Guardz is excited to launch a new blog series where we will explore various cybersecurity topics related to small and medium enterprises. Throughout the series, we will dive into the different aspects of threats from the Dark Web, including an overview of how it is becoming increasingly easy to access underground sources.
Whether you are an enterprise owner looking to learn more about protecting your company or an IT expert seeking to expand your knowledge, this series is designed to provide valuable insights and actionable tips to help you in your journey.
To make this possible, Guardz has launched its very own Cyber Intelligence Research team (CIR) led by top cyber security and intelligence professionals. This team is dedicated to researching existing and emerging cyber threats that target small and medium enterprises.
So, sit back, grab a cup of coffee, and join us on this journey as we explore in this first blog in this series about how the Dark Web became a paradise and go-to place for cybercriminals.
What is the Deep and Dark Web?
The internet is a vast network of information, and certain parts are not easily accessible or visible through conventional search engines like Google or Bing. These parts are known as the Deep and Dark Web.
- The Deep Web refers to content that is not indexed by search engines and is not accessible through traditional means.
- On the other hand, the Dark Web is a subset of the Deep Web that is intentionally hidden and requires specific software or authorization to access.
The Dark Web is based on the TOR network. TOR, short for The Onion Router, is a free and open-source software that enables anonymous online communication. It works by routing internet traffic through a network of servers operated by volunteers worldwide, making it difficult to trace the origin of the communication.
The TOR network was initially developed for the US Navy to protect government communications. Still, it has since been adopted by a wide range of users, including journalists, activists, and whistleblowers, who need to communicate and access information anonymously and securely.
How it became a go-to hub for cybercriminals?
The cybercrime community quickly discovered the benefits of anonymous communication and how to remain hidden from search engines. This environment enabled operating in the shadows for over two decades and running cybercrime forums and black markets.
- Cybercrime forums are online discussion boards where cybercriminals can communicate and collaborate. They can exchange tips, tricks, and advice on hacking and even pool their resources to carry out more complex cyber-attacks. Some forums may require membership or an invitation, while others are open to anyone.
- Black markets are online marketplaces where cybercriminals can buy and sell illegal goods and services. Transactions are often conducted using cryptocurrencies, which makes it difficult to trace the transactions and the identity of the buyers and sellers.
However, the Guardz CIR team noticed that, over the last few years, instead of remaining in the deepest and the darkest corners of the internet – the cybercrime community has rapidly opened up to new candidates and has a firm trend of democratization.
The Guardz CIR team discovered a site aggregating hundreds of links to cybercrime forums and black markets. Now guess what – it’s accessible and can be found using a Google search!
When the information is so easily organized and accessible, it enables a freshly baked malicious actor to find and join a relevant community easily.
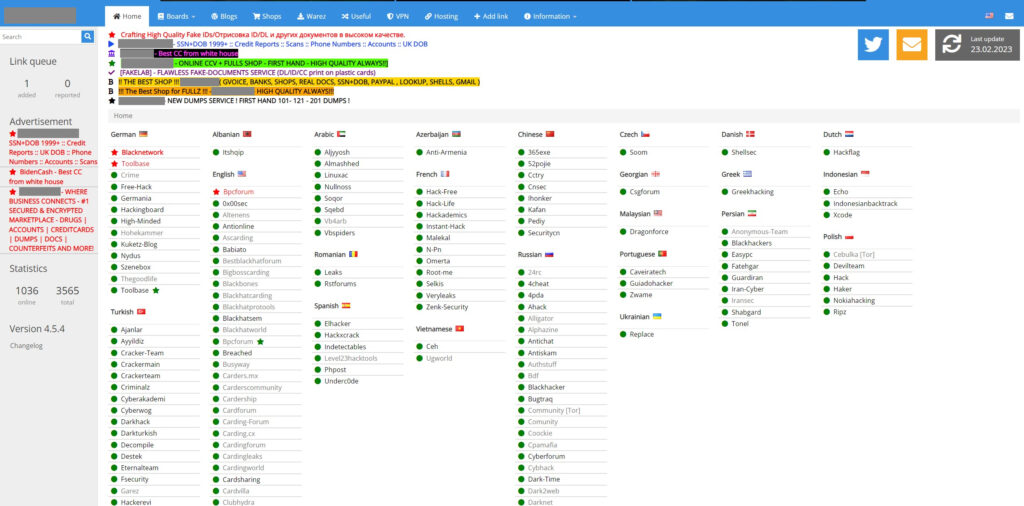
Overview of cybercrime forums
We drilled down on this topic and researched several cybercrime forums from the above-mentioned site.
To emphasize the democratization process, we checked the number of people that participate and are involved in cybercrime activity. The facts are worrying:
- The forum opened only in the middle of 2022, already attracted over 325,000 users, and started over 43,000 unique threads.

- Another forum that has been active since 2015 has reached over 4.7 million users, with a record of over 63,000 users being simultaneously connected.

Another interesting fact is that every forum has its own expertise. For example, the Guardz CIR team sees that one source strongly focuses on leaking and selling compromised databases while another forum acts as a point for acquiring offensive cyber tools.
Cybercrime 101
In 2023, you no longer need to be a high-profile hacker that knows how to execute a successful attack from A to Z. A variety of cybercrime tools and services can be obtained freely, purchased, or outsourced to third parties.
The Guardz CIR team simulated a situation when a rookie threat actor is willing to initiate cyber attacks using a “spray and pray” technique.
After passing a short and free registration process in one of the forums, the threat actor receives access to a feed with freshly compromised databases.
According to our research, at least 50% of companies in this feed are small and medium enterprises worldwide.
In our use case, we found and obtained a new database related to a US-based tech education company that was targeted in an unknown cyber incident, resulting in a leak of almost one million records, including personally identifiable information (full names, date of birth, and email addresses) and clear text passwords.
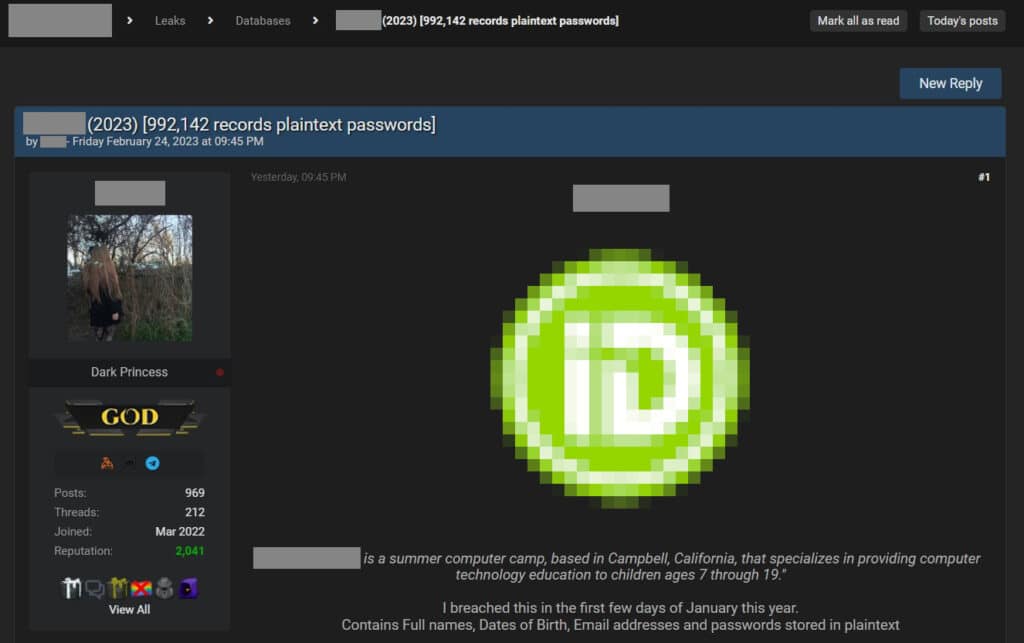
The database was dumped on 24 February 2023 and is available for download. The Guardz CIR team sifted through the data and discovered several education institutions and other small and medium enterprises (excluding SAP) that used their corporate email addresses to create a user. They now have sensitive information exposed, including clear text passwords. The recent user login dates verify that the data is fresh.
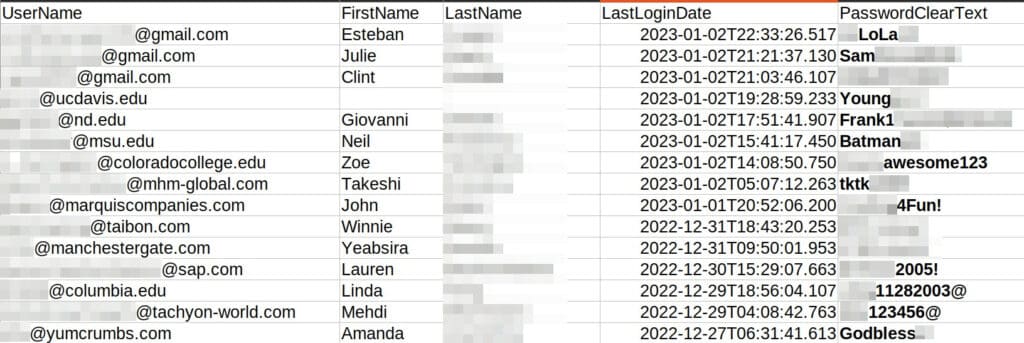
Unfortunately, it’s only the beginning of endless options open to a cybercriminal.
While jumping to another forum, the threat actor can find a tool that will be able to load a combination of mentioned above email addresses and passwords and conduct a fully automated check if those credentials also fit PayPal accounts. In the case of a match, the threat actor can take control of the account and withdraw the money.

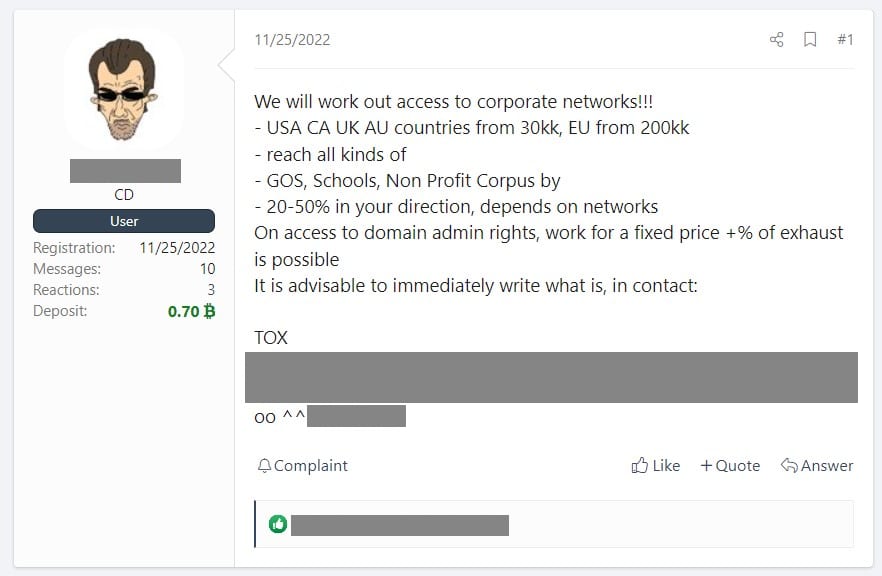
In an even more egregious case, the threat actor can match a compromised password to the corporate email address and try to log in to the business email on behalf of the employee.
In the case of a successful login but a lack of technological knowledge on how to continue from that point, threat actors can simply re-sell access to more advanced malicious actors typically found in the Russian cybercrime scene.
However, the companies can protect themselves by implementing 2FA (two-factor authentication) as part of the login process, and utilize Guardz to detect if there is or isn’t a 2FA on an account. This step can significantly enhance security and reduce the risk of unauthorized access.
The Guardz CIR team recommends using a trusted 2FA method, such as SMS, authenticator apps, or hardware tokens.
Stay tuned
Stay tuned for more upcoming blogs where we will be covering topics like additional threats from third-party data breaches, why ransomware continues to be a major issue, an overview of the black market that targets small and medium enterprises, the human factor in successful cyberattacks, and more.
Summary
Small and medium enterprises may not have the same resources as large corporations to invest in cybersecurity, but they are just as vulnerable to cyber threats. Small and medium enterprises are often seen as low-hanging fruit for cybercriminals who know these companies may have weaker security measures.
The consequences of a cyber attack can be devastating for small and medium enterprises, including financial losses, damage to reputation, and loss of customer trust. In addition, Small and medium enterprises may also face legal and regulatory consequences if they fail to protect sensitive customer data.
Investing in cybersecurity doesn’t have to be a daunting task. Guardz offers an all-in-one cyber solution for only $9/month.
In short, businesses cannot afford to ignore cybersecurity. It’s essential to take proactive steps to protect against cyber threats and ensure the long-term success of the business.
- Share On:












