Are you unfamiliar with malware-related terms like Keylogger, RAT (Remote Access Tool), Trojan, Worm, and Botnet? Or are you part of an MSP team seeking to expand your knowledge in this area? This blog will provide actionable tips on maintaining safety in the digital world.
From ransomware to information stealers and beyond, malicious software has the potential to wreak havoc on systems, compromise sensitive information, and disrupt operations. In this blog, the Guardz Cyber Intelligence Research (CIR) team will delve into one of the most popular types of malware, examining its various forms and discussing the latest trends in cyber threats.
Join us as we unravel the complexities of malware and equip you with the knowledge and tools needed to defend against these pervasive digital adversaries. Along the way, we’ll also explore the direct connection between the Dark Web and information-stealing attacks.
What is an Information Stealer Exactly?
Information stealers are a type of malicious software designed to secretly collect sensitive information from compromised systems. This category of malware is specifically engineered to target and steal valuable data, including login credentials, financial information such as credit card details, personal identification specifics, and other confidential data like cryptocurrency wallet seed phrases.
Some of the most prevalent names in this malware category include Redline, Vidar, and Racoon. However, emerging information stealers like Silencer, Lumma, and Rhadamanthys are quickly gaining traction and are on the path to joining the leaders mentioned above.
Information stealers cannot be executed remotely, meaning that the individual using the workstation is the one who clicks on the malicious item and initiates the infection chain. Threat actors often use social engineering techniques, which we covered in one of our previous blogs, to combine stealers with pirated software (such as cracked games, serial key generators, or mainstream programs like cracked Photoshop), email attachments, compromised websites, or even malicious ads on search engines promoting fake software like “all-in-one virus cleaning tools.”
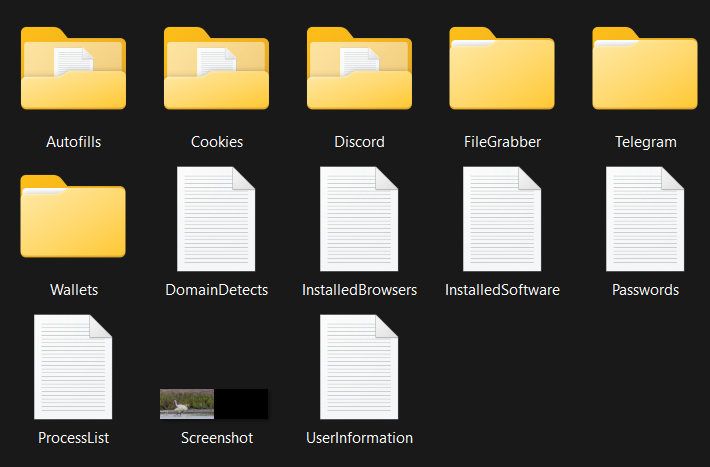
Once installed on a victim’s system, an information stealer may employ various techniques to gather sensitive data, including keystroke logging, clipboard monitoring, capturing screenshots, grabbing files from specific paths, or extracting data from web browsers and email clients. The stolen information is then typically transmitted back to the attacker’s command-and-control server or stored locally for later retrieval.
The stolen data can be used by cybercriminals for a variety of malicious purposes. For example, the threat actor can invest time to search the harvested data for sensitive compromised credentials to the company’s remote access (like VPN or RDP) and then re-sell the access on the underground forums.
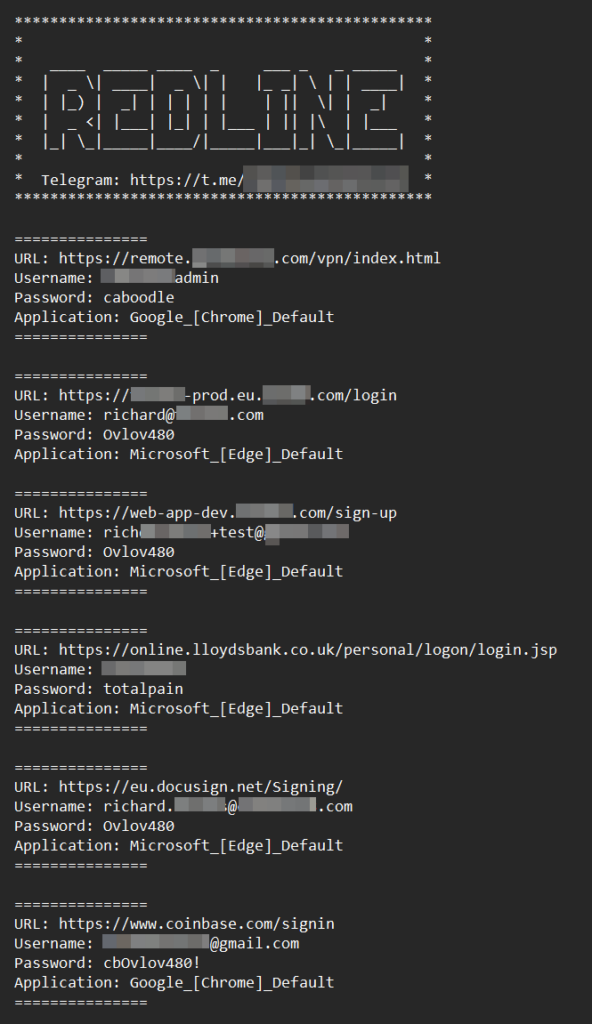
In the example below, the Guardz researcher analyzed one of the Redline logs from a UK-based infected computer. Unfortunately, this is also an example of mixing work and personal life on the same device.
The information stealer managed to exfiltrate not only the credentials for a remote VPN connection to the victim’s workplace (which is an SME) but also compromised access to the production and development environments of other companies.
From a personal perspective, the victim’s bank account and cryptocurrency wallet login details are now in the hands of cybercriminals. The full version of the log contained much more sensitive data, but the Guardz team has censored those details for obvious reasons.
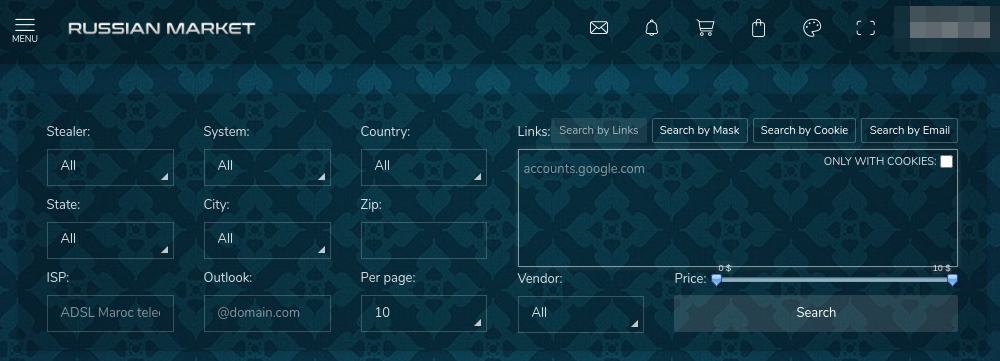
However, searching for valuable credentials can be a time-consuming endeavor, and the majority of cybercriminals prefer the more popular method of monetization – selling large quantities of digital identities to illicit platforms like the “Russian Market.”
Such underground markets resell the data as separate items and offer options for customized searches. As a result, if an attacker aims to target a specific domain or service, they can easily find exactly what they need.
Information Stealer Data Compromise vs. Third-Party Breach Leakage
There is one crucial distinction that every cybersecurity specialist needs to understand. When we use our corporate credentials to register for a third-party service, in the event of a data breach, the single set of compromised data that cybercriminals can potentially exploit is the information provided to that specific service.
While this is still an unpleasant cyber incident, it is essential for every MSP provider to monitor such occurrences and deliver actionable intelligence to their clients as promptly as possible.
However, if you store all your passwords within your browser and your device gets infected by an information-stealing attack, all stored passwords are directly transmitted to malicious actors. Consequently, you turn your personal device into a stand-alone data breach.
In the event of a credentials leak from a third-party source, modern cybersecurity regulations mandate the storage of all passwords in an encrypted format. Although this is a commendable practice, weak passwords like “123456” can still be easily decrypted, even if they are stored in a hashed version.
For instance, decrypting the password “123456”, stored as an SHA256 hash (8d969eef6ecad3c29a3a629280e686cf0c3f5d5a86aff3ca12020c923adc6c92), took a Guardz researcher just a few seconds.
In the case of information-stealing malware, even the decryption step becomes irrelevant. The stealer manages to exfiltrate all stored browser passwords in clear text, bypassing encryption entirely.
The Threat Evolution
Originally, information stealers had basic technical capabilities. However, due to high demand from the cybercrime community, these malware families rapidly advanced their attack options.
The primary reason for the popularity of this malware type is that it is often offered on a subscription basis, with malware developers providing continuous product improvement and support. Furthermore, other threat actors in the underground community also offer managed services for malware distribution.
These facts emphasize the growing trend that modern cyberattacks are likely a combination of several outsourcing services. Guradz CIR discussed the rise of “Attack as a Service” in our first Dark Web blog.
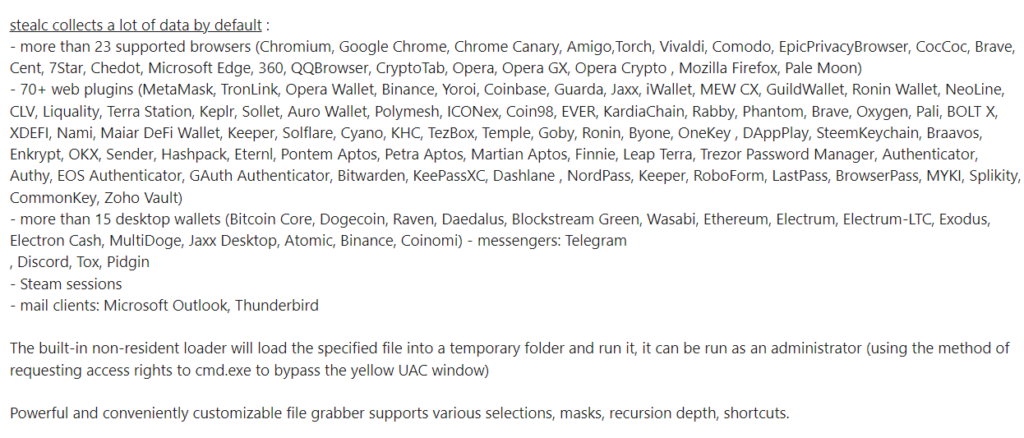
We analyzed the capabilities of the StealC stealer, first introduced to the underground community in early 2023, and discovered that it supports credentials exfiltration from over 20+ browsers, data grabbing from over 70+ browser plug-ins (mostly crypto-oriented), and targeting common email clients like Outlook.
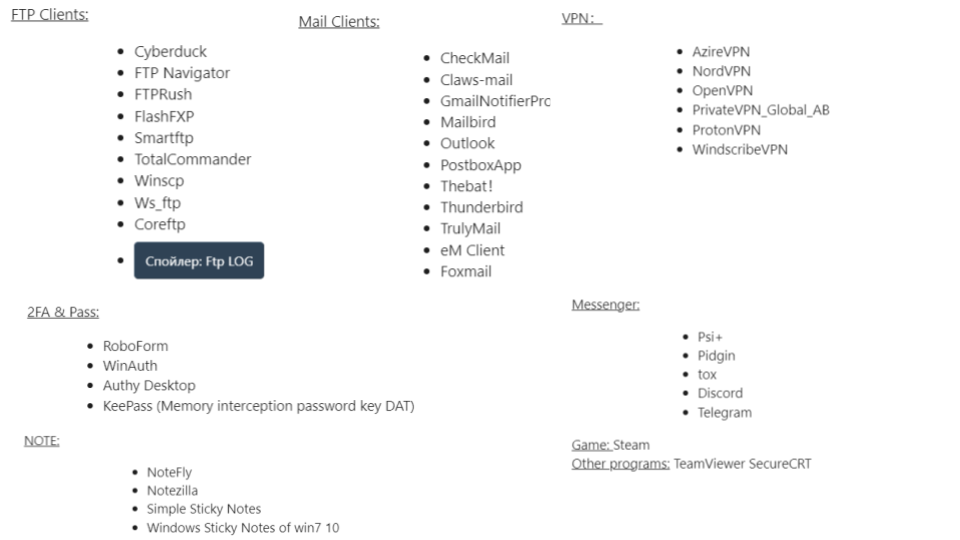
A more advanced stealer, Rhadamanthys, active since Q3 2022 – has the additional functionality of grabbing data related to FTP clients, more email clients, and VPNs.
Emerging MacOS Threat
Guardz researchers have been continuously tracking the information-stealer landscape, and until recently, the trend had been quite stable – this type of malware predominantly targeted Windows-based devices.
The rationale behind this is quite simple – Microsoft Windows remains the most widely used operating system globally. From a threat actor’s perspective, scale is paramount, and developing dedicated malware to infect Linux devices, for example, is a less scalable solution.
Our team examined statistics from the notorious “Russian Market” to validate our hypothesis. Indeed, 100% of the top five operating systems hit by information stealers and now offered for sale are Windows-based.
| OS name | Compromised identities |
| Windows 10 Pro | Over 2.8 million |
| Windows 10 Enterprise | 900.000 |
| Windows 10 Home | Over 2.2 million |
| Windows 7 | 221.000 |
| Windows Server | 10.000 |
However, Guardz CIR has discovered that this status quo will likely change soon.
MacOS-based devices, which are highly popular in the US, have begun to appear on cybercriminals’ radar, and we are already seeing the shift on underground forums.
In May 2023, the emerging information stealer “Atomic,” which exclusively targets MacOS devices, was released and offered for rent as a service for $1000/month. Later in June, the threat actor also announced they were seeking to buy a 0-day/1-day exploit for MacOS.
In June 2023, merely a month later, another emerging information stealer, “ShadowVault,” began offering its infection services for rent at $500/month.
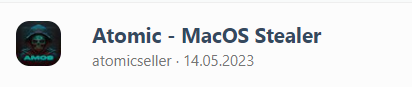
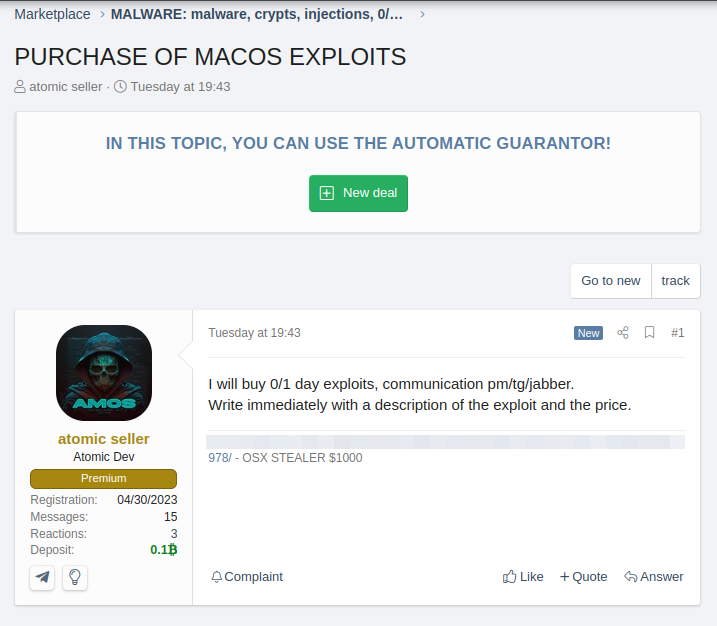

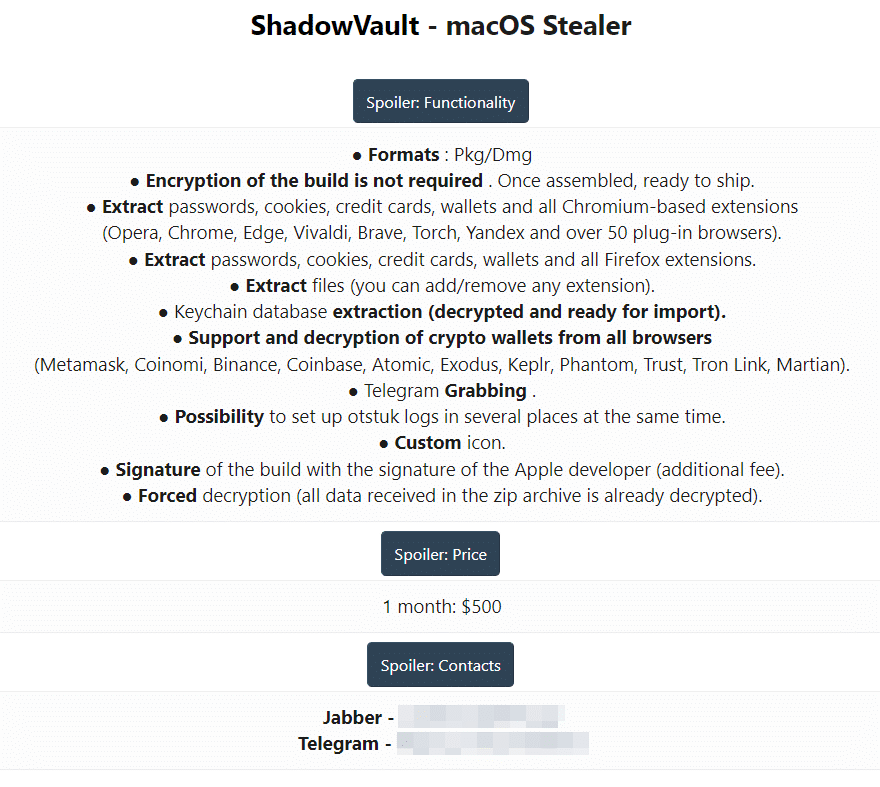
And recently, on 9 June 2023, a Russian-speaking threat actor offered to pay $50,000 to develop a new MacOS stealer.
Looking to boost your MSP revenue? Guardz got your back!
Tips on How to Prevent this Attack with Guardz
To protect against information-stealing malware, it is crucial to regularly apply security patches to operating systems and software, exercise caution when opening email attachments or downloading files from unknown sources, and enable two-factor authentication. Guardz continuously monitors your digital assets from the inside out, securing your user’s data, email, devices, external exposure, cloud apps, employee awareness, browsers, and more.
However, Guardz firmly believes that user education and awareness regarding safe online practices are vital in mitigating the risk of information-stealing malware infections.
Summary
Guardz empowers MSPs with the tools to secure and insure SMEs against ever-evolving threats such as phishing, ransomware attacks, data loss, and user risks by leveraging AI and a multilayered approach.
- Share On: