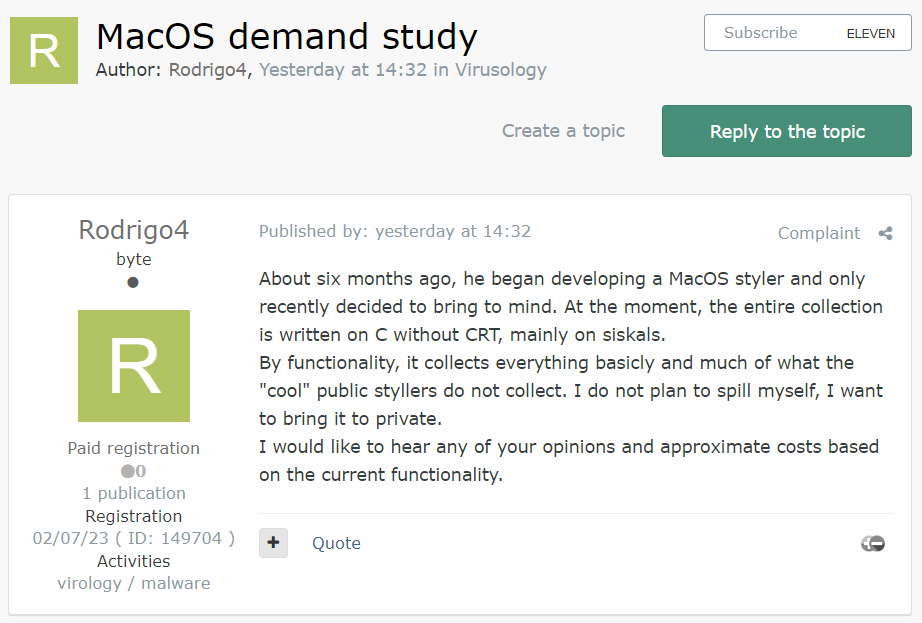
It looks like the macOS-related topic is a subject of interest to other cybercrime forum members. As recently as July 20, 2023, the freshly baked threat actor “Rodrigo4” opened a thread (originally in the Russian language) with the title “MacOS demand case study.”
He shared that for the last 6 months, he has been working on his version of macOS information stealer malware and is willing to offer this to private members.
It still remains to be seen how many other threat actors are lingering in the dark, working on developing malware for macOS devices. Meanwhile, Guardz will continue to monitor this topic and share the findings with the cybersecurity community.
Summary
As with other remote access tools and malware, protecting against HVNC involves employing robust cybersecurity measures. Guardz is here to bring you the latest findings from the closed cybercrime communities and shed light on emerging threats.
We learned that with Hidden Virtual Network Computing (HVNC) it is possible to control a machine without the victim’s knowledge. It’s a known malware module that targets Windows OS devices, but now we see that there is also a shift to macOS machines.
Mac computers and devices are widely used by SMEs due to their reputation for security and usability. As trusted security service providers, all MSPs have a responsibility to stay up-to-date on these new threats and ensure their clients’ Mac devices remain secure.
Though Macs have historically been less targeted by cybercriminals, attackers are now developing more macOS malware. Guardz researchers believe that this kind of tool can be integrated into a variety of “Attack-as-a-Service” cybercrime services that are available on underground forums. Ignoring macOS vulnerabilities leaves SMEs at risk of business disruption, stolen intellectual property, and financial loss.
Looking to boost your MSP revenue? Guardz got your back!
The deposit feature on the underground forums allows cybercriminals to transfer money to the escrow account. This is used as a good faith measure from a threat actor’s side to prove to other members that he offers high-level products.
We also saw that there was a previously unknown cybercriminal that only a few days ago emerged from stealth and declared that he had been working on macOS-related malware for the past half year.
Finally, educating users about the risks of opening suspicious email attachments or downloading files from untrusted sources is crucial in preventing HVNC infections.
Stay tuned for our next blog posts to stay sharp on everything that’s going on the Dark Web and how Guardz uses this intelligence to make SMEs safer.
- Share On:












