Whether you’re an SME business owner, employee, IT professional, or MSP vendor, email is an essential part of your daily communication routine. However, many tend to focus solely on the “inbox” or “sent items” areas of our email accounts.
Have you ever received a suspicious email or out-of-the-ordinary SMS? Do you know how many of these suspicious forms of communication are sent to your team on a daily basis? That’s where the Guardz Cyber Intelligence Research (CIR) team comes in to reveal this often-neglected area of your email account.
You’ll be surprised to discover that you have free Amazon gift cards waiting for you, or when you receive an email claiming that something has happened with your bank account, or even when you’re told that you’re eligible for an inheritance from the royal family.
As technology advances, cybercriminals are increasingly turning to AI as a tool to automate and scale their attacks. AI can be used to automate tasks such as reconnaissance, vulnerability scanning, and social engineering, which can speed up the attack process and increase the chances of success.
For example, AI can analyze social media profiles and other public data to gather information about potential targets, such as their interests, job titles, and network connections. This information can then be used to craft targeted phishing emails or social engineering attacks that are more likely to succeed.
AI can also be used to create convincing deep fake videos or audio recordings that can be used to trick people into divulging sensitive information or transferring funds to fraudulent accounts. These attacks are particularly effective because they exploit the vulnerability of human nature, such as trust and authority biases.
This is where social engineering comes into play- a form of manipulation involving psychological tricks to influence people into taking certain actions or revealing sensitive information. The individuals who leverage this technique are called social engineers, and they are a key factor in the success of modern cyber-attacks. Understanding the tactics and techniques used by social engineers is crucial to defending against such attacks and protecting sensitive information.
Know Your Weaknesses
Social engineering is a successful method of cyber attack due to its exploitation of human weaknesses. The following are common weaknesses that social engineers use:
Trust – Social engineers frequently rely on people’s inclination to trust others. They may impersonate someone with authority, like an IT Administrator or a CEO, to gain trust and access.
Curiosity – People are naturally curious, and social engineers may exploit this by creating a sense of urgency or presenting something that seems too good to resist.
Fear – Social engineers may use fear to intimidate people into taking actions they wouldn’t usually take, such as revealing sensitive information under the impression that failure to comply could result in a forever locked bank account.
Ignorance – Lack of knowledge or awareness of cybersecurity risks is a common weakness that social engineers exploit. They might use technical terms to confuse people or create a sense of urgency to pressure them into taking action.
This is just a small example of our natural weaknesses that can lead us to click on malicious links, believing we received an email from our IT administrator. Another example is downloading an infected PDF file with a tempting title such as “Your Salary Raise” or posing as a bank or other financial institution and claiming that there has been fraudulent activity on the account, urging the victim to provide personal information or transfer money immediately or even executing a wire transfer to a threat actor posing as the company CEO.
Those are tactics, techniques, and procedures that malicious actors use daily to trick and attack SMEs. MSPs must be aware of the existence of these threats and keep themselves up-to-date with the latest social engineering techniques in order to properly secure their clients.
What Are The Latest Trends in Email Phishing?
Email phishing is a social engineering attack that uses fraudulent emails to trick individuals or organizations into divulging sensitive information or taking harmful actions. These emails often appear to be from trusted sources like banks, online retailers, or social media sites and contain a sense of urgency or a call to action that prompts recipients to click on links or download attachments.
These links or attachments may contain harmful software that can compromise a computer or redirect users to malicious third-party websites where they are asked to provide sensitive information like login credentials, social security numbers, or credit card details.
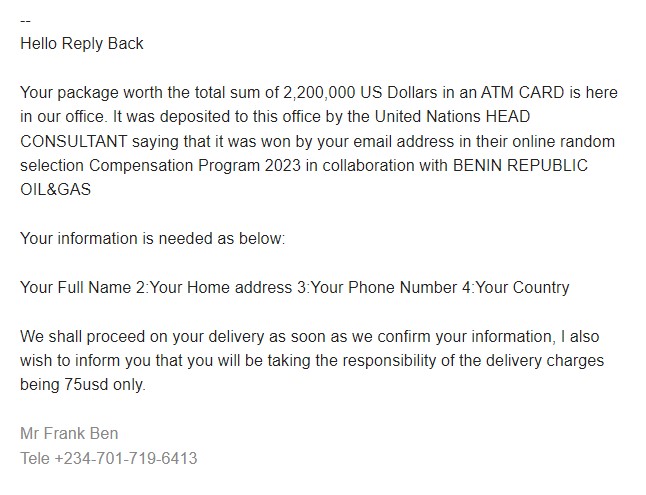
For example, the email below is a typical “spray and pray” phishing email sent to one of our clients. The threat actor used known social engineering techniques to “notify” the employee that a package worth over 2 million USD was deposited by the UN head consultant and that they just needed to pay a $75 delivery fee.
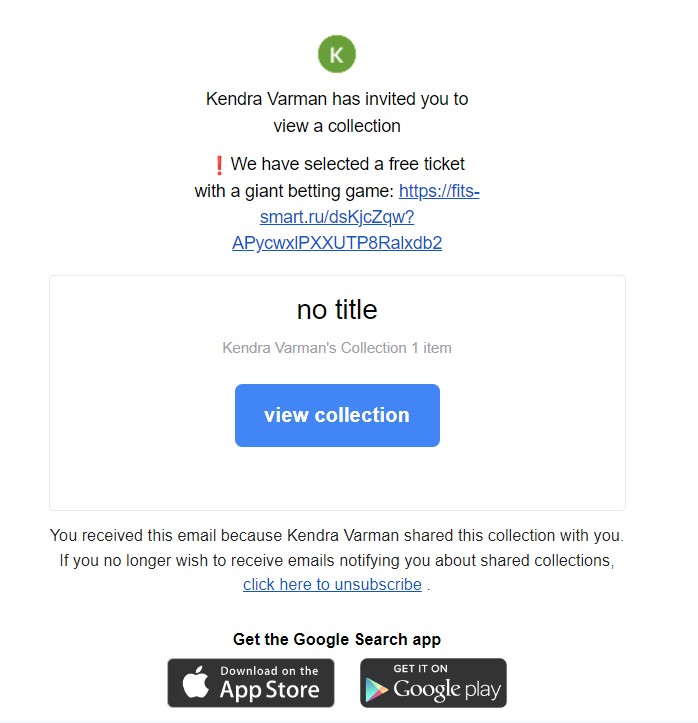
In another case, they received an email that mimics the graphics and design of Google, offering an interesting deal from someone named “Kendra Varman.” The deal promised a free ticket for a popular game, but in order to claim it, we were instructed to click on a link that redirected to a website based in Russia. However, this website was flagged as malicious by Guardz, indicating that it was not a safe site to visit.
When the Dark Web Meets Email Phishing
In the previous blog, “What is the Dark Web and Why Should SMEs Care?”, we covered how cybercrime methods have undergone a democratization process in recent years, with the underground community now open to newcomers who lack high-profile technological knowledge.
In the case of email phishing, you simply need to select your victims and outsource the rest to the malicious actors, who will provide you with the full environment to launch phishing attacks.
For instance, a threat actor who has been active on a Russian cybercrime forum since 2019 offers an A to Z service to set up an email phishing attack that can impersonate an email provider, a retail network, or even a financial institute such as a bank or credit card company.
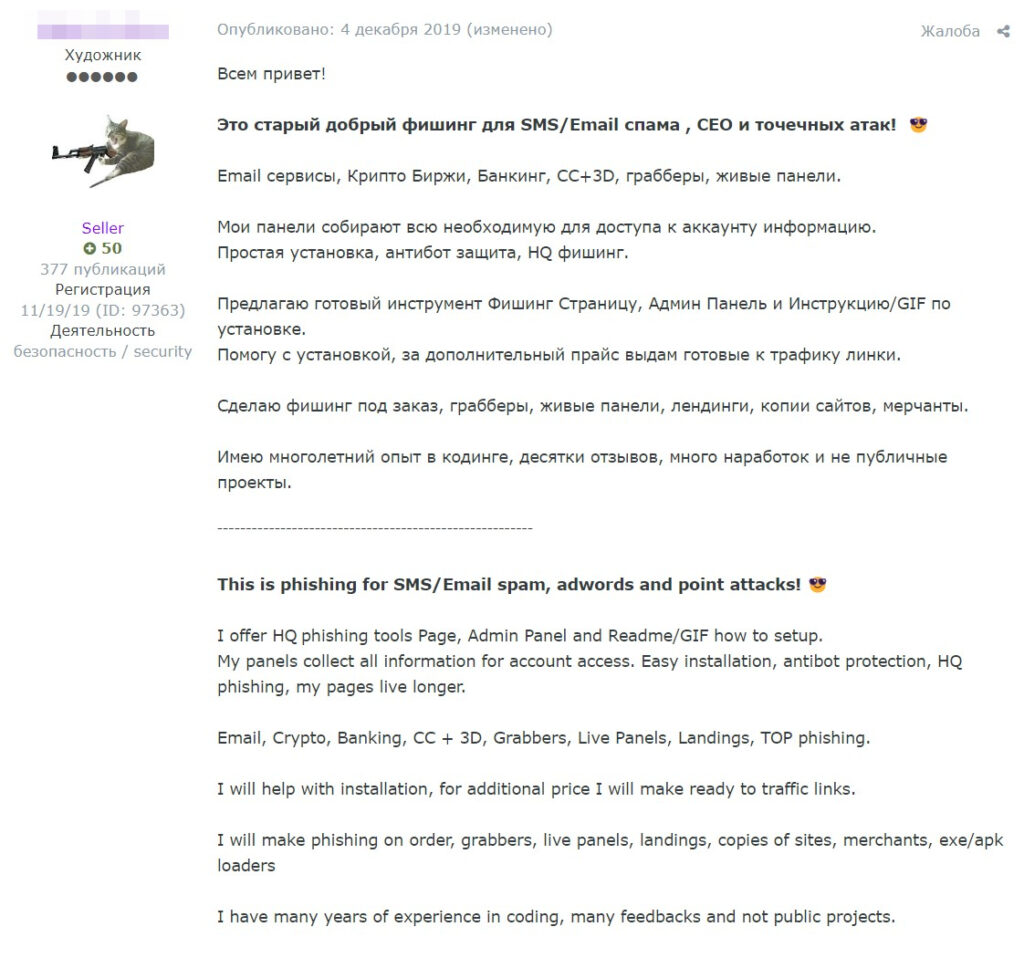
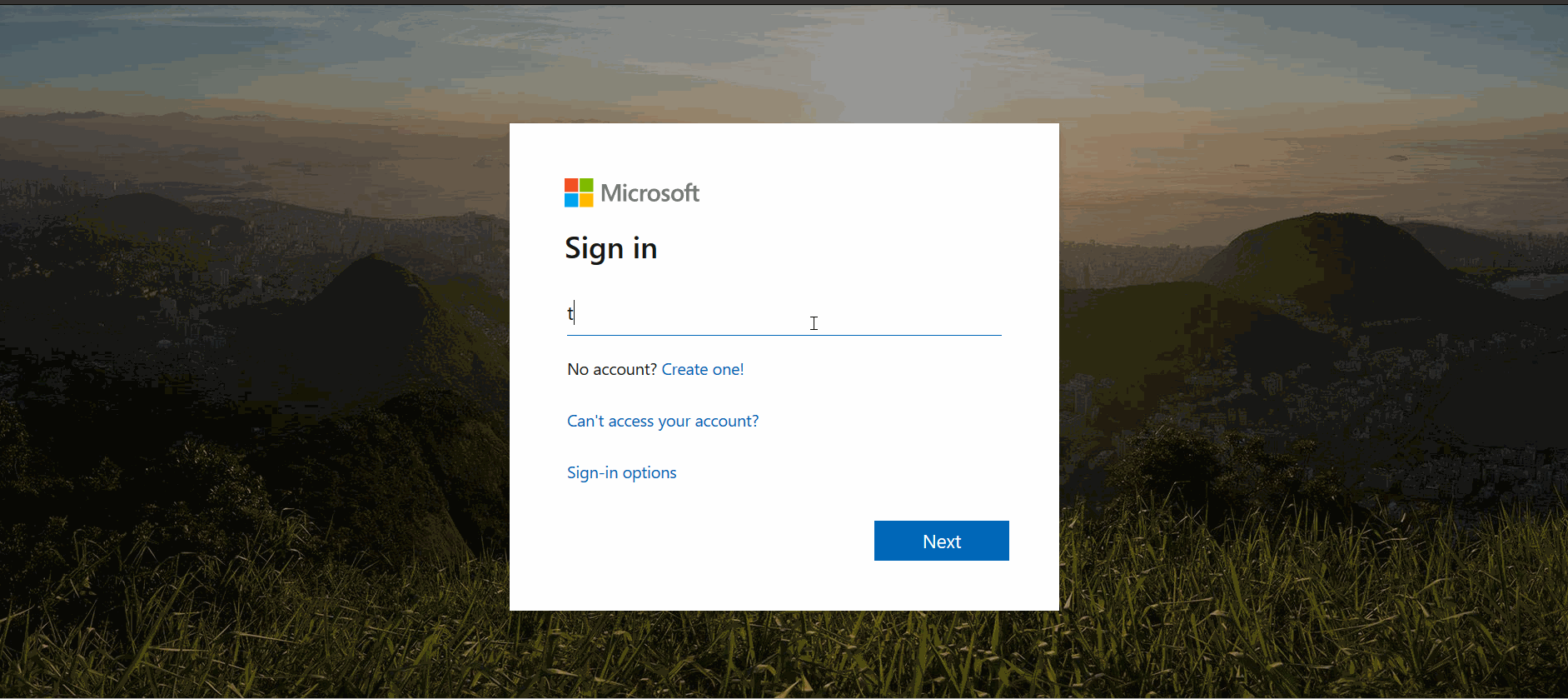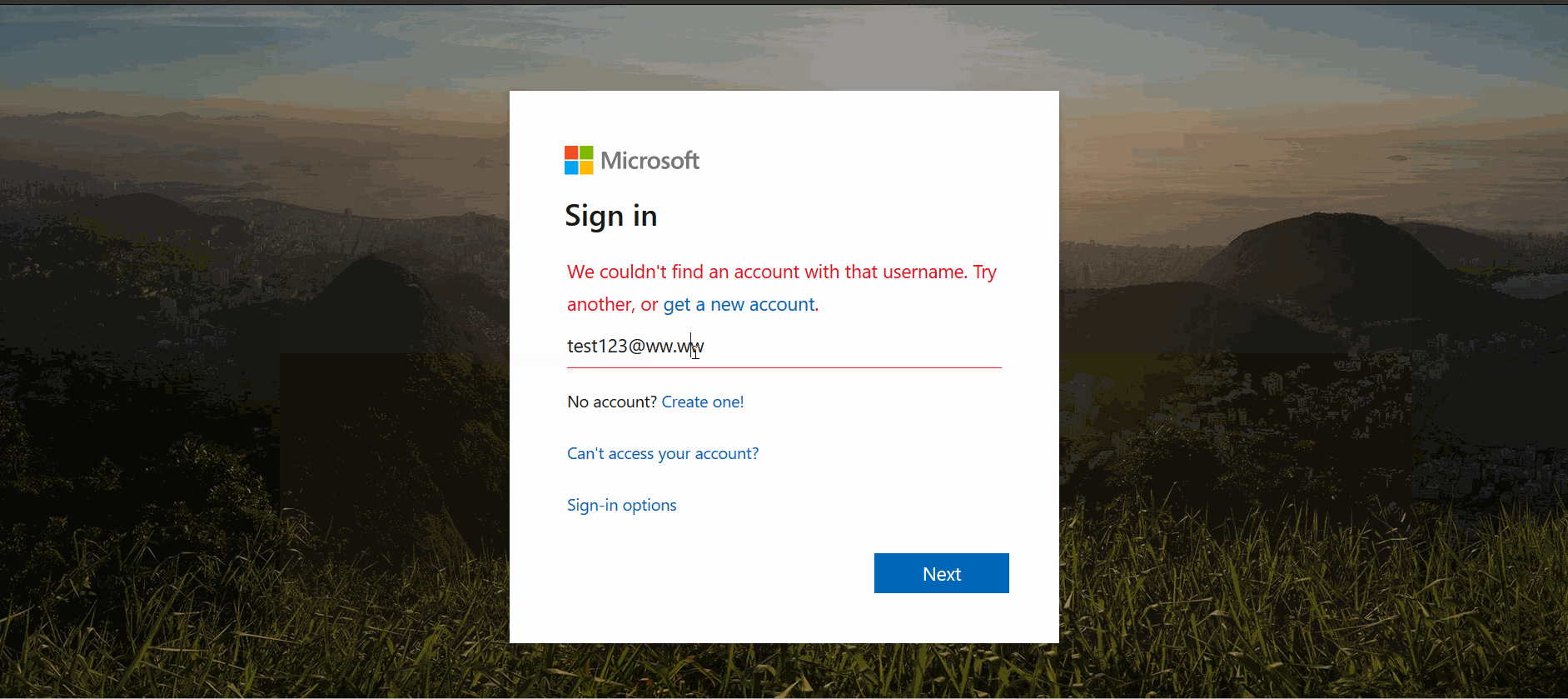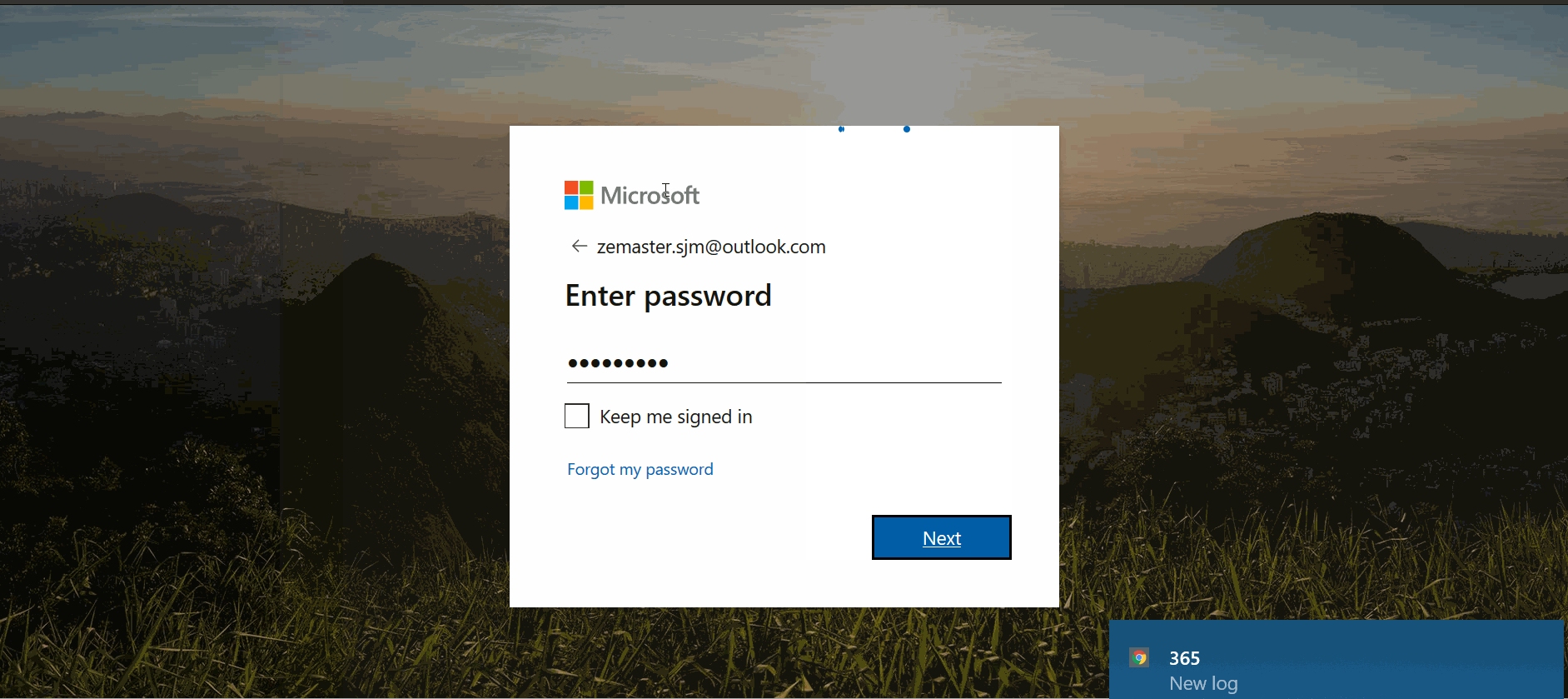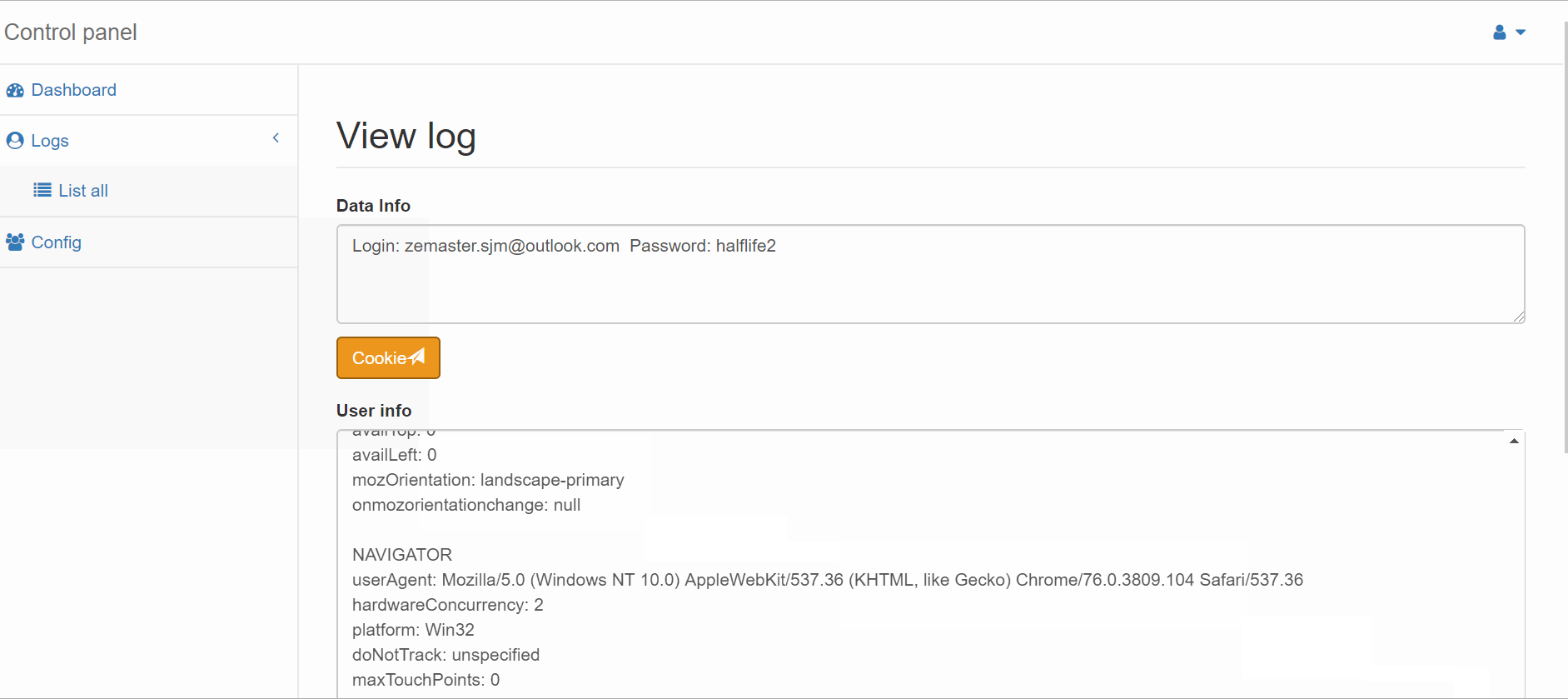
Guardz CIR obtained and analyzed recorded demos of Phishing-As-A-Service provided by the threat actor and blocked it automatically for our clients.
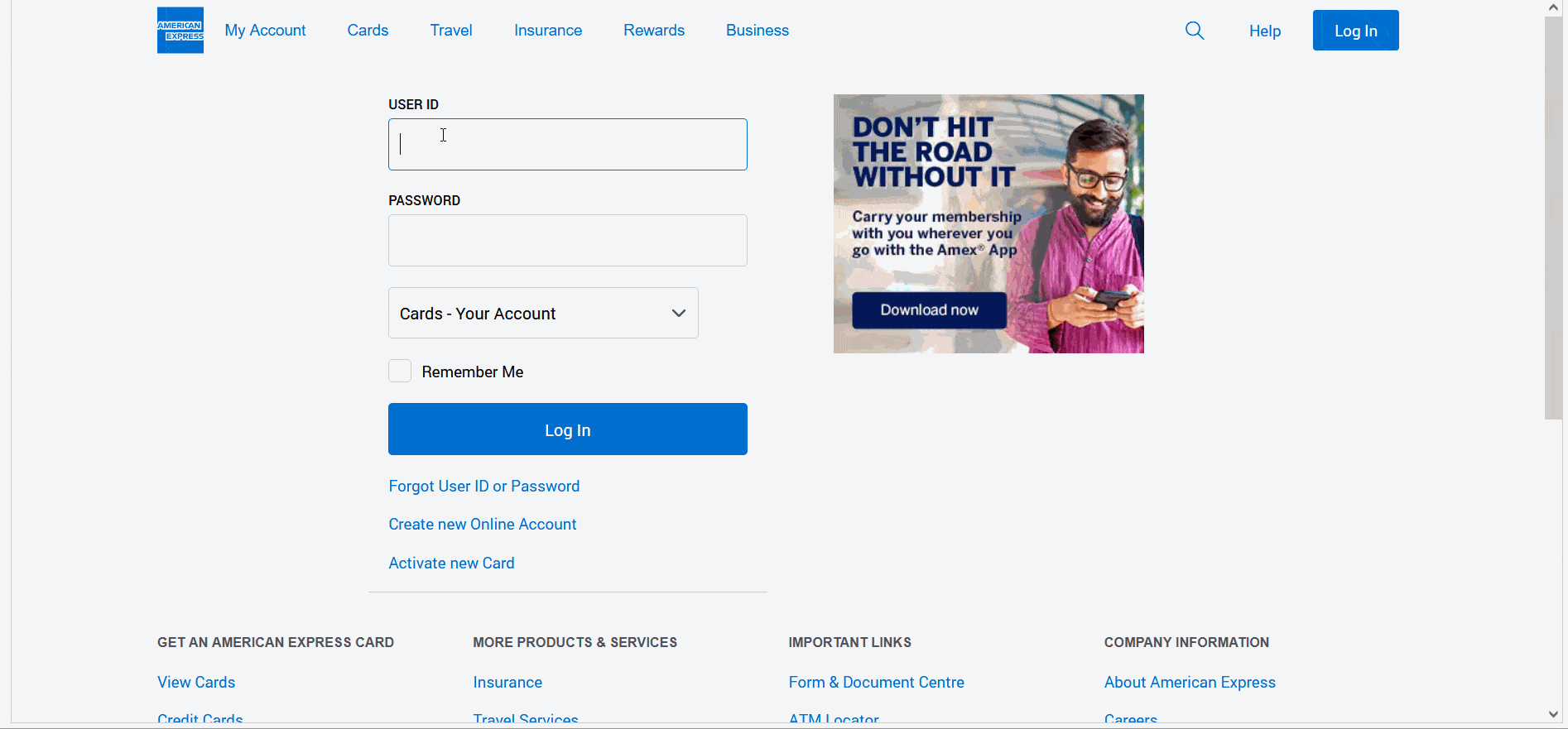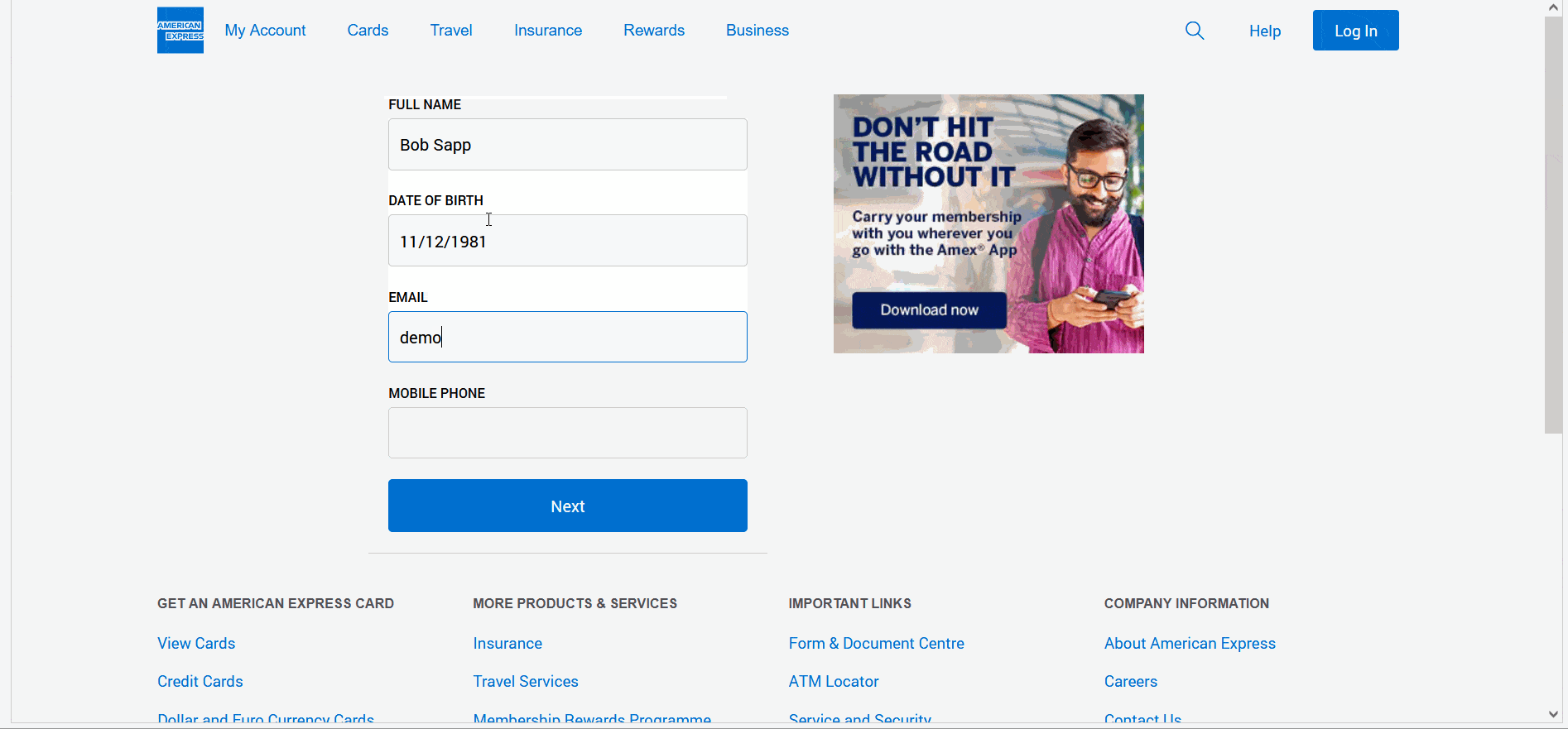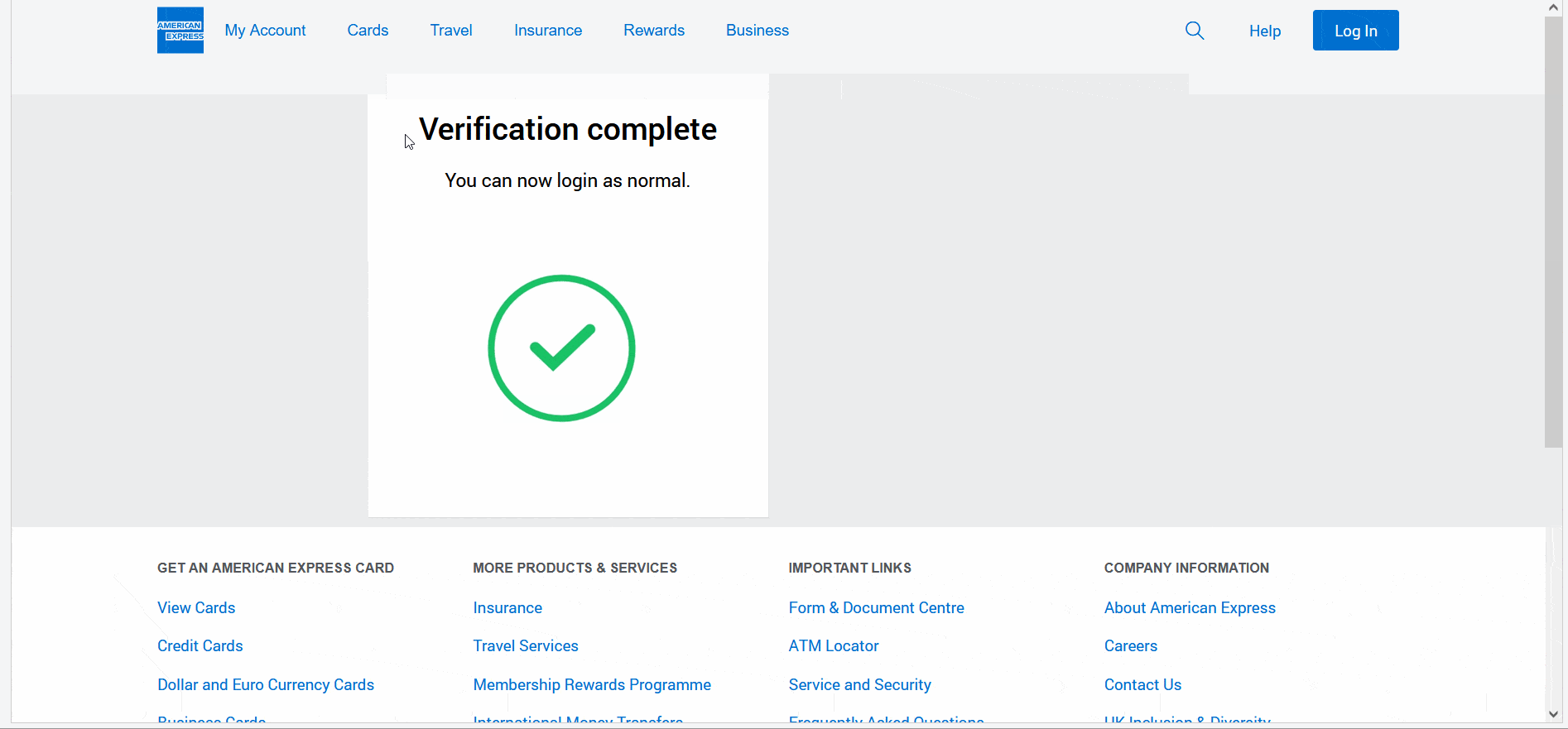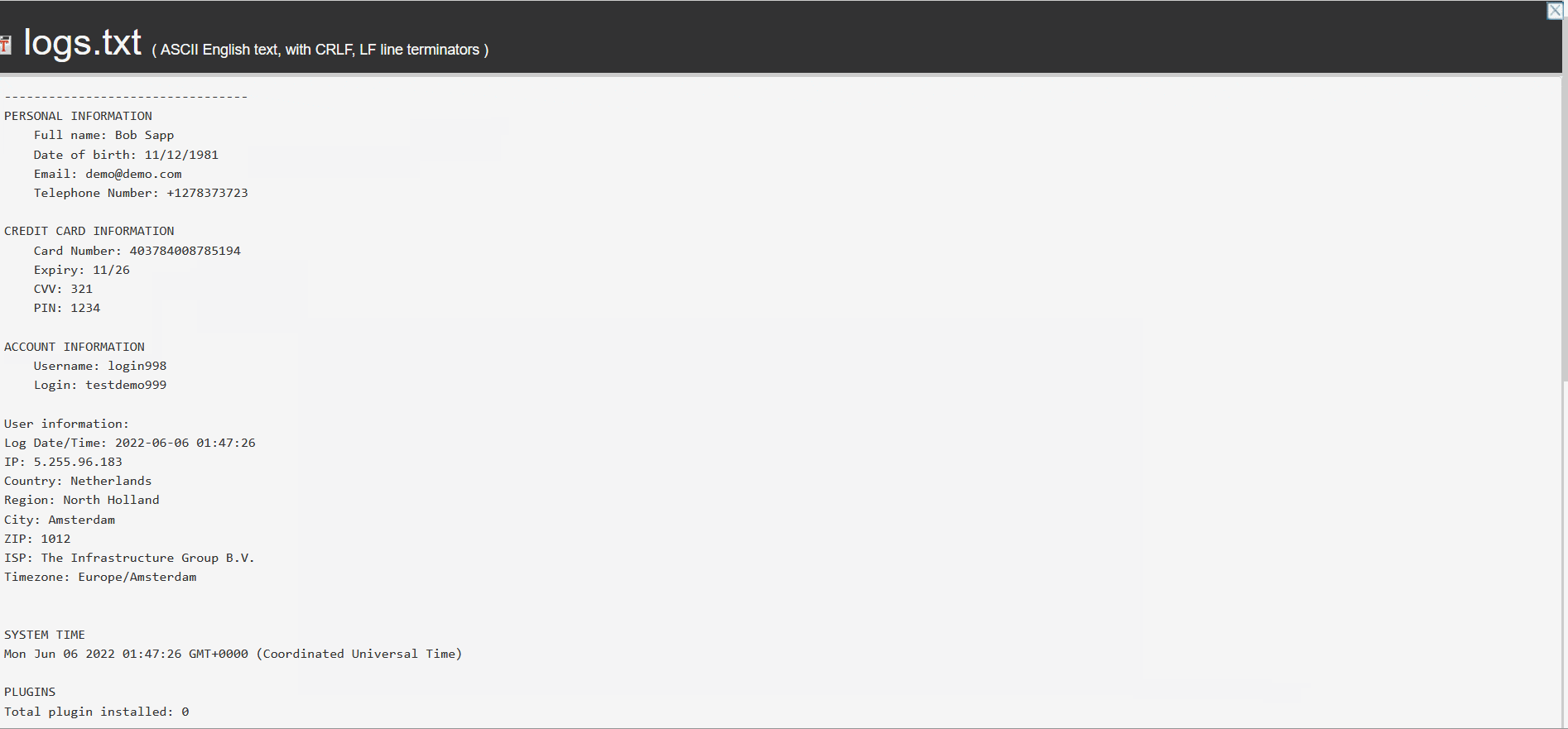
The kit that mimics the AMEX website initially tricks the victim into entering their user identification and password. However, suddenly, due to a “policy update” procedure, the victim is prompted to provide their full name, date of birth, email address, and phone number.
To “complete verification,” the last step is to provide a full credit card number and expiration date. After entering all the required information, the victim receives a “verification completed” notification, and the threat actor shows how the data is captured on their side.
When it comes to the Office 365 kit, which is widely used by many companies worldwide, the victim is only tricked into entering their email address and password. The threat actor then shares how the freshly compromised data is displayed on their malicious dashboard.
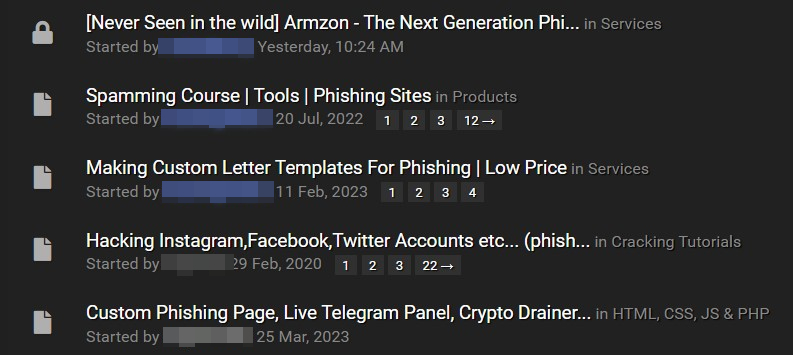
However, suppose you don’t have access to the Russian underground community. In that case, there are also English-language cybercrime forums that offer various phishing tutorials and illicit services, such as developing tailored phishing pages.
Smishing is Here to Stay
Receiving phishing emails is not the only way to fall into an attack. Cybercriminals often use short malicious messages delivered directly to your mobile phone via SMS.
Due to the 160-character limit of a single SMS, cybercriminals have limited space to write long texts and often exploit human fear or urgency. For example, the SMS may contain a message that tax authorities are currently filing a legal case against you, but by clicking on the link provided, you can “solve the problem.”
In another case, you may receive an update from your local post service stating that one of your packages requires an additional fee to be released from the warehouse. The message may state that the fee must be paid within the next 24 hours. Otherwise, the package will be destroyed.
Tips on How to Spot Suspicious Content
We know that every social engineering attack prey on human weaknesses and manipulates individuals to commit a certain action. To help you spot and identify potential phishing attacks, here are four tips:
Be wary of unfamiliar email senders – always verify that you have received the email or SMS from an address or number you know and trust.
Watch out for urgency or unusual requests – use your common sense and analyze the situation. If you have never been asked to transfer a large sum of money to an unknown bank account before, it may be a phishing attempt.
Be cautious of links or attachments – hover your mouse over suspicious areas that urge you to click. Check if you are familiar with the domain address in the link before clicking.
Trust your gut feeling – if you are unsure about an email or message, it is better to be safe than sorry. Consult your Managed Service Provider (MSP) or Guardz cybersecurity professionals for further assistance.
But more importantly, it is to have the right security stack to protect your users from the next phishing attack that can cause serious damage to your business and clients.
Guardz aims to create a safer digital world for all businesses, empowering MSPs and IT professionals to proactively secure their clients and businesses with a comprehensive set of advanced cyber protection features, including email security, cyber awareness, device protection, cloud application security, external risk assessment, and cyber insurance coverage in a single pane of glass.
- Share On:












